Self-replicating malware is a notorious nuisance that’s been around for as long as computers have. This year, a whopping 75% of organizations suffered a malware attack, up from 61% in 2020.
In this blog, we’re exploring the infamous malware attack - how it works and spreads, how to prevent it, and the worst attacks in history. Read on to learn more.
What is a Malware Attack?
Malware is any malicious software that is designed to damage and/or manipulate a programmable device or network. Malware comes in different forms such as spyware, adware, ransomware, trojan horses, viruses, and worms. A malware attack is a type of cyberattack where the malware executes itself on the victim’s computer and performs actions without the user’s consent or knowledge. These actions can include:
- Create copies of itself, spread to and infect different parts of the system
- Install apps that record keystrokes or control system resources without the user’s knowledge, thereby slowing down the system
- Steal, encrypt, or delete sensitive data
- Restricting access to files, programs and/or the system, and extorting money from the victims to restore access
- Swamping the browser or desktop with ads
- Altering search engine results
- Adding icons to the desktop, or redirecting users to popular websites
- Destroying critical components of a system and making it inoperable
The extent of damage depends on and varies with the type of malware that is used to carry out the attack. Malware attacks can target any type of data, right from financial information, medical records, personal emails to password credentials.
Proactive vs Reactive Cybersecurity
Website attack vectors are techniques or routes that hackers use to gain unauthorized access to a computer, system, or network in order to exploit vulnerabilities in the system. In this section, we’ll go over the ways in which malware can get into your system.
Malware is commonly distributed through email attachments, fake online advertisements, and/or infected applications and websites. Malware can also infect a computer via physical means such as infected removable devices like USB drives or external hard drives.
Usually, malware infiltrates a system when a user downloads or installs an internet program that they should not. Users are typically tricked into clicking on these malicious links or pop-ups that are disguised under flashing messages pretending to be genuine. Take a look at this example:
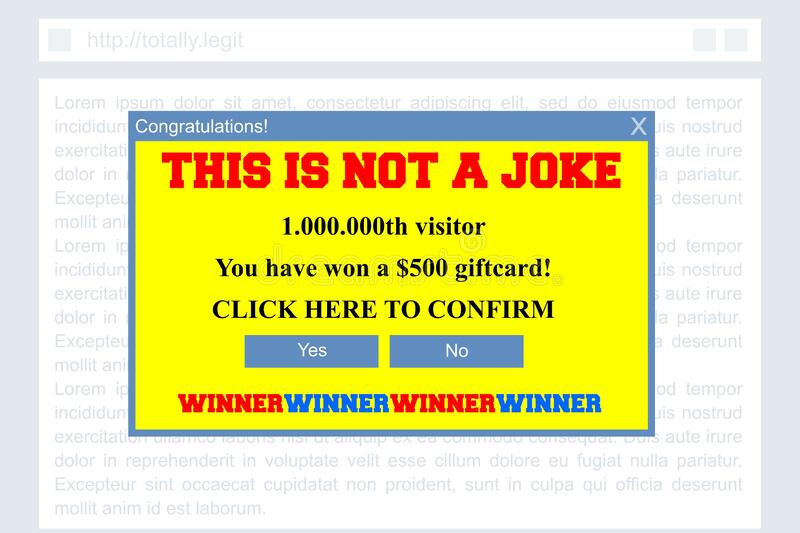
Source: viruspup.com
When the user clicks on the link, it automatically redirects to a malicious website that installs malware on the computer.
Following are the top 5 malware attack vectors that can be used to infect your systems:
Social Engineering
As mentioned above, social engineering methods are widely used by numerous types of malware to enter a device or network. These techniques such as phishing emails, smishing and pop-ups mislead unsuspecting users into launching a corrupted file or clicking on a link to an infected website.
Today, with the increased usage of social media, hackers can also leverage these platforms to deceive users. Sometimes, the photos you see on your social media could contain hidden malware. For instance, a photo you click on can take you to a fake webpage that requests you to download and install a plugin. Once you download the plugin, the attacker gains full access to your system.
Operating System Vulnerabilities
As the most sensitive part of your computer, the operating system is also vulnerable to cyberattacks. Worms - a common type of malware, spreads across computer networks by exploiting security vulnerabilities in the operating system. They are then used to execute payloads that can delete files, encrypt and/or steal data, and create botnets.
Compromised Websites
This method of attack is particularly dangerous because it can infect your computer without any intervention from you. Every day, approximately 30,000 new websites are hacked. When you visit a hacked website, it automatically starts searching for vulnerabilities on your computer. These vulnerabilities could arise from legacy versions of applications, unpatched vulnerabilities in the OS, or from browser plugins. If a security flaw exists, the hacker exploits it to install malware on your computer.
Remote Desktop Protocol
Remote Desktop Protocol or RDP is a network connection protocol that allows a user to connect to another computer using a network connection. It is usually used by IT administrators and support staff to access systems that are in different locations. Hackers scour the internet for computers that are accessible via RDP. Once they've discovered these systems, they use brute-force techniques to obtain the credentials and gain access to the system. The hacker then has complete control over the computer, and can install malware.
Infected Removable Drives
Malware can also spread through portable storage devices that are infected, such as USB drives or hard drives. The malware is automatically installed when you connect it to your system. The USB drive could get infected from a system it was previously connected to, or sometimes attackers deliberately leave infected devices in public for people to find.
Often, malware will get downloaded simultaneously along with other software that you download. This includes software downloaded from third-party websites as well as files shared via peer-to-peer networks.
Examples of Malware Attacks
Check out the details of some of the worst malware attacks till date:
ILOVEYOU Worm (2000)
A classic in the world of malware attacks, this worm was a pioneer in social engineering attacks. With the subject line “ILOVEYOU” , it took advantage of lonely people around the world and stole their credentials. The creator, Onel de Guzman, couldn’t afford dialup service so he created the worm that would help him use other people’s accounts. The worm exploited numerous vulnerabilities in Windows 95 and went on to infect millions of computers everywhere. It even temporarily shut down the UK Parliament’s computer system.
MyDoom (2004)
The MyDoom virus holds the record for the fastest-spreading virus (as of 2021). It was first discovered in 2004 and remains the most expensive virus outbreak ever, causing $38 million in damages.
Zeus Trojan (2007)
Also known as Zbot, or the “banking trojan”, Zeus is a Trojan Horse that was first discovered in 2007. It utilizes the man-in-the-browser keystroke logging and form-grabbing technique to steal banking information. One of its key features is its ability to create a botnet made up of infected computers, or bots. Bank of America, NASA, Monster.com, ABC, Oracle, Cisco, and Amazon were all victims of the Zeus Trojan.
Emotet (2014)
Emotet is referred to as the “King of Malware” because it is so good at its job. A polymorphic malware, Emotet’s functionality changes every time it is accessed. Like Zeus, it is also a Trojan and spreads predominantly through phishing emails. First discovered in 2014, Emotet is now used as a vehicle to spread other forms of malware.
WannaCry and Petya/NotPetya (2017)
These ransomware attacks were particularly controversial in the cyberworld. Hackers allegedly infected computers using EternalBlue, a National Investigation Agency (NSA) exploit. To read more about the most popular ransomware variants and how to protect yourself from them, check out our
blog post
on ransomware attacks.
Tips to Prevent Malware Infections
Now that you're aware of the
dangers of malware attacks, here's how you can prevent them:
Strengthen Your Primary Defenses
Follow the necessary best practices when it comes to application, appliance and system security. Maintain a strong password policy. In addition to implementing Multi-Factor Authentication, set strong and unique passwords that are at least 16 characters in length and update them regularly. Perform regular risk assessments and identify and patch vulnerabilities before update cycles.
Backup Your Data
The most effective way to defend against malware is by being able to restore data from clean backups. When it comes to backing up your data, ensure that you have a multi-layered defense including data encryption, built-in fault tolerance, and modern data isolation. This helps you avoid paying hefty sums of money to criminals that have your data.
Endpoint Monitoring
Deploy effective
endpoint monitoring
tools such as next-generation firewalls, intrusion prevention systems, and anti-malware software to monitor endpoint activity continuously.
Network Segmentation
Minimize the risk of exposure to an infection by isolating your network through network segmentation. To learn more about how network segmentation can prevent malware infections, read
here
.
Cyber Threat Intelligence
Monitor your network traffic carefully by running deeper and more advanced analytics to see what's going on across your network. Utilize
real-time threat intelligence
to better understand security information and emerging cybersecurity threats.
Zero-Trust Approach
This method ensures secure access from end-users, endpoints, APIs, IoT microservices, containers, and other sources. When you verify credibility before granting access, you make sure your workloads, workplace, and workforce remain safe.
Conclusion
The future of malware is undoubtedly uncertain. New variants and attack techniques will continue to come up. However, the good news is that no matter what the nature of malware evolves to become, you can always take the necessary steps to fight back and keep your systems protected.
The
Evolve
suite by Threat Intelligence comes with a range of cutting-edge capabilities that can equip you to fight malware threats. Right from Leaked Password Monitoring, Cyber Threat Intelligence, top-notch Security Testing, to Endpoint Monitoring, and more we’ve got the tools and expertise you need to keep your business and data secure. And the best part is that you can enjoy all of these benefits in a single, expert solution.
Contact us
today to learn how you can combat cybersecurity threats in your environment.






