Imagine that you are a security manager responsible for the security of your enterprise. You have just received a report that an intruder has gained access to your company's database containing sensitive customer information. You have one hour to respond to the intruder before he or she can leak the information to the public. How would you respond? What resources would you need to respond? Would you have to notify the authorities? What should you do?!
Time-sensitive issues like this can't afford to be dealt with in a last-minute fashion. Fortunately, you can be prepared through tabletop exercises that simulate these high-pressure scenarios. Read on to learn about the benefits of tabletop exercises and how to conduct them.
What is a Tabletop Exercise?
We all know how important it is to have an incident response plan. It helps you delegate roles and responsibilities, and it allows you to have a structured plan to follow during a cyber incident. While having an Incident Response Plan is a good start, it's not enough to rely on it alone. When it comes to cyber security, you need solid proof that your defenses and contingency plans work. You cannot afford to leave it up to chance. This is why it's essential to validate your security measures. Testing your defenses gives you a much needed understanding of how they will perform during an actual attack. In addition, you also get a good idea of what your vulnerabilities are and how you can improve them.
So, how do you know that your team is well prepared to handle any incident when it occurs? With a tabletop exercise.
NIST
defines a tabletop exercise as 'A discussion-based exercise where personnel with roles and responsibilities in a particular IT plan meet in a classroom setting or in breakout groups to validate the content of the plan by discussing their roles during an emergency and their responses to a particular emergency situation. A facilitator initiates the discussion by presenting a scenario and asking questions based on the scenario.'
A tabletop exercise is a simulation of a real-world scenario that involves a group of individuals playing out a hypothetical incident response situation. The objective is to evaluate the effectiveness of an organization's incident response plan and to identify gaps in the plan, procedures, and communication channels. The simulation is conducted in a controlled environment and does not involve any actual physical activity.
Why Do You Need Tabletop Exercises?
There are several reasons why your organization needs a tabletop exercise. Some examples are:
- Improving Incident Response Plan: A tabletop exercise is an effective way to evaluate the effectiveness of your IRP. By running a simulation, you can identify gaps in your plan and adjust it accordingly to ensure that it can handle any real-world situation.
- Enhancing Team Communication: During a tabletop exercise, the team can practice their communication channels, identify bottlenecks, and streamline the process. This can help to ensure that everyone is on the same page during an actual incident and that information is being communicated effectively.
- Identifying Key Decision Makers: In the event of an incident, it's essential to have clearly defined roles and responsibilities. A tabletop exercise can help identify key decision-makers and ensure that everyone understands their roles and responsibilities.
- Building Confidence: A tabletop exercise can help build confidence in the team's ability to handle an incident. By simulating a real-world scenario, team members can become more comfortable with the process and feel better prepared to handle an actual incident.
In fact, a recent study showed that tabletop exercises had a significant impact on the confidence levels of the team.
Lisa Forte, expert in running cyber crisis simulations, says that 'Human beings don't make good decisions under pressure. We make poor decisions that are short-sighted or maybe impulsive and that's [a crisis] is not the time to be making those decisions."
Can you imagine being in the middle of a cyber incident and your decision-makers don't know what to do? That is nothing but a disaster waiting to happen.
The main aim of a tabletop exercise is to prepare a crisis management team to handle a cyber incident in a simulated environment. This includes the identification of the stakeholders, understanding the roles and responsibilities of the team members, prioritizing response actions, and assessing the effectiveness of the crisis management plan.
During a cyber crisis, everything is dependent on the people involved, the decisions they make, and how they handle the situation. A tabletop exercise can help practice these decisions and decision-making skills, and refine the incident response process as needed, before an actual incident occurs. A tabletop exercise gives you the opportunity to make mistakes and learn from them, so that when it comes to the real thing, you're ready.
How to Design an Effective Tabletop Exercise for Incident Response
- Define the Objective: The first step is to define the objective of the exercise. You need to determine what you want to achieve by conducting the exercise. Is it to test the response capabilities of your team, to evaluate the effectiveness of your existing incident response plan, or to identify gaps in your incident response process?
- Identify the Scenario: The next step is to identify the scenario for the exercise. The scenario should be based on a realistic incident that could potentially impact your organization. This could include a cyber attack, a natural disaster, or a physical security breach.
- Create the Script: Once you have identified the scenario, you need to create a script for the exercise. The script should include the sequence of events that will unfold during the exercise. It should be detailed enough to provide a realistic simulation of the incident, but flexible enough to allow for improvisation.
- Assign Roles: Each participant in the exercise should be assigned a specific role to play. This could include the incident commander, the IT manager, the public relations representative, and others. Each role should have a specific set of responsibilities that align with the incident response plan.
- Conduct the Exercise: Once the roles have been assigned, you can conduct the exercise. During the exercise, you should follow the script and monitor the response of the participants. The exercise should be realistic enough to provide a meaningful test of your incident response capabilities, but controlled enough to ensure that it does not cause any actual damage.
- Debrief and Evaluate: After the exercise is over, you should debrief the participants and evaluate the results. This includes identifying any gaps or weaknesses in your incident response plan, as well as any areas where your team performed particularly well. You should also document the lessons learned from the exercise and use them to improve your incident response process.
By following these steps, you can design an effective incident response tabletop exercise that will help you to test and improve your incident response capabilities.
Incident Response Simulation - The Threat Intelligence Approach
Historically, incident response simulations targeted only security teams within an organization. However, due to the rise in cybercrime and its severe consequences, merely testing technical response capabilities is no longer sufficient. Simulations should now encompass executive and board-level focus, ensuring that all staff members, including non-IT personnel, understand their responsibilities during a cyber-attack. The goal of such exercises is to familiarize executives and board members with incident response management at their level.
Our team has experience conducting such incident response tabletop exercises for numerous clients in a variety of industries. While we have designed our exercise methodology to be flexible, we have found that we consistently get the most out of the exercise when we follow a specific, step-by-step process. This process includes the following steps:
Introduction to Incident Response Simulation and the Process
This is a brief overview of the incident response simulation, including the goals and objectives of the exercise. Objectives of the Incident Response Simulation:
- To gain a deeper understanding on how to apply the plan to real-world scenarios
- To identify any areas that need improvement in the current processes
- To become prepared for when a security breach occurs to respond effectively
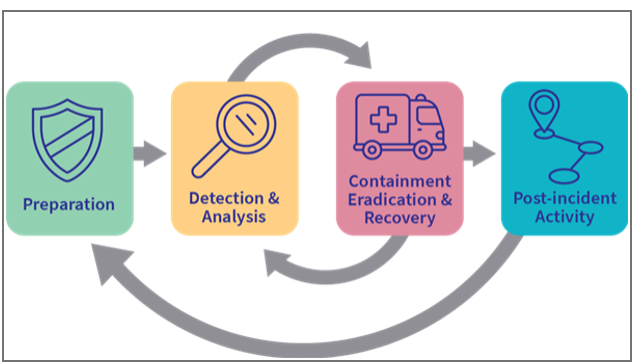
Incident Response Phases
- Preparation Phase - This step would include collecting all the necessary data to respond to an incident. From a technical standpoint, this would include gathering information about the systems that are at risk, making sure the right security controls and security monitoring are in place, and what tools are available to respond to the incident.
- Identification Phase - Detecting potential incidents and identifying the type and scope of the incident.
- Containment Phase - Containing the incident to prevent it from spreading and causing further damage.
- Eradication Phase - Removing the threat and restoring normal operations.
- Recovery Phase - Returning to normal operations and evaluating the incident response process to identify areas for improvement.
- Lessons Learnt - Analyzing the incident to identify what worked well and what needs improvement in the incident response plan.
Executive and Board Level Focus
This step involves discussing the incident response process at an executive and board level, including potential risks and ways to improve the organization's incident response capabilities. For a board and executive focused incident simulation, the exercise would begin with the escalation of an incident from the security team.
At a board level, the different phases of incident response would look slightly different.
For instance, at a board level, the preparation phase would include reviewing the company's policies, procedures, ethical considerations, and legal requirements.
Ty Miller, Managing Director at Threat Intelligence says, "A lot of companies have only 10% of the data that's required to investigate a security breach. And that's because they haven't properly prepared for a breach."
It could also include discussing how to manage resources and the capabilities of the incident response team in an emergency situation. For example, what if some members of the team are unavailable or only available in a limited capacity? What if they're exhausted from regular work hours and are unable to respond immediately? Does the security team have adequate tools to respond to an incident or do they need to be upgraded? In case they require new tools, does the budget allow for this?
At each phase, think of what questions the board might ask, what concerns they might have, and how to address them.
Incident Response Enhancements
This last step involves implementing improvements to the incident response plan based on the lessons learned from the simulation.
Incident Response Phases
Red Team, Blue Team Exercises vs Tabletop Exercises
A Red Team exercise is a simulation of a real-world attack that is carried out by an independent group of security professionals. The goal of a Red Team exercise is to test the security of an organization by attempting to breach its defenses and identify vulnerabilities. The Red Team acts as the attacker, attempting to exploit weaknesses in the organization's security measures, while the organization's Blue Team defends against the attack. The goal of a Blue Team exercise is to test the effectiveness of the organization's security measures by assessing how well the Blue Team can detect and respond to simulated attacks.
Whereas, a tabletop exercise is a type of scenario-based training exercise that involves key stakeholders and decision-makers in a simulated crisis scenario. Unlike Red Team and Blue Team exercises, tabletop exercises don't involve a live attack. Rather, the focus is on assessing an organization's overall preparedness, communication, and decision-making capabilities in the face of a simulated crisis. It provides a stress-free environment for participants to practice their response plan. Tabletop exercises may not always involve people from all levels and departments of an organization, they can be conducted separately for the security team and the board and executives. Even when other departments are involved, it is usually a key representative from each department who participates.
For instance, let's say a city government wants to test its response capabilities in the event of a natural disaster, such as an earthquake or hurricane. The city government might organize a tabletop exercise that involves key stakeholders from various departments, including emergency services, public works, and transportation. During the exercise, the participants would be presented with a simulated crisis scenario and asked to make decisions based on the information available. The goal of this exercise would be to assess the organization's overall preparedness and response capabilities in the face of a crisis, including communication, decision-making, and coordination between departments.
Ty continues - "When a company has done these exercises a few times, they can start getting bored of them. In such cases what we recommend is to actually attack the company and see how they respond."
So, red and blue team exercises can be a natural next step for companies that are already doing tabletop exercises regularly.
To learn more about how Red and Blue Teams work, check out our
blog post on the same.
Common Scenarios for Tabletop Exercises
Here are some common scenarios that can be used as the basis for tabletop exercises.
Data Breach: A hacker gains access to a company's database containing sensitive customer information, such as names, addresses, and credit card numbers. The hacker then threatens to leak this information publicly unless the company pays a ransom.
Ransomware Attack: An employee unknowingly clicks on a phishing email, which installs ransomware on the company's network. The ransomware encrypts all of the company's files, making them inaccessible, and demands a large sum of money to provide the decryption key.
Insider Threat: An employee who is disgruntled with the company's management decides to leak confidential information to a competitor. The employee uses their authorized access to the company's network to steal and distribute sensitive information.
Physical Security Breach: An unauthorized individual gains access to a company's server room by tailgating behind an employee with authorized access. The individual then proceeds to steal or damage the servers, causing the company to lose valuable data and suffer significant downtime.
Conclusion
In conclusion, conducting incident response tabletop exercises is crucial in preparing organizations for cybersecurity threats and other crisis situations. By simulating various scenarios, decision-makers and key stakeholders can test their communication, coordination, and ability to make informed decisions under pressure. With the average cost of a data breach expected to surpass $5 million in 2023, being well-prepared is vital. By investing in these exercises, organizations can mitigate risks and reduce the potential impact of a real-life crisis.
Ready to put your incident response plan to the test? Contact our team of experienced security analysts to schedule a tabletop exercise and ensure your organization is prepared for any security incident.







