In 2020, the COVID-19 pandemic and organizations’ rapid transition to remote operations have created numerous opportunities for threat actors to launch sophisticated cyber attacks, with serious repercussions. Research suggests that since the start of the pandemic, remote workers have caused security breaches in 20% of organizations , while ransomware attacks accounted for over one-third of cyber incident response cases in 2020. Yet another report called 2020 the “worst year on record,” with almost 3000 publicly-reported data breaches, leading to the exposure of a staggering 44+ billion records.
Fast forward to 2025, ransomware cases decreased by 11.5% year over year, but ransomware-affiliated groups continue to upgrade their attack techniques. In addition, 32% of incidents observed involved attackers using legitimate IT tools for malicious purposes. (IBM)
Clearly, cybersecurity incidents are inevitable and are becoming more challenging to detect. However, how organizations respond to an incident can have a tremendous bearing on its ultimate impact. To mitigate an incident’s effect on their data, and ultimately on their revenues and reputations, organizations must take appropriate steps to minimize their vulnerability. Here’s where Incident Response (IR) can play a game-changing role in preparing and protecting organizations from future threats. We must ask four questions when considering Incident Response Plans:
- What is incident response and why is it important?
- What are the four phases of incident response?
- What are the five steps of incident response?
- Which phase of incident response involves investigation and diagnosis?
In this detailed guide, we will cover all of these key aspects. We will also explore incident response plans for small businesses, and give examples of incident response plan flow charts.
Let’s start with the most basic question: What is Incident Response?
What is Incident Response?
“Incident Response” (IR) involves more than just responding to a security incident. IR is a systematic, proactive, reactive and preventative approach that enables organizations to prepare for, detect, mitigate, and recover from cybersecurity incidents. It involves both planning and execution, and allows firms to respond effectively to an incident in an orderly and effective manner so that they can minimize its impact and protect their assets, financial health and reputation.
An IR program helps strengthen the organization’s ongoing risk assessment and incident response process. It also supports knowledge-sharing and documentation, and helps with litigation so legal teams can understand the applicable reporting and notification requirements under data breach laws.
Why is Incident Response Important?
A failure to implement an IR Plan (IRP) can have disastrous consequences. It weakens the organization’s security posture and makes them more vulnerable to the business, financial and legal consequences of attacks. Their insurance claims may be rejected, which will affect their bottomline, business continuity and longevity.
Unfortunately, many organizations lack a formal IRP. According to IBM's 2024 X-Force Threat Intelligence Index, 51% of organizations have only an informal or ad hoc plan, despite the fact that those with a formal IRP experience less business disruption and greater cyber resilience. Notably, organizations with a formal IRP spend about $1.2 million less on data breaches than companies without such preparations.
Many cybersecurity risks are often not detected until it’s too late, which creates numerous operational challenges for organizations. Due to its emphasis on anticipation, adaptation, agility and speed, a formal IRP with clear measures can help eliminate these challenges quickly, and/or minimize their impact.
What Are The Four Phases Of Incident Response?
The National Institute of Standards and Technology (NIST) has created an Incident Response Life Cycle that effectively answers the question: What are the four phases of incident response?
I. Preparation
It is impossible to effectively respond to incidents – much less prevent them – at a moment’s notice. That’s why preparation is critical when establishing IR capability and ensuring the security of the organization’s systems, networks and applications. Preparation must include all the below activities:
- Set up an IR team, define responsibilities and clarify their decision-making powers;
- Set up multiple communication and coordination mechanisms, including devices, software and incident analysis resources;
- Create a jump kit containing materials that may be needed during an investigation in order to facilitate faster responses;
- Conduct periodic risk assessments of systems and applications;
- Harden hosts using standard configurations, following the principle of “least privilege”;
- Configure the network perimeter to deny all unauthorized activities;
- Deploy anti-malware software at the host, application server and application client levels.
Conduct awareness training so users are clear on the appropriate use of networks, systems and applications.
II. Detection and Analysis
The second phase helps determine whether a security incident occurred, and analyze its severity and type. The NIST outlines the following steps:
- Identify the most common attack vectors so as to define specific handling procedures;
- Pinpoint signs of an incident, both current (indicators) and future/possible (precursors) to determine the type, extent and magnitude of the problem, as well as weed out false positives;
- Analyze and validate incidents to determine their scope, points of origin and attack vectors;
- Document and timestamp all incidents including system events, conversations and observed changes in files.
Prioritize incidents based on relevant incident-specific factors like:
- Functional impact;
- Information impact;
- Size;
- Type of resources affected;
- Notify appropriate individuals so they can execute their specific roles and functions.
This phase can be challenging for numerous reasons. One, incidents may be detected by many means, making the detection process extremely complex. Next, some incidents are nearly-impossible to detect. Third, the high volume of indicators of potential compromise (IOCs) make it difficult to separate genuine issues from “noise.” Finally, incident analysis is a people-dependent activity, even with automation, so a lack of human expertise can weaken the organization’s detection/analysis capabilities.
III. Containment, Eradication and Recovery
The goal here is to mitigate or minimize the effects of a security incident before it can overwhelm resources or cause too much damage. But it’s necessary to predetermine strategies and procedures. It’s also important to define containment strategies based on acceptable risks and criteria, such as:
- Potential for resource damage;
- Value and business impact of affected assets;
- Need to preserve evidence/order of volatility;
- Continuity of service;
- Resources and time required to implement the strategy.
Other important steps include:
- Evidence gathering, handling and documentation: For incident resolution and (possible) legal proceedings;
- Identifying the attacking host(s): By validating the attacking host’s IP address, using incident databases, and monitoring possible attacker communication channels;
- Eradication and recovery: By identifying all affected hosts and exploited vulnerabilities, and eliminating components of the incident (e.g. malware);
- Restore systems to normal operations: By remediating vulnerabilities to prevent similar incidents in future.
IV. Post-incident Activity
While cybersecurity incidents cost organizations, on average, $3.86 million (IBM) , they also provide opportunities for learning and improvement. This is why NIST suggests that every IR program should include a “lessons learned” element based on meetings and follow-up reports that produce a set of actionable data, like:
- Incident count;
- Time spent per incident;
- Objective assessment via logs, forms, reports, etc;
- Subjective assessment of performance and outcomes.
These metrics can help improve security measures and the incident handling process, and also help with risk assessment and the implementation of additional controls.
What Are The Five Steps Of Incident Response?
What are the five steps of incident response in order in this model?
- Preparation: Develop IR policies and guidelines, conduct cyber hunting exercises, assess threat detection capability, and incorporate threat intelligence feeds;
- Detection and Reporting: Monitor security events, create tickets, and report incidents;
- Triage and Analysis: Collect data from tools and systems for further analysis;
- Containment and Neutralization: Restore systems and resume normal operations;
- Post-incident Activity: Document all information to prevent similar future occurrences.
What is An Enterprise Incident Response Plan, and What are Its Key Steps?

INCIDENT RESPONSE PLAN
An Incident Response Plan is a set of defined procedures that list the steps to be taken during the different phases of incident response. This must consist of roles and responsibilities for the IR team, communication plans, and systematic response protocols.
Your IRP must be written in clear language, free of any ambiguous terms. Listed below are three commonly used terms in IRPs that are often confused.
Event: An event is an observed difference on a regular device/user behavior/system/process. All logs are considered events. Examples of events are when an administrator connects to the router, when a firewall policy is published.
Alert:* An alert is an urgent notification triggered by a suspicious event or series of such events that is sent to responsible parties to take an action. Examples of alerts include multiple unsuccessful login attempts to an account, or a connection from an unknown IP address.
*Note that alerts are different from notifications as notifications don’t represent a risk to the system and are usually shown in a different window from alerts.
Incident: An event that negatively affects the organization’s business activity is called an incident. An incident usually starts when an analyst or system classifies an alert as an incident. An example incident is when a hacker posts company credentials online.
Incident response plan elements
An incident response plan usually includes these elements:
- The organization’s approach to IR;
- How IR supports the firm’s vision, mission and goals;
- IR phases and activities;
- Personnel roles and responsibilities, a clearly articulated chain of command, and senior management approval;
- Resource and activity prioritization strategy depending on the attack vector, data exfiltrated, and the criticality of the infrastructure components that may be affected;
- Key metrics to capture the capability, effectiveness and performance of the IR program;
- Communications flows between the IR team and stakeholders (internal and external);
- How lessons learned will be reinforced across the enterprise.
An effective incident response framework also includes a tailored IR policy that clearly defines elements, such as:
- Purpose, objectives and scope;
- Statement of management commitment;
- Definition of security incidents;
- Definitions of roles, responsibilities, and levels of authority;
- Reporting, communications and information-sharing requirements;
- Handoff and escalation points in the IR process;
- Incident prioritization;
- Performance measures.
Standard Operating Procedures (SOPs) should also be defined based on the IR policy and plan. They must specify the processes, techniques, checklists, etc. to be used, and should be tested to validate their usefulness. Training on SOPs can ensure that security incidents are handled efficiently and with minimal impact to the flow of business.
Incident response plan steps
This 7-step process is very effective for creating an effective IR plan:
- Prepare for potential incidents with triage exercises and playbooks;
- Identify the size and scope of an incident by starting with the initial compromised device;
- Isolate compromised devices to stop the spread of the attack;
- Eradicate threats by patching devices, disarming malware, disabling compromised accounts, etc.;
- Recover and restore normal services to the business;
- Document lessons learned to prevent future incidents;
- Train staff on incident response.
Incident Response Plans for Small Businesses
An incident response plan is critical for small businesses, particularly in a post-COVID world because it can help them react quickly and correctly to security incidents while minimizing cost and potential damage.
Here are the steps to create an incident response plan for small businesses:
- Identify possible security incidents that could impact the business;
- Decide how to react to each incident;
- Identify the personnel who will be responsible for handling incidents;
- Implement internal and external communications channels;
- Consolidate this information to create a comprehensive plan;
- Practice incident response;
- Adjust the plan as needed.
Incident Response Plan Flowchart
A fllowchart can be a great way to visualize the creation steps outlined in the previous two sections. Below is a good example of one:
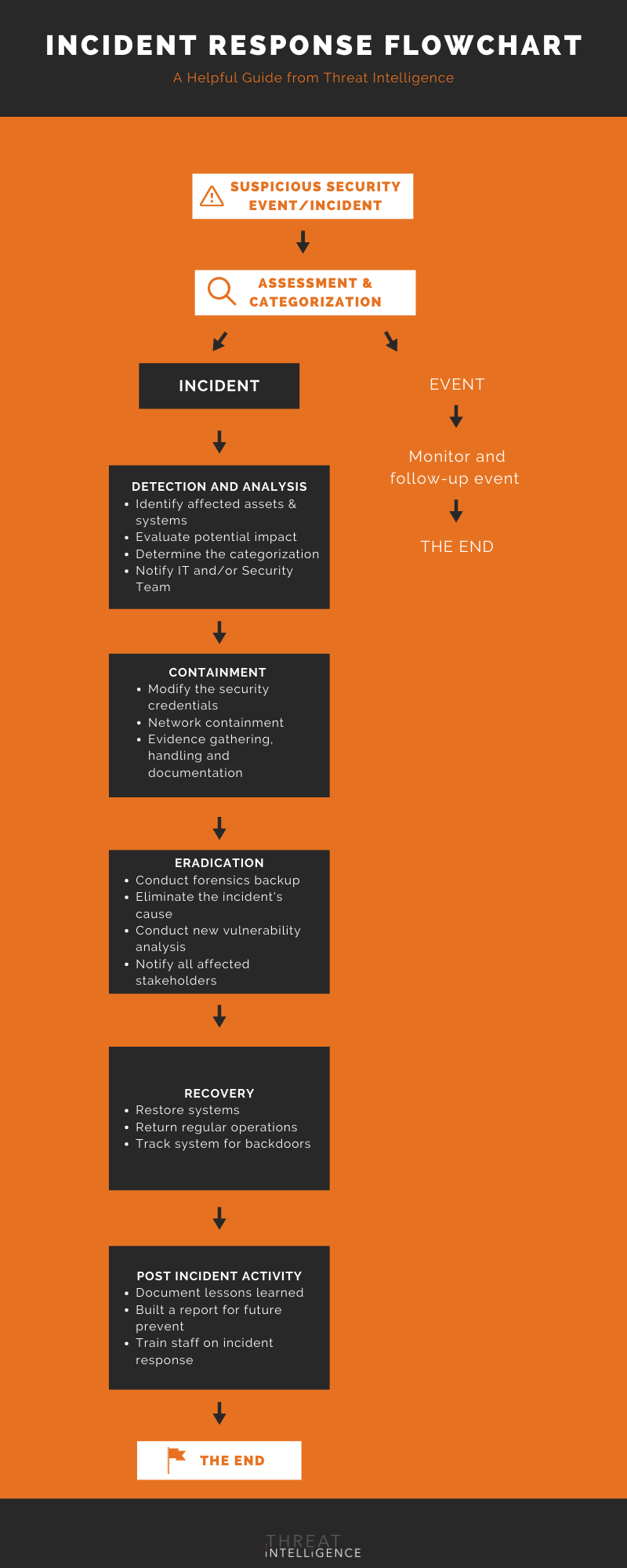
Incident Response Team
The IR team’s main goal is to ensure that the proper response is initiated with any security incident. It should include specialized sub-teams, each with a job to do. These include:
- Security Operations Center (SOC): The first line of defense to triage security alerts;
- Incident Manager: To determine incident response and a plan of action with various stakeholders;
- Computer Incident response Team: To provide expert technical inputs;
- Threat Intelligence Team: To constantly assess the cyber threat landscape and strengthen the organization’s security profile.
WHO HANDLES INCIDENT RESPONSE?
The Incident Response Team of an organization is responsible for addressing incidents across the business. The IR team’s main goal is to investigate security incidents and ensure that the proper response is initiated. It should include specialized sub-teams, each with specific roles. These include:
- Security Operations Center (SOC): The first line of defense to triage security alerts
- Incident Manager: To determine incident response and a plan of action with various stakeholders
- Computer Incident Response Team: To provide expert technical inputs
- Threat Intelligence Team: To constantly assess the cyber threat landscape and strengthen the organization’s security profile
In addition to the above-mentioned roles, the team can also contain members of the legal, human resources, and public relations departments.
IR Teams are also referred to as Computer Security Incident Response Team (CSIRT), Cyber Incident Response Team (CIRT), or Computer Emergency Response Team (CERT).
Building Your Incident Response Team
Your incident response efforts depend on how well your CSIRT is built. All the required roles and responsibilities must be filled in order to avoid higher damage and longer attacks. CSIRT models are of three different types:
Central: The team is made up of a centralized body that oversees IR for the entire company. For example, each subsidiary or branch of a big organization could have their own separate IR teams that report back to a single, central entity.
Distributed: There are multiple teams that work together to coordinate efforts as needed. Each team is usually in charge of a certain aspect of the IT infrastructure, a physical location, or a department.
Coordinated: Central teams are frequently in charge of system monitoring and can alert and assist distributed teams when necessary.
However, it can be difficult to figure out which model is appropriate for your company. The NIST guidelines for IR model selection include the following criteria:
- Availability
- Expertise
- Staffing
- Budget
WHAT IS INCIDENT RESPONSE ORCHESTRATION?
Incident Response Orchestration is the process that brings together trained people, proven processes, and integrated technology required to adequately deal with an incident. This helps the incident response analysts understand what their roles and responsibilities are and how to execute them. This facilitates accurate decision-making and boosts productivity for the IR team.
- Understand threats – Ensure sufficient planning and preparedness to improve cyber resilience in your organization. Have a standardized, documented, and repeatable IRP in place.
- Build an IRP - Analysts may run more tests, prioritize threats, and filter out false positives to provide a thorough picture of the suspected incident.
- Test and improves processes – Cyber security professionals must stay ahead of the latest cyber threats by proactively testing and enhancing incident response methods to meet and surpass the organization’s security requirements.
- Use threat intelligence – Collaborate as security professionals and share information to external sources like open-source security advisories, law enforcement and news media, and commercial solutions to improve threat intelligence against cybercriminals.
- Streamline incident investigation and response – Use automation to streamline repetitive and time-consuming tasks that are inefficient.
-
- Orchestration - Provide the IR team with the necessary support, knowledge, and tools to act quickly, correctly, and effectively.
Incident Response Plan Examples and Templates
Instead of building your IRP from scratch, you can save time and effort by starting from a template. One such example is provided by the California Department of Technology
here. It discusses the steps to be taken to implement an incident response plan, and to prevent the intrusion from happening again. Another template from the
Criminal Justice
Information Center provides guidelines on how an incident response plan can be written in order to respond to security incidents.
Listed below are some more templates that you can use as examples for building your incident response plan.
NIST INCIDENT RESPONSE PLAN
The NIST (National Institute of Standards and Technology) Incident Response Framework provides guidelines for effective incident response within organizations. It consists of several key components:
1. Incident Response Policy, Plan, and Procedure Creation: Organizations should develop customized policies, plans, and procedures that outline management commitment, purpose, scope, definitions, organizational structure, incident prioritization, performance measures, and reporting mechanisms.
2. Sharing Information With Outside Parties: Communication with external entities, such as law enforcement, media, vendors, and other incident response teams, should be appropriately managed and documented. Pre-established policies and coordination with public affairs, legal, and management teams are crucial.
3. Incident Response Team Structure: An incident response team should be available to handle incidents promptly. Different team models, such as a central team or distributed teams, can be implemented based on the organization's size and geographical diversity.
4. Staffing Models: Organizations can choose from various staffing models, including internal teams, partial outsourcing with contractors' assistance, or full outsourcing to qualified providers.
AUSTRALIAN CYBER SECURITY CENTRE (ACSC) INCIDENT RESPONSE PLAN
The ACSC Cyber Incident Response Plan begins with preparation, which includes developing response plans, training personnel, and conducting tests/exercises. The next phase is detection, investigation, and activation, involving incident confirmation, classification, and activation of the response teams. The plan then moves to containment, evidence collection, and remediation, where activities are documented, evidence is collected, and remediation actions are executed.
The recovery and reporting phase focuses on executing the recovery plan, concluding the response teams' activities, and preparing an internal incident report. Finally, there is a phase dedicated to learning and improving, involving post-incident reviews, updating the incident response plan and associated materials, and addressing communication, engagement, legal, regulatory, notification, and reporting requirements.
CISA INCIDENT RESPONSE PLAN
The CISA Incident Response Plan walks you through 3 stages of incident response: Before, During and After.
BEFORE A CYBERSECURITY INCIDENT
It is important to train staff on their security roles and reporting suspicious events. Review the incident response plan with an attorney and establish relationships with CISA regional teams and local law enforcement agencies. Print and distribute relevant documents and contact lists, develop an incident staffing and stakeholder plan, and regularly review the plan. Prepare press responses, select an outside technical resource for investigations, and conduct attack simulation exercises to practice incident response scenarios.
DURING A CYBERSECURITY INCIDENT
Key actions include assigning an Incident Manager (IM) to lead the response and manage communication flows, stakeholders, and task delegation. An assigned Tech Manager (TM) acts as the subject matter expert, bringing in internal and external technical experts as needed. A Communications Manager (CM) handles interactions with reporters, social media updates, and external stakeholders.
AFTER A CYBERSECURITY INCIDENT
Important steps include conducting a formal retrospective meeting to analyze the incident, identify areas for improvement, and update policies and procedures accordingly. Retrospectives should be blameless and focus on the system's failures rather than individual actions. Communicating the findings to the staff promotes transparency and builds a culture of security.
Automated Incident Response
Automation refers to the process of replacing manual tasks with machine-based automated actions. When it comes to incident response, automation is used mainly for two purposes:
Investigations:
this includes automating the collection of contextual information for an incident, such as threat intelligence and patterns from previous incidents for context.
Actions: actions that can be automated include sending commands to security products such as firewalls and servers to block certain IP addresses.
Automated incident response systems leverage advanced technologies to collect and analyze contextual information for incidents. They tap into threat intelligence sources and mine patterns from previous incidents, providing invaluable context to the incident response team. This contextual information empowers the team to make well-informed decisions and take appropriate actions swiftly, enhancing the overall effectiveness of the response.
Moreover, automation extends to the execution of actions within the incident response process. Certain tasks, such as sending commands to security products like firewalls and servers, can be automated. For example, when a malicious IP address is identified, automated incident response systems can trigger the automatic blocking of that IP address across relevant security devices.
Automating the IR process comes with many benefits like:
Real-time Detection: Automated incident response systems continuously monitor network and system activities in real-time. They leverage advanced detection mechanisms, such as behavioral analysis and anomaly detection, to identify potential security incidents promptly. By detecting incidents in real-time, organizations can respond swiftly and prevent further damage or data breaches.
Deep Technical Investigation: Automated incident response tools provide capabilities for deep technical investigation. They analyze the collected data, including log files, network traffic, and system artifacts, to gain insights into the nature and scope of the incident. This helps incident response teams understand the attack vectors, identify affected systems or assets, and assess the overall impact of the incident accurately.
Reduce Response Time: One of the significant benefits of automated incident response is the ability to minimize response time. By automating various aspects of the response process, such as alert triaging, evidence collection, and initial containment, organizations can significantly reduce the time it takes to address an incident. Rapid response is crucial for limiting the attacker's dwell time and mitigating the potential impact on the organization's systems and data.
Additionally, automated incident response helps address alert fatigue, a common challenge faced by incident response teams. Automating the initial triage and analysis of alerts, lets organizations prioritize and filter out false positives more effectively. This reduces the noise and overload of irrelevant alerts, allowing the team to focus on genuine threats and high-priority incidents.
With automation, organizations can also manage low-risk events efficiently. Not all incidents require the same level of attention and resources. Automated incident response systems can autonomously handle low-risk events, following predefined playbooks or response workflows. This enables the incident response team to allocate their time and resources more effectively, focusing on high-risk incidents that demand immediate attention.
As soon as suspicious activity is identified, our Evolve Security Automation platform triggers Automated Incident Response procedures to ensure the incident is contained as quickly as possible to minimize any negative impacts to your organization. To learn more about our automated incident response solution, schedule a demo with our team today.
AI & Automation in Incident Response
Cyber criminals are actively exploring AI's potential to devise malicious attacks. AI-generated phishing emails now take as little as 5 minutes to craft, compared to 16 hours manually. What's worse is that research indicates that AI-generated phishing emails are highly effective, with nearly 80% of recipients opening them. In addition to these developments, cyber criminals are leveraging AI to enhance the speed, scale, and automation of their attacks. This includes the use of AI-powered voice and video cloning techniques to impersonate trusted individuals, such as family members, co-workers, or business partners.
How AI Enhances Incident Response
With cyberattacks evolving, AI-driven security can enhance incident response by:
Automating Threat Detection – AI-powered SOAR (Security Orchestration, Automation, and Response) platforms analyze millions of security alerts, reducing false positives and detecting real threats faster.
Accelerating Incident Containment – AI can automatically isolate compromised endpoints, minimizing lateral movement.
Enhancing Threat Intelligence – AI models correlate real-time attack patterns to predict and respond to new threats.
Reducing Response Time – AI-assisted IR reduces the time between initial detection and remediation, helping organizations respond in minutes instead of hours.
Optimizing Triage & Prioritization – AI can analyze attack severity in real time, ensuring security teams focus on high-risk threats first rather than wasting time on false positives.
Supporting Rapid Decision-Making – AI-driven analytics provide actionable insights and automated recommendations, enabling IR teams to make faster, data-driven decisions during an incident.
Conclusion
Incident response begins as soon as a threat is detected in a company’s environment. With a detailed incident response plan, the organization can properly prepare for and plan to prioritize actions and minimize potential damage in the event of an incident. The threat landscape is widening and will continue to do so over the next few years. In this scenario, incident response is as critical for large enterprises as it is for small businesses, not only to regain control over systems and data, but to ensure business continuity in an unstable world.







