Enterprise Cybersecurity Solutions That Adapt to
Your Business Needs
Protect your cybersecurity ecosystem from the most advanced cyber threats with Threat Intelligence's global expertise and Evolve Security Automation
Evolve automates complex cybersecurity processes instantly, eliminating the need for multiple isolated solutions and reducing human intervention





Is your organization looking for a complete cyber security solution?
With our products and services, your team can take a proactive security posture.

Services
A Certfied Cybersecurity team to meet your needs
Our services combine the expertise of highly experienced cyber security consultants with security automation.
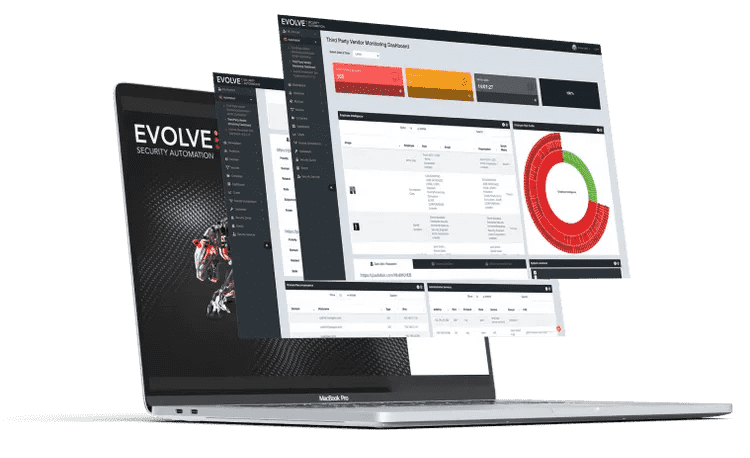
Evolve is the next generation of SOAR platforms.
Evolve gives security teams the tools and clarity they need to: mitigate attack surface, detect dubious behaviour, and fast respond and remediation with intelligent automation.
Platform
Goal
Our goal is to innovate security automation
At Threat Intelligence, we know that effective cyber defense requires more than just off-the-shelf products or a one-size-fits-all approach. That's why we offer a unique combination of cutting-edge security products and highly-skilled services that are tailored to meet the specific needs of your organization. Our innovative solutions redefine how cyber security capabilities are deployed and delivered globally, empowering you to secure your business against even the most relentless cyber threats.

Selected to conduct and manage penetration testing examinations for the Australian Government, our team members not only hold positions on the Board of Directors of CREST Australia and New Zealand, but also lead the CREST Technical Team.

With extensive experience in the longest running training course at Black Hat USA and a position on the Black Hat Asia Review Board, our trainers are renowned for their expertise in the most recent threats and the cutting-edge techniques to combat them.

Threat Intelligence contributes to the development of global security methodologies, standards, and libraries that are incorporated into industry-specific security regulations of the Open Web Application Security Project (OWASP).

The Team Behind Evolve

Services
A Certfied Cybersecurity team to meet your needs
Our services combine the expertise of highly experienced cyber security consultants with security automation.
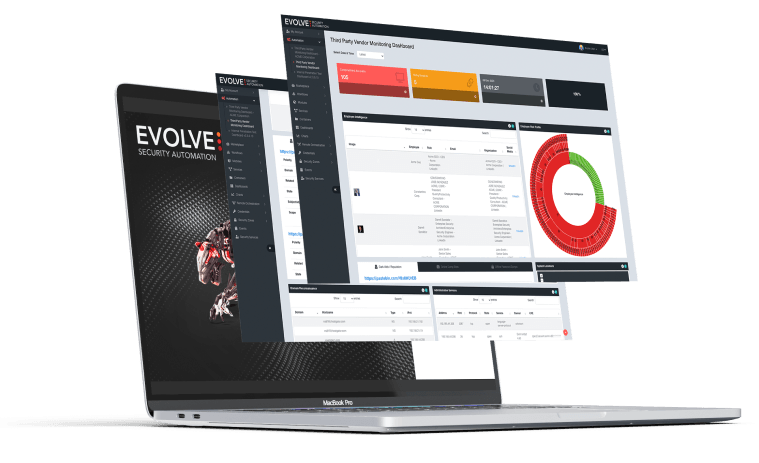
Evolve is the next generation of SOAR platforms.
Evolve gives security teams the tools and clarity they need to: mitigate attack surface, detect dubious behaviour, and fast respond and remediation with intelligent automation.
Platform
Goal
Our goal is to innovate security automation
We enable organisations to secure themselves through security automation against relentless cyber threats by redefining how cyber security capabilities are deployed and delivered globally through our innovative security products and highly-skilled services.

Blog
Ready to Get Started?
Is your organization looking for a complete cyber security solution? With our products and services, your team can take a propositive security posture. Let’s chat.





