Free Cyber Security Resources
Ebooks, industry brochures, playbooks and more to help you secure your organisation!
[ATTACK REPORT]

November Attack
Report
Discover how RansomHub is targeting critical sectors with double-extortion tactics, impacting 210 victims. Insights from David Gilmore, Cybersecurity Analyst & AI Researcher.
[BROCHURE]

Critical Infrastructure Cybersecurity
Check out our brochure for insights on the latest threats and how we protect critical infrastructure.
[PLAYBOOK]

ISO 27001 Compliance Playbook
Access our ISO 27001 Compliance Playbook for practical tips to strengthen your security and meet regulatory requirements.
[EBOOK]

Your Essential Guide
to Third-Party Risk Management
Explore the major risks that can flow from third-party attacks, and the key factors for any organisation looking to mitigate threats that may emerge from your supply chain.
[PLAYBOOK]
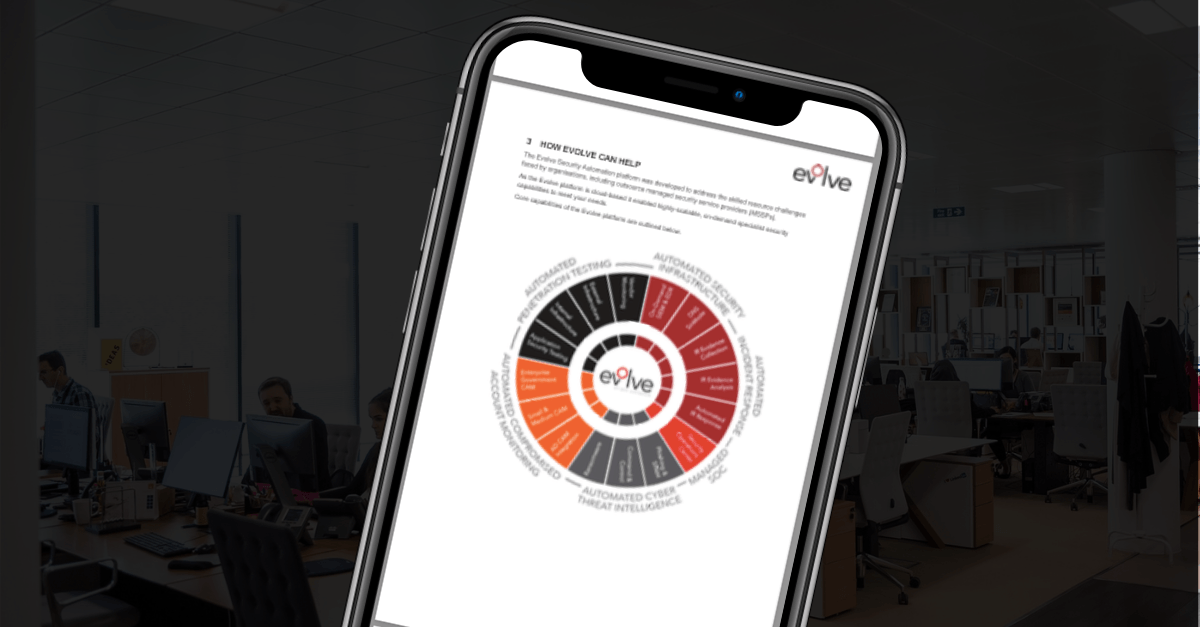
Security Operations Centre (SOC)
Playbook
Explore how a Security Operations Centre (SOC) is essential to your IT infrastructure and how to be as efficient and effective as possible.
[BROCHURE]

Cybersecurity for Governments
Brochure
Explore the challenges and solutions of the Cybersecurity Government industry and how our team employed Evolve to enhance their cybersecurity posture.
[BROCHURE]

Cybersecurity for Education
Explore the challenges and solutions of the Cybersecurity Education industry and how our team employed Evolve to enhance their cybersecurity posture.
[EBOOK]

Getting Started with Penetration Testing
This guide provides you the essential overview you require to make an informed decision about what penetration testing approach is right for your organization.
[EBOOK]

Regulatory Compliance for SMBs Business
A comprehensive guide for small and medium businesses that are getting started with compliance.
[BROCHURE]

Healthcare Cybersecurity
Brochure
Explore the challenges and solutions of the Cybersecurity Healthcare industry and how our team employed Evolve to enhance the cybersecurity posture of our clients.
[EBOOK]

The Complete Guide to Automating Enterprise Ransomware Protection
Protect your enterprise from the devastating effects of ransomware. Our guidebook offers practical steps to automate prevention and rapid containment in the event of a breach.
