When it comes to cloud security, Amazon Web Services (AWS) is often considered the gold standard. With 33% of the market, AWS is the largest cloud provider in the world right now.
As Amazon’s public cloud grows in popularity, more and more businesses are looking to take advantage of its scalability and flexibility. However, as with any technology platform, there are security risks that need to be managed.
In this blog post, we will share 8 AWS cloud security best practices that will help you keep your data and applications safe in the cloud.
The Cloud and Your Data
Let’s face it, the cloud can be a scary place. A place where you can store your data, access it from anywhere, and even share it with others, all without having to worry about your files getting lost or corrupted. Surely, there must be a catch?
Well, cloud computing platforms are among some of the most targeted and vulnerable platforms in the cyber world. The number of businesses that have experienced at least one cloud data breach in the last year stands at a shocking
98%. One such example pertaining to AWS is the recent Facebook data breach that exposed the personal data of
540 million users in 2019.
But these risks aren’t going anywhere. Organizations use the cloud primarily to store sensitive data, including employee and customer information. This data is often critical to business operations and must be protected at all costs.
Introducing AWS and its Reputation for Cloud Security
Amazon Web Services (AWS) is a cloud computing platform that provides users with on-demand access to a variety of resources, including storage, compute power, and networking. AWS is known for its reliability and scalability, but it's also gained a reputation for security.
AWS provides a number of security features to help ensure the security of your data and applications in the cloud. Some of these features include: identity and access management, network and application security, continuous monitoring, and compliance.
AWS has a proven track record of delivering secure, reliable, and scalable services. It is known for its security because its infrastructure is designed and managed with the unique needs of large-scale cloud environments, security best practices and standards in mind. In addition, its security features are replicated across different services and data centers around the world. This makes it an ideal platform for businesses that want to take advantage of the benefits of cloud computing but also protect their data and applications from cyber threats.
Security Features of AWS
AWS and its partners offer a broad range of tools and features that are designed to help you secure your cloud environment. But, from S3 to EC2 and everything in between, these features can be hard to understand. Here’s a brief overview of some of these features:
Infrastructure Security
The security features of AWS allow you to have more privacy and control over your network access. These features include network firewalls that let you create private networks and control access to your applications, options for connectivity that allow you to establish private or dedicated connections from your office or on-premise environment, DDoS mitigation technologies that help protect your data from attacks, and data encryption that helps protect your data from unauthorized access.
Inventory and Configuration Monitoring
AWS offers deployment tools, inventory and configuration management tools, and template definition and management tools to help you move fast while also maintaining your security posture. For instance, AWS Config is a service that enables customers to collect information about their AWS resources. Using this information, customers can collect and compare current configurations against desired configurations. It also provides rules-based notifications to indicate when configurations drift outside of predefined thresholds and can automatically correct the drift.
Data Encryption
AWS lets you encrypt data at rest in the cloud. Amazon’s encryption features include: Amazon Elastic Block Storage (EBS), Amazon Simple Storage Service (S3), Amazon Redshift, Amazon ElastiCache, AWS Lambda, and Amazon SageMaker, and Amazon Relational Database Services (RDS). Among these, Amazon S3 is one of the top features that helps maintain security and privacy of your data in the cloud. It allows you to organize and manage your data in a secure, efficient, and cost-effective way. Data is stored as objects in “buckets” and each object can have up to five terabytes of data in it.
Identity and Access Control
A free feature of AWS, Identity and Access Management allows you to control who has access to your AWS resources and services. You can use IAM to define policies that control access to AWS resources and services and to specify access permissions. Resource access is denied by default and users can get access only after permission is granted in IAM. Another such feature is the AWS Single Sign-On (SSO) that allows you to centrally manage access and user permissions for all your accounts.
Monitoring and Logging
AWS detects threats by consistently monitoring network traffic and account activity in your cloud environment. It provides a range of tools that help you gain visibility into your account activity and security events. For example, CloudTrail allows you to see what resources were accessed, by whom, and when they were accessed. It provides detailed logs of all interactions across all AWS services on your account. Another monitoring and observability tool is Amazon CloudWatch. It provides a range of metrics and reports that help you monitor your applications, respond to performance changes, and optimize your resource utilization. CloudWatch gives you a complete picture of your operational health and enables you to discover insights, detect anomalies, and troubleshoot issues in your cloud environment.
AWS and Compliance
It is important to note that AWS has made
compliance controls a fundamental aspect of the service, as opposed to bolt-on solutions found elsewhere in the industry. AWS's approach is not only proven, but it enables continuous compliance controls across the entire AWS Cloud. AWS services are in compliance with GDPR and additionally SOC 1/SSAE 16/ISAE 3402 (formerly SAS 70), SOC 2, SOC 3, ISO 9001 / ISO 27001, FedRAMP, DoD SRG, and
PCI DSS Level 1 certifications are continuously audited in AWS computing environments. Amazon also has assurance programs that provide templates and control mappings for customers to achieve compliance in their AWS-hosted environments. Finally, resources such as whitepapers, reports, accreditations, certifications, and third-party attestations are available for customers to learn more about compliance controls and implement them.
Top 8 AWS Cloud Security Best Practices
Just like any other service, the security of your AWS cloud depends on how you configure and manage it. In this section, we’ll go over some of the most important best practices that you can follow to ensure the security of your data in the AWS cloud:
Understand Your Responsibilities
While AWS provides a plethora of security tools to secure your cloud environment, it follows the shared responsibility model when it comes to security. Under this model, AWS is responsible for the security of the cloud infrastructure and its customers are responsible for configuring and managing their respective AWS services and resources properly. Essentially meaning that Amazon is responsible for the security of the cloud and customers are responsible for security in the cloud.
Encryption and Backups
Data encryption is key to maintaining security in the cloud. By default, AWS offers AES256 encryption for all data stored in the Amazon S3 buckets. In addition, you can take advantage of Amazon Key Management Service to create your own encryption keys and encrypt your data.
Backup your cloud data in 3 copies and 2 different locations, one of which is in a different physical location - either a different service or a different region. Also ensure that one of the backups is on a cloud service other than AWS.
Implement Strong Cloud Security Controls
Include strong cloud security controls in your security strategy. This includes clearly defining user roles, conducting regular privilege audits and removing privileges when the user no longer needs them, implementing a strong password policy, and multi-factor authentication and permission time-outs.
Leverage AWS Security Tools
It is advised to use the AWS Advisor tool that helps you to identify potential security vulnerabilities and provides recommendations for mitigating them. It provides recommendations for improving system performance and optimizing your infrastructure in accordance with AWS standards. In addition, you can use built-in AWS security tools such as Amazon CloudFront, AWS Shield, Guard Duty, and Cloud Watch that can assist you in securing your cloud environment.
Test Your Infrastructure Regularly
Regularly carry out security assessments and penetration tests against your AWS infrastructure to ensure that the security controls are effective and also to identify vulnerabilities or potential weaknesses.
Use a Cloud-Native Security Solution
To deal with the unique requirements of the cloud, use a cloud native security solution that can provide the visibility and controls that are required to secure cloud infrastructure. Cloud-native solutions enable continuous delivery, and protect your data from external threats. Moreover, some of them also help you with meeting compliance requirements.
Integrate Your Security Products
You can use numerous tools that are available within AWS and third-party providers to secure your cloud data. Some tools will present their findings in their own formats. Security Hub uses a unified format to integrate and present findings from various tools, eliminating the need for security teams to do so.
Keep Your AWS Security Best Practices Up to Date
As a leader in cloud computing, AWS is constantly improving its cloud infrastructure and security services to better serve its customers. Stay informed about the latest security updates and keep updating your AWS security best practices and store these policies on a shared drive accessible by all of your users so that everyone is on the same page. You can patch your AWS servers using a variety of third-party tools. You can also use AWS Systems Manager Patch Manager, which allows you to easily automate patching for your cloud systems.
AWS with Evolve
As you migrate to AWS Cloud or expand your AWS services, you will face new threats and challenges that need to be addressed correctly.
Evolve Security Automation can help you automate your security processes with little to no impact on your workflow. Evolve Security Automation is the first of its kind, a security automation cloud with the ability to integrate with AWS services and the AWS cloud to provide comprehensive security protection for your AWS resources. See what's going on in your AWS environment with Evolve's data-driven reporting and dashboards that show you all of your AWS infrastructure at a glance.
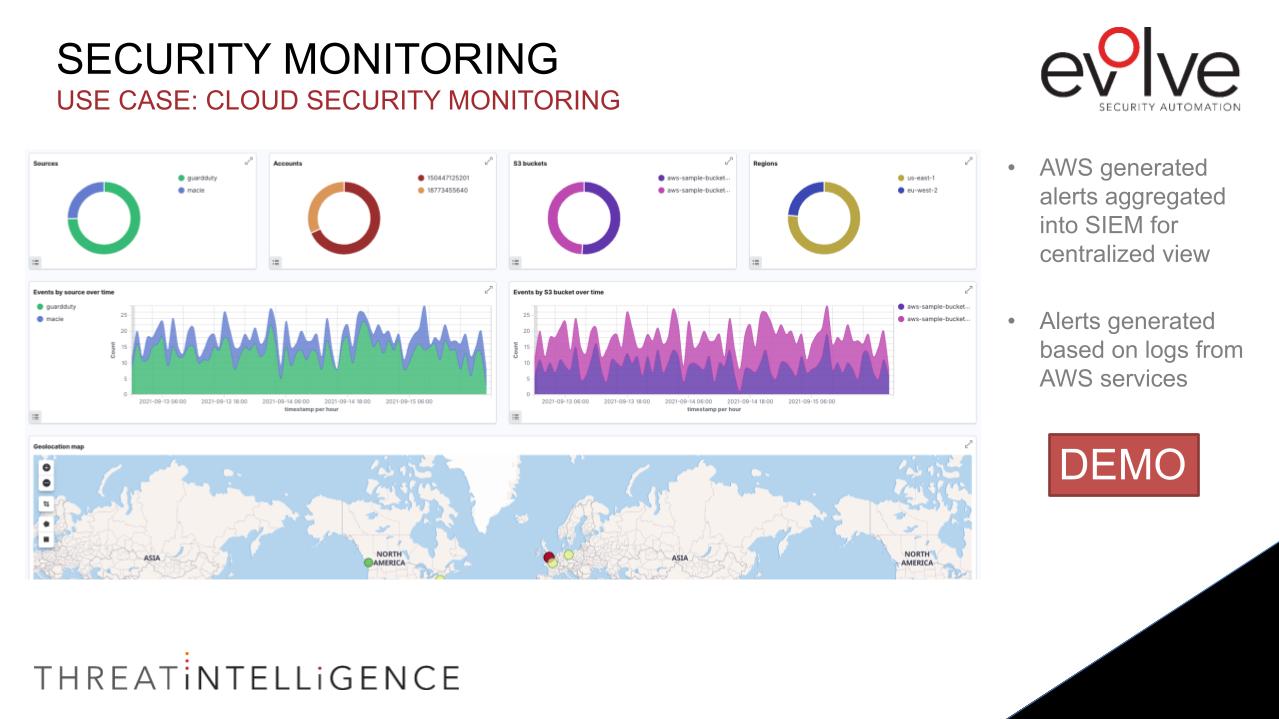
With Evolve’s XDR tool, it can ingest log data from cloud services, such as AWS. Log data can be collected from an S3 bucket, after which it is processed by out-of-the-box decoders and rules.
Evolve provides support for the following services:
- Amazon Key Management Service (KMS)
- Amazon Guard Duty
- Amazon Inspector
- Amazon Macie
- Amazon Virtual Private Cloud (VPC)
- AWS Config
- AWS Cloud Trail
- AWS Trusted Advisor
- AWS Web Application Firewall (WAF)
What’s more, our penetration testing services are carried out by some of the best security experts in the world with decades of experience under their belts. If you have any questions about how Evolve can help you secure your data and your AWS cloud, feel free to reach out to us and
book a free consultation/demo.







