It is undeniable that organizations require robust security measures against cyber threats. A cyber-breach can result in huge expenses to your organization. So what can we do to help prevent these breaches? This is the purpose of a strong security architecture that can reduce these cyber security threats and the expenses that might result from them.
A security architecture is a set of models, methods, and security principles that align with your objectives, keeping your organization safe from cyber threats. Through security architecture, a business’ requirements are translated to executable security requirements. Just like architecture in construction where there is an examination of the property in such factors as climate, soil type, topography, and client preference, so must a security architect understand the network, firewalls, defences, detection systems, and many other factors.
TYPES OF SECURITY SERVICES
The fundamental goal of security architecture is to protect your organization from cyber threats. But what are these threats?
Sensitive company data is continuously under threat of attack, whether through malicious actors, malware, or human error. Cyber threats come in all shapes and sizes, from denial of service attacks to data theft and financial fraud. Malware such as viruses, worms, and Trojans can wreak havoc with a company’s networks and infrastructure, while ransomware can hold an organization’s data hostage until a ransom is paid. In addition to these outside threats, businesses also need to be aware of insider threats that can result in data theft, data loss, and even destruction of the business.
The CIA triad is the backbone of every security architecture. It stands for Confidentiality, Integrity, and Availability, which are three key principles for any security system. Confidentiality ensures that only authorized users have access to sensitive data. Integrity ensures that data is not modified without authorization. And lastly, availability is about making sure that and systems are available when needed. As a result, information must be protected from unauthorized access, usage, modification, disclosure, and destruction.
The OSI security architecture is an internationally accepted standard and a structured approach to information security. It outlines certain security services that need to be in place to secure data as it moves across a network.
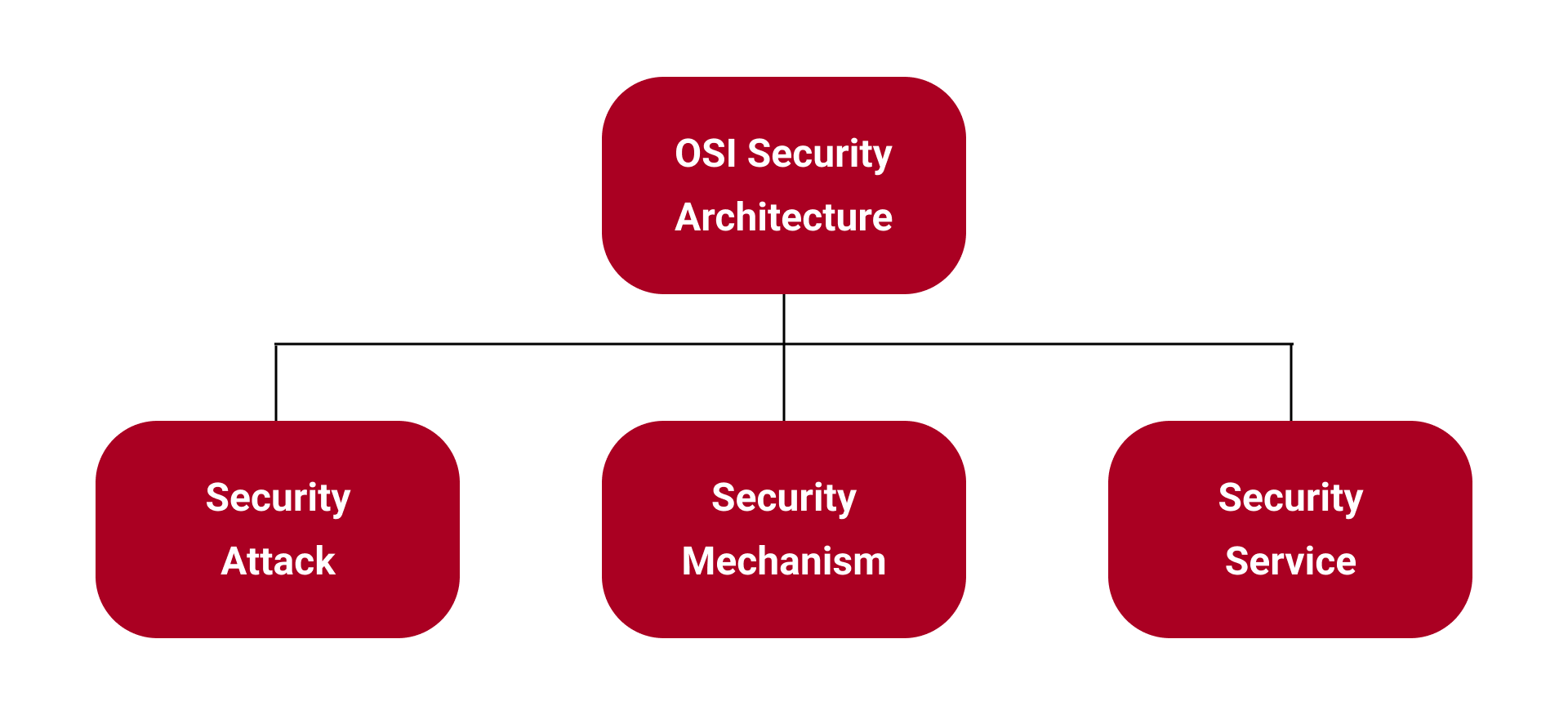
A security service is processing or communication service that improves the security of the data processing systems by protecting the flow of information. These services include authentication, access control, data confidentiality, data integrity, nonrepudiation, and availability.
- Authentication verifies that the user attempting to access a system is who he claims to be. This may be accomplished through a combination of passwords, usernames, tokens, biometrics, and so on.
- Access control restricts access to a system or information to authorized individuals. It may be based on user credentials, user location, user roles, or other criteria.
- Data confidentiality maintains the privacy of information while it is being transmitted. This is usually accomplished by encryption, using secure file-sharing software, implementing confidentiality policies and/or more.
- Data integrity ensures that data are not altered or modified in transit or storage. Additionally, it ensures that the the data received by the receiver is from a trusted source.
- Non-repudiation prevents users from denying that they sent or received a specific message.
The above-mentioned services are critical to ensure the confidentiality, integrity, and accessibility of important enterprise data.
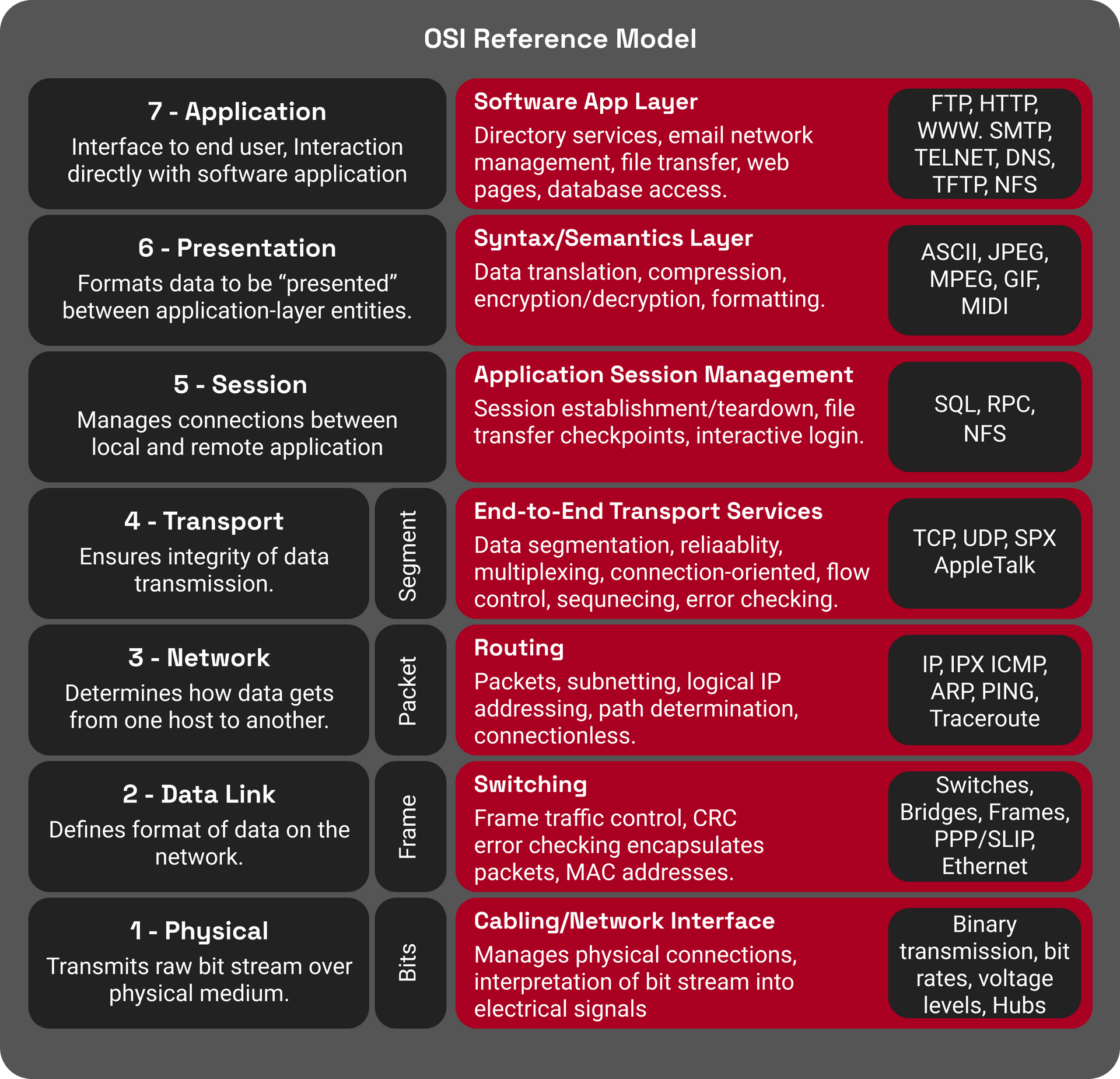
Security Architecture Frameworks Examples
Security architects have guidelines (frameworks) to work with. A security architecture framework is a set of consistent guidelines and principles for implementing different levels of business’ security architecture. Companies may opt to devise their frameworks by combining international standard frameworks, such as:
- TOGAF
- SABSA
- OSA
TOGAF Framework
TOGAF, or The Open Group Architecture Framework, helps determine which problems need to be solved within the security infrastructure in a business. Its primary focus is on the organization’s goal and scope, as well as the preliminary phases of security architecture. TOGAF does not, however, give specific guidance on ways to address security issues.
SABSA Framework
SABSA, or the Sherwood Applied Business Security Architecture, is a policy-driven framework. It helps define the critical questions that security architecture can only answer: what, why, when, and who. The goal of SABSA is to ensure that after the design of security services, they are then delivered and supported as an integral part of the enterprise’s IT management. One downside, however, is that SABSA doesn’t get into specifics regarding technical implementation.
OSA Framework
On the other hand, the Open Security Architecture (OSA) is a framework related to technical and functional security controls. OSA offers a comprehensive overview of crucial security components, principles, issues, and concepts that underlie architectural decisions involved in designing effective security architectures. However, OSA can only be used if the security architecture has already been designed.
CLOUD SECURITY ARCHITECTURE
Data stored in the cloud also needs protection from unauthorized access, malicious attacks, and other potential threats. Cloud security architecture is the combination of strategies, policies, and controls used to protect the cloud-based data that organizations store and process. This includes the physical, network, and host security controls for data in the cloud.
Cloud security architecture is a critical component of any expanding business because of the increasing dependence on cloud computing for data storage and processing.
Cloud service models are classified into three major categories: Software as a Service (SaaS), Platform as a Service (PaaS), and Infrastructure as a Service (IaaS). Each of these service models has unique security requirements that can be addressed by different security architectures. In this section, we're exploring two of the most popular cloud security architectures: Amazon Web Services (AWS) and Microsoft Azure.
When it comes to cloud security, both AWS and Azure have a wide range of built-in security features and tools to help you secure your cloud data. Both of them follow a shared responsibility model where the responsibility for security is divided between the cloud provider and the cloud customer. They also offer built-in compliance tools that can audit your cloud resources and recommend appropriate security best practices to help you secure your data and meet your compliance requirements. Compliance solutions on both platforms support the majority of the major compliance standards including ISO 27001, PCI, DSS, and many others.
Both AWS and Azure also provide Identity and Access Management (IAM) services, encryption in transit and at rest, and firewall rules, and VPN services. In addition to these built-in security features, each cloud platform also includes a marketplace where users can purchase third-party vendor applications to satisfy specific security needs.
For a detailed view of how you can secure your cloud resources using AWS and Azure, check out our blog posts on the same -
8 AWS Cloud Security Best Practices You Need to Know,
and
Improve Azure Security With These Tips and Tricks.
ENTERPRISE INFORMATION SECURITY ARCHITECTURE
Enterprise Information Security Architecture (EISA) is the framework for planning and implementing security measures for enterprise data. It provides the basis for understanding the information security goals of the organization and ensures that the right controls are in place to meet those goals. It also provides a systematic approach to managing and assessing risk, as well as a framework for designing, implementing, and maintaining information security solutions. Enterprise Information Security Architecture is an approach to security that is based on best practices and includes both technical and non-technical controls. It represents how information security is practiced within the organization and provides the basis for information security policies and procedures.
While EISA is a comprehensive approach to information security, it is more broadly concerned with optimizing business security. Many businesses find it difficult to balance security and business needs, but EISA aims to provide a framework that can be used to achieve this balance.
Benefits of Security Architecture
Strong security architecture leads to fewer security breaches
With modern technology, an organization is required to have a security architecture framework to protect vital information. This drastically reduces the threats associated with an attacker successfully breaching an organization’s systems. Among the many benefits of security architecture is that it can translate each unique requirement into executable strategies and develop a risk-free environment for a business while aligning with the latest security standards and business needs.
Of course, the “holy grail” is that security architecture helps organisations demonstrate their integrity and confidentiality to potential partners. A strong security architecture, first and foremost, upholds the three pillars of the CIA Triad: Confidentiality, Integrity, and Accessibility. In so doing, consumers and business partners will be much more likely to work with and trust an organization.
Proactive security measures save money
Mitigating cybersecurity threats is expensive. Some of the possible ramifications of security breaches can include the halt of production processes, product recalls, embarrassing press conferences and, as a result, damaged reputations and severe monetary loss. The cost of fixing an error when detected in the early coding stages can cost up to 300%.
However, if the same error is detected in the post-releases or the production stages, it costs up to 3,000% more. To avoid or reduce the chances of errors slipping through during product development, it is advisable to integrate security at each production level. All products should be developed within a security context, minimising zero-day attacks and rushed (therefore expensive) patches.
Mitigate disciplinary measures in the event of a breach
Although cyber breach legislation consequences differ around the globe, it is common knowledge that the more an organization tries to prevent risks and reduce vulnerabilities, the higher the chances of favourable outcomes in the event of an attack. Working within regulations can help prevent punitive measures, which will, of course, further damage a company’s reputation and finances. With the introduction of GDPR, regulations have gotten stricter, and businesses are working to keep their technology within these new regulations.
At the same time, technology is also advancing quickly, meaning that the legislative landscape is also working tirelessly to catch up with technology. In other words, both sides of the equation are constantly changing and tightening their regulations and practices.Therefore, as a business, having a robust security architecture and using the necessary processes and tools to integrate the development cycle to detect errors is the best way to comply with the relevant authorities and regulations, as well as further defend your company against cyber threats.
The Crucial Element Missing in Most Enterprises
We spoke to Sam Panicker, Technical GRC specialist at Threat Intelligence, to understand what enterprises need to keep in mind when it comes to security architecture.
According to Sam, a crucial component in a robust security architecture is an ISMS policy.
"What we tend to find is that most small to medium-sized businesses do not have an ISMS policy in place."
He says, "Whenever you're in trouble and an auditor comes in, the first thing they'll ask for is an ISMS policy."
What is an ISMS Policy?
An Information Security Management System (ISMS) Policy, as defined by IT Governance, USA, is "a framework of policies and procedures for systematically managing an organization's sensitive data."
It is a document that lists all the important data, and people in an organization, the roles and responsibilities of people, and the procedures to be followed to ensure the safety of sensitive data within the organization.
In addition to providing a framework for handling sensitive data, it also serves as a guideline for the organization when there is an incident.
However, this is not to be confused with an incident response plan. While an incident response plan is specific only to handling an incident, an ISMS policy is a document that lists out the framework to follow to ensure data security on a day-to-day basis.
"An ISMS policy is about your data, your valuables, and your organization." highlights Sam.
"Your valuables are your data, people, processes, technology, and other assets," he adds.
So an ISMS policy would cover everything from physical security to data security. For example, do your employees use company-owned and approved devices to work and access sensitive information? What are the important documents you have in the organization? How is your company structured? Do you have a risk register? Do you have physical security measures in place? What kind of security incidents have you had in the past? These are some of the questions that an ISMS policy would answer.
"We would recommend that anybody who is building a security architecture for their organization starts with an ISMS policy. It's very essential." reiterates Sam.
Conclusion
As we conclude, it is important to mention that these types of issues must be handled by a specialist. IT – specifically cyber security – is a sensitive field. Having an expert to walk you through this process is vital to ensure that your security is being handled correctly. Moving forward, well-planned and effective security architecture will greatly help in consistently managing risks by allowing departments to make quick and better decisions and leveraging industry best practices.