Penetration Testing: Everything You Need To Know
In this post, we will explore everything you need to know about penetration testing (pentesting). Let’s dig in:
What Is Penetration Testing?
Although penetration testing can be done manually, automated software is sometimes used to systematically compromise wireless network, servers, network devices, web applications, mobile devices, endpoints and other potential exposure points.
The primary objective of penetration testing is to identify security weaknesses in IT infrastructure. Penetration testing can also be used to test an organisation’s security policy, its ability to identify and respond to security incidents and its employees’ security awareness. Penetration testing is also known as pentesting or ethical hacking. It is also sometimes referred to as a white hat attack.
Financial service organisations and tech companies commonly conduct pentesting, but all organisations can significantly benefit from this type of evaluation.
Why Is Penetration Testing Important?
It reveals vulnerabilities
Penetration testing evaluates the existing vulnerabilities in your network infrastructure or application system configurations. Your employees’ habits and daily actions that could lead to malicious infiltration and data breaches are also under scrutiny during a pentest. Once the testing is over, you receive a report informing you of all the weaknesses found and the software and hardware improvements you should consider. You also get recommendations on policies that would boost the overall security.
It reveals real risks
Pentesters try to exploit the identified weaknesses. This gives you a chance to see what a black hat hacker could do in the real world. This helps you to prioritise real-world risks so you can focus on the weaknesses that really matter rather than theoretical ones.
It tests the capability of your cyber defense
Your organisation should be quick to detect and respond to attacks. You should detect intrusions in time, launch investigations promptly, discover the intruders and block them. This should be the case, whether it is a malicious actor or an expert testing your protection strategy’s effectiveness.
The feedback you receive from the pentest will let you know how you can improve your defense.
Ensures business continuity
For your business operations to be running all the time, you need access to resources, 24/7 communications and network availability. Disruptions to these necessities will have a negative impact on your business.
A pentest is similar to a business continuity audit, in that it identifies potential threats that would lead to unexpected downtimes or a loss of accessibility. Addressing these threats will ensure your business continues to run without interruptions.
Helps MEET compliance REQUIREMENTS and certifications
Your organisation might be operating in an industry with legal requirements that dictate a certain level of penetration testing. For example, the ISO 27001 standard and the PCI regulations require all system owners and managers to conduct regular security reviews and pentests with skilled testers.
Helps you maintain trust
Data breaches and cyber attacks affect the loyalty and confidence of your customers negatively. However, if your organisation is known to conduct strict and systematic reviews and penetration tests, this will assure your shareholders.
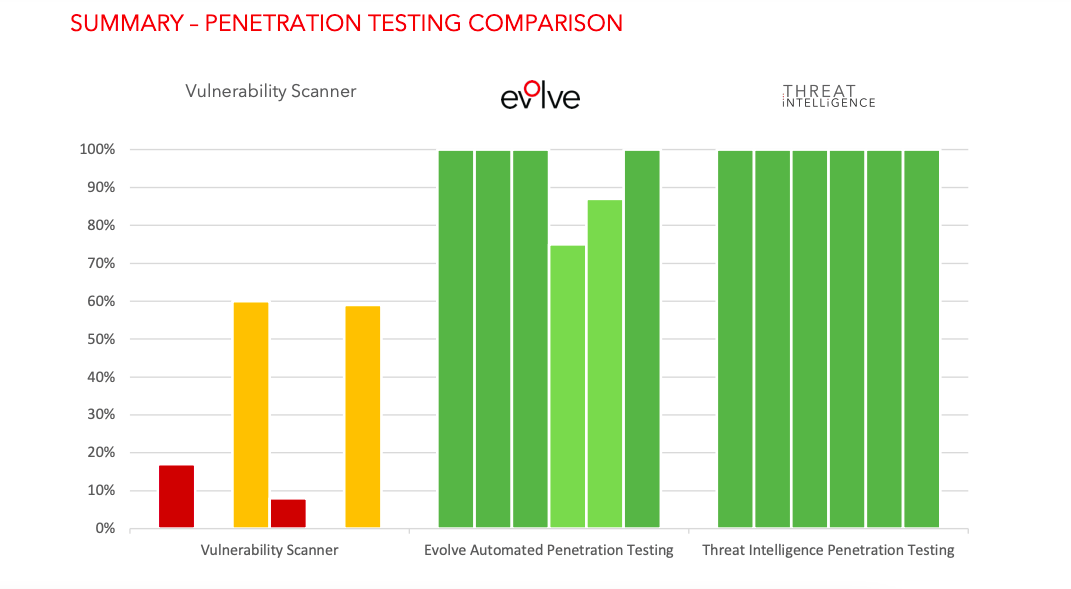
What Is The Difference Between Vulnerability Scans And pentests?
While vulnerability scans give you a picture of the security weaknesses present, a penetration test adds additional context by finding out if it’s possible to leverage the vulnerabilities to gain access to your environment. Penetration testing also helps in prioritising recommendation plans based on the threat that poses the highest risk .
Penetration Testing Tutorial
Before we look at the steps or stages of penetration testing, let’s determine who conducts pentesting.
Who Performs Penetration Tests?
For a complex pentest that requires going deep into different applications and systems, you need an expert pentester or a group of them. To sufficiently test a realistic attack scenario, you will need a red team that employs complex strategies and solutions similar to what real threat actors would use.
For less demanding tests, you can create a robust pentesting program by using readily-available resources. Even if you don’t have extensive pentesting knowledge, you can use automated testing tools to run simple tests that are easy to run but vital to perform regularly. Such tests include validating vulnerability scans, privilege escalation, network information gathering and phishing simulations.
What Are The Stages Of pentesting?
Penetration testing can help you proactively identify the most exploitable security vulnerability before a malicious actor does. However, the process involves much more than infiltration. Penetration testing is a thorough, well thought out process made up of the following phases:
PLANNING AND PREPARATION: For the pen test to go well, you and your testers need to be on the same page on the test’s goals. Your testers need to know some of the tests they should run, who are aware that the tests are being run and how much information you will provide them with.
DISCOVERY: This phase is where testers perform reconnaissance on their target, gathering data such as names, job titles, email addresses and IP addresses.
PENETRATION ATTEMPT AND EXPLOITATION: Now that the pen testers have enough data on their target, they attempt to infiltrate the environment and exploit the weaknesses they discover.
ANALYSIS AND REPORTING: Pen testers create a report that details the entire pen testing procedure, the tools used, the weaknesses found and recommendations to remedy them.
TIDYING UP YOUR ENVIRONMENT: A thorough clean-up of the IT environment is done once the penetration test is completed. The pen testing team removes any files, accounts, or software that were used solely for the purpose of testing. In addition, firewall and system configurations are reverted to the original state.
REMEDIATING THE VULNERABILITIES: The remediation process lets you utilize the findings from the test report, prioritize the vulnerabilities in your system based on their criticality and remediate them to prevent potential attacks in the future. Some of the issues can even be resolved with a quick fix that does not require significant time, effort, or costs.
RETEST: The best way to be sure that the recommendations you implemented were effective is to test again. Quite often, as methods used to attack IT environments are always evolving, this may uncover new weaknesses.
How Often Should You pentest?
There is no one-size-fits-all when it comes to pentesting. The following factors affect how often an organisation should pentest:
- The size of the company – If you run an organisation with a large online presence, you have more attack vectors and are therefore more attractive to hackers, so you should test often.
- Budget – Large businesses can afford an annual pentest while a smaller one can only conduct a pentest once every two years.
- Regulations – organisations in some industries are required to perform specific security checks, including penetration testing.
That being said, you should aim at conducting a pentest once a year to ensure more consistent IT and network security management. In addition to your yearly analysis and assessment, you must also conduct a pentest when you:
- Add new network applications or infrastructure
- Establish offices in a new location
- Modify your end-user policies
- Make substantial upgrades to your infrastructure and applications
COMMON PEN TEST STRATEGIES
BLIND PEN TEST
DOUBLE BLIND PEN TEST
EXTERNAL PEN TEST
INTERNAL PEN TEST
TARGETED PEN TEST
Types of Penetration Testing
When conducting a pentest, it can be tempting to ask the pentesters to do a general test where they “test everything” however, with this approach, pentesters will end up only scratching the surface of several vulnerabilities. Therefore, they would miss out on the valuable intelligence they would gather if they took a more in-depth approach by concentrating on a few areas. To ensure pentests are effective, there are several types of pentests that focus on specific areas of an IT infrastructure. They include:
NETWORK PENETRATION TESTING
This is the most common type of pentest. Network service penetration testing aims to discover gaps and weaknesses in your organisation’s network infrastructure.
When conducting this type of pentest, an ethical hacker will run tests locally at the site and remotely from the outside. The tester will focus on targeting the following network areas:
- IPS deception
- Firewall configuration testing
- DNS level attacks
- Stateful analysis testing
Network service penetration testing helps you protect your organisation from the following network-based attacks.
- DNS level attacks
- IPS/IDs evasion attacks
- SSIT attacks
- Router attacks
- Unnecessary open ports attacks
- Man in the middle attacks
- Proxy server attacks
- Database attacks
WEB APPLICATION PENETRATION TESTING
Web application penetration testing is a more detailed pentest used to discover weaknesses in web-based applications. The scope of this pentest includes browsers and web-based applications and components such as Applets, ActiveX, Scriptlets, plugins and Silverlight.
Because of the increase in threats and complex nature of web applications, penetration testing generally requires more time to plan and execute, as techniques are continually evolving.
One of the main reasons you should conduct this type of pentesting is to expose security vulnerabilities within your web-based applications and their components, including back-end networks, databases and underlying code.
This type of pentest also helps in prioritising determined vulnerabilities and provides solutions that might help mitigate them.
Client-Side Penetration Testing
This type of penetration testing is used to expose security vulnerabilities in client-side applications. Apps like program applications – such as web browsers, Putty, Macromedia flash, email clients, Microsoft Office Suite and Adobe Photoshop.
Client-side penetration testing is valuable in identifying attacks such as:
- Cross-site scripting attacks
- Cross-origin resource sharing
- HTML injection
- Malware infection
- Clickjacking attacks
- Form hijacking
- Open redirection
Wireless Penetration Testing
Wireless penetration testing aims to find out and evaluate connections between all the devices connected to your organisation’s Wi-Fi. All IoT devices, laptops, smartphones and tablets are examined.
Pentesters usually conduct wireless penetration testing on-site because they need to be in the range of the wireless signal to access it. However, where necessary, they can also deploy a device to carry this out remotely. Because wireless networks allow data to flow in and out of your organisation, you should conduct wireless penetration testing to prevent data leakages and unauthorised access. Before you conduct wireless pentesting, please consider the following.
- Have you identified all access points and noted the ones with inferior encryption methods?
- Do you have monitoring systems to identify unauthorised users?
- Is all the data flowing in and out of your network encrypted?
- What measures are you currently taking to protect your wireless network?
- Is it possible that your IT team may have duplicated or misconfigured a wireless network?
- Are all your wireless access points using WAP protocol?
Social Engineering Penetration Testing
In a social engineering penetration test, a pentester attempts to persuade users to give their sensitive information, such as their passwords and usernames. Some of the common attacks pentesters use include:
- Phishing attacks
- Smishing (using SMS)
- Imposters
- Vishing (using Voice)
- Pre-testing
- Tailgating
- Namedropping
- Dumpster diving
- Gifts
- Eavesdropping
Social engineering penetration testing is a vital part of pentesting. This is because social engineering scams are very lucrative and internal users are the biggest threats to your network’s security. In fact, recent statistics show that 98% of cyber attacks rely on social engineering.
Physical Penetration Testing
In physical penetration testing, a pentester simulates a real-world threat by attempting to compromise physical barriers to access a business’s infrastructure, employees or systems.
Physical penetration testing is essential because most businesses treat physical barriers as an afterthought, but a malicious actor could cause severe damage if they can access your server room.
Physical penetration testing is useful to expose vulnerabilities in controls such as cameras, locks, sensors and barriers.
Penetration Testing Software
Different penetration testing targets require different software, such as those used for port scanning, Wi-Fi break-ins, application scanning and direct penetration of the network. The types of pentesting tools fall into five broad categories:
- Reconnaissance tools that help testers discover network hosts and open port
- Vulnerability scanners that help discover issues in the network services APIs and web applications
- Proxy tools
- Exploitation tools that help in accessing assets
- Post-exploitation tools for integrating with systems and maintaining access.
Penetration tools and software should have the following characteristics:
- They should be easy to configure, deploy and use
- Should automate the verification of vulnerabilities
- Generate detailed vulnerability logs and reports
- Categorize vulnerabilities based on their severity
- They should reevaluate previous exploits
Most of the popular penetration tools are open source or free to use. Open source tools give pentesters the freedom to modify and adapt the code for their specific needs. Some of the most commonly used penetration testing software includes:
Nmap
Nmap, short for Network Mapper, is a pen tool that scans networks and systems for weaknesses linked to open ports. This tool is directed to the IP address of the system to be scanned and it tests the system for open ports. Nmap can also be used to monitor host or service uptime and map networks attack surfaces.
Wireshark
This is a valuable tool for analyzing network traffic and packets. It allows organisations to see the minute details of what is taking place on their networks in real-time.
John the ripper
This tool contains several password crackers in one package. It automatically identifies different types of password hashes and decides on a customizable cracker. John the reaper is commonly used to launch attacks to discover password weaknesses in databases and systems.
Metasploit
Metasploit
is a widely used penetration testing tool that has made hacking easier than before by automating previously repetitive tasks. Its website boasts that it is “world’s most used penetration testing framework”. It is an open-source tool that lets you breach and enter a system by passing a code and then run a payload on accessing the system.
Penetration testers use the same tools that black hat hackers use. This is because these tools are already readily available, well documented and it gives pentesters a better understanding of how these tools can be used against their organisations.

AUTOMATED PENETRATION TESTING
Although they are much faster, automated testing can give false positives and lack the depth that manual testing has. Also, automated testing solutions follow a scripted routine – unlike human pentesters who think and act like cybercriminals while analysing data and simulating attacks.
WHAT HAPPENS AFTER A PEN TEST?
Fortifying your security posture is a continuous and ever-evolving process, given the nature and complexity of today’s threats. Repeat the penetration testing process at regular intervals as a part of your organization’s overall risk assessment and cybersecurity strategy.