EvolveSC Ensures Seamless Protection from Supply Chain & Third-Party Risks. No Manual Hassles – Just Monitor, Assess, and Defend.

The safety of your supply chain is critical to the success of your business.
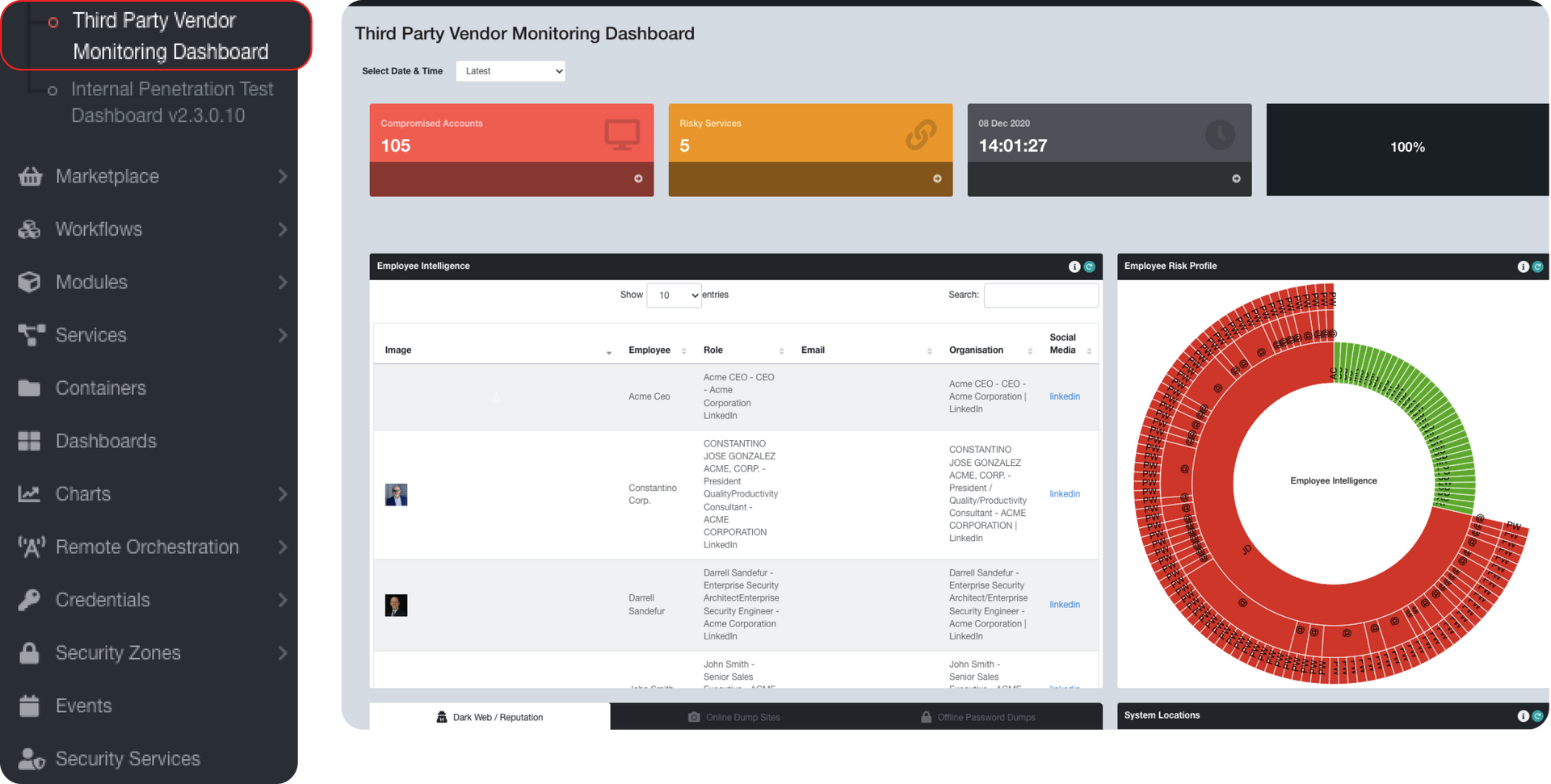
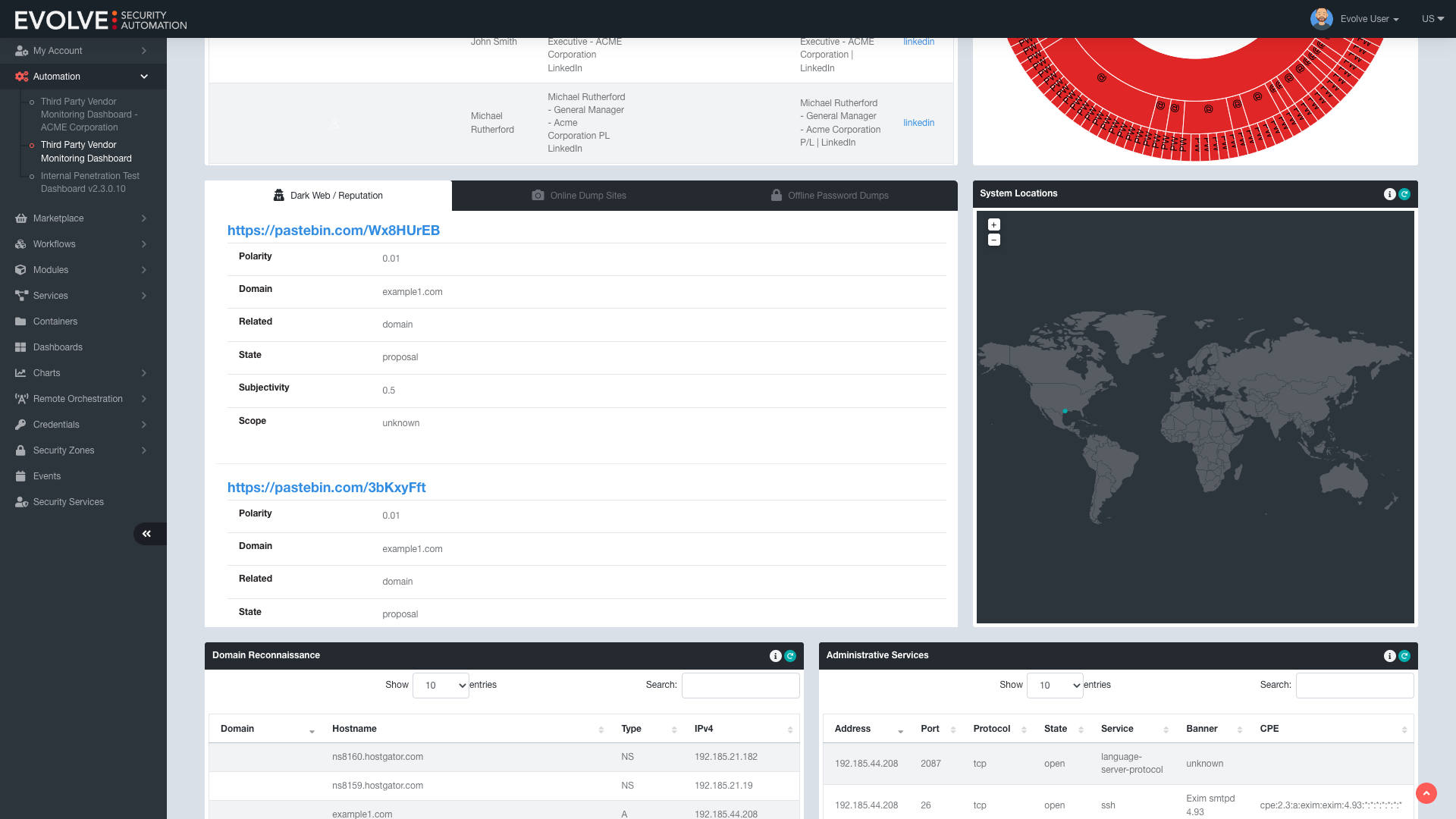
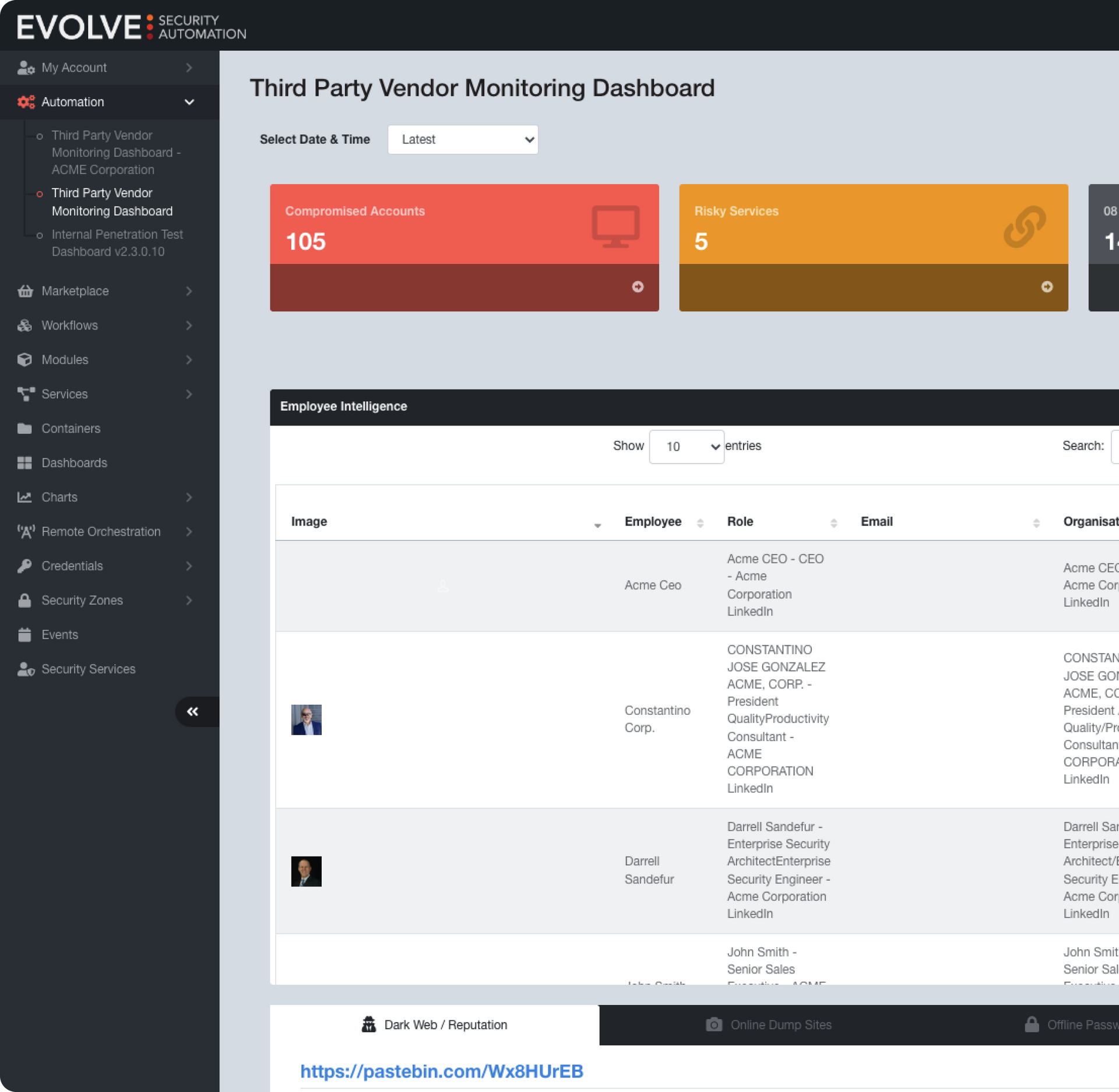
With EvolveSC, you can easily monitor and assess risks to your supply chain without spending time and resources on laborious manual assessments. Gather insights about your organization, employees, and systems, such as revealed passwords, exposed systems and exploits, suspicious dark web activity, and more. Effortlessly identify potential attacks against your supply chain and enterpise with the first ever third-party risk management solution.
Stay Connected and Secure
Outsourcing services is a more viable option for businesses looking to accelerate their growth. EvolveSC can help you continuously monitor and assess third-party risks, allowing you to grow your business without potential supply chain risks holding you back. With our automated, intelligent, and scalable technology, you can actively guard your gates and secure your most valuable information.
A Modern Solution for the Modern Supply Chain
As business environments evolve, the need to adapt is imperative. EvolveSC leverages automation to provide a modern solution for the ever-changing business landscape, allowing businesses to stay agile and remain competitive. Its platform enables you to safeguard data, minimize disruptions, build trust and transparency with customers, and ensure secure data movement across your entire supply chain.
Challenge Third-Party Security
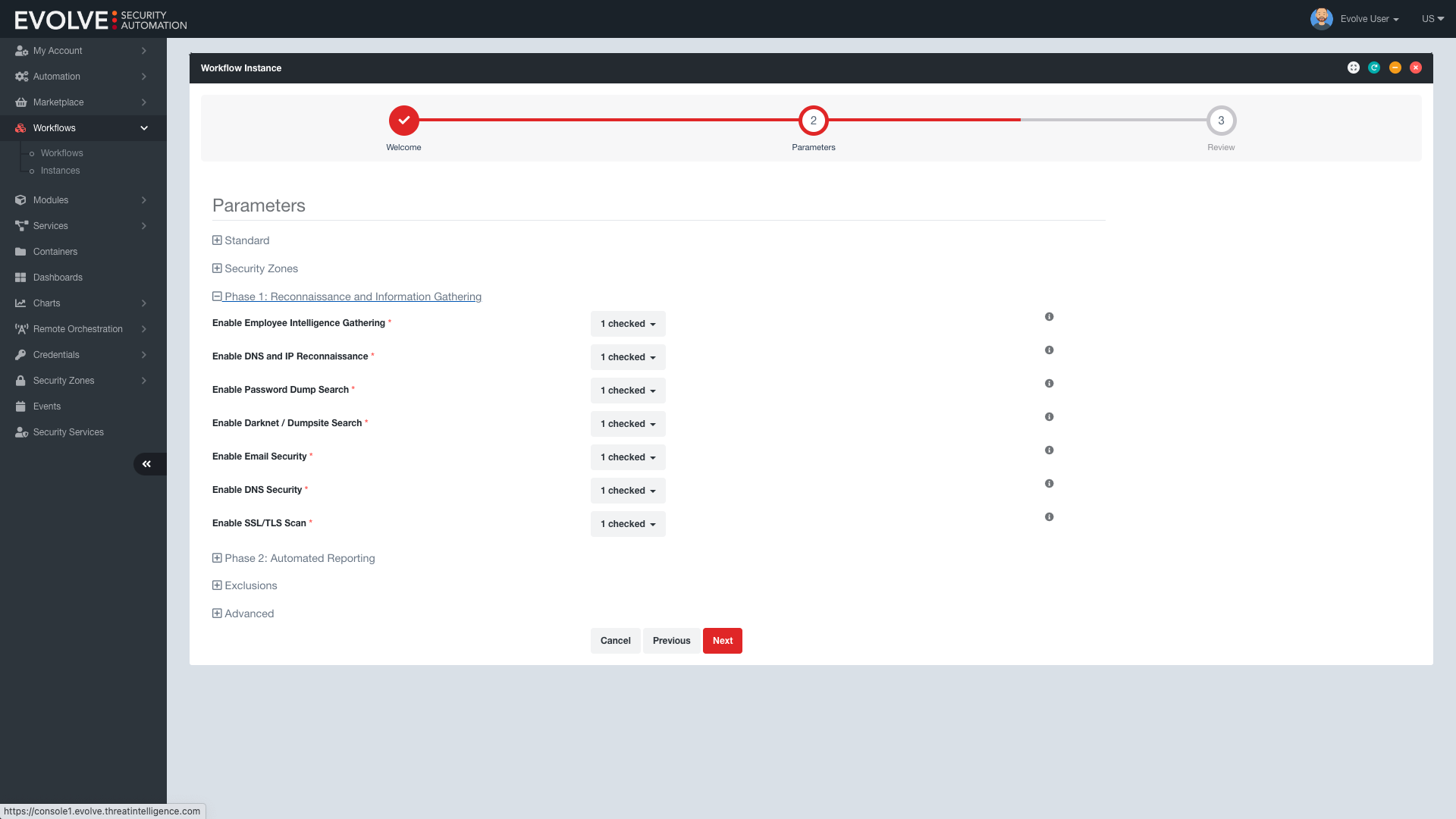
EvolveSC lets you go one step further than simply monitoring your supply chain and put the security status of your vendors to the test, with our automated pen testing workflows. No manual effort is required to evaluate and score vendors against industry standards such as OWASP, ISO, or internal policies. With our integrated testing capabilities, you get an extra layer of security that will validate the safety of your data and give you the confidence to take swift action when needed.

Monitor third-party risk 24/7
Gain frequent insights into your supply chain risks and discover precisely where your weakest links are, without the hassle of obtaining approvals.

Detect critical risks quickly and easily
Minimize the time it takes to detect critical risks across all your third-party vendors – completely passively.

Proactive supply chain security
Gain visibility into third-party vendors' security status, make more informed decisions when it comes to your supply chain, and avoid the negative impacts of security breaches.
Key Features
- Employees most susceptible to threats
- Email address prediction and verification
- Leaked usernames and passwords
- Compromised systems and services
- Suspicious dark web communications
- IP and DNS reconnaissance
- Unknown domains and system
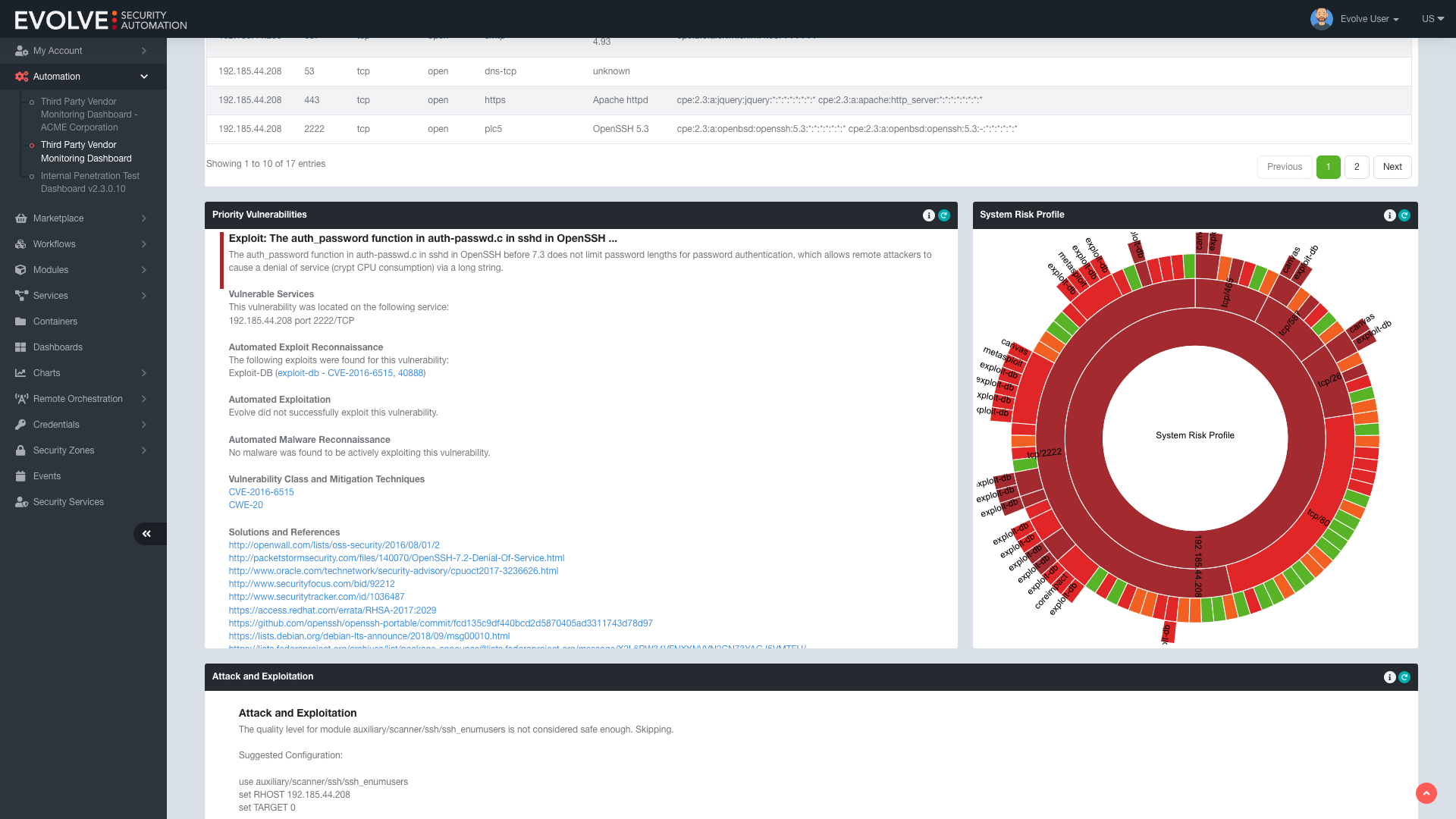
- Real-time exploit locator
- Automated exploit configuration
Selected to conduct and manage penetration testing examinations for the Australian Government, our team members not only hold positions on the Board of Directors of CREST Australia and New Zealand, but also lead the CREST Technical Team.

With extensive experience in the longest running training course at Black Hat USA and a position on the Black Hat Asia Review Board, our trainers are renowned for their expertise in the most recent threats and the cutting-edge techniques to combat them.

Threat Intelligence contributes to the development of global security methodologies, standards, and libraries that are incorporated into industry-specific security regulations of the Open Web Application Security Project (OWASP).

The Team Behind Evolve
Ready to Get Started?
Is your organization looking for a complete cyber security solution? With our products and services, your team can take a propositive security posture. Let’s chat.