Multi-factor authentication (MFA) has long been recognised as the best way to protect online accounts. You know it well—it requires more than just a password to log in, making it harder for hackers and other malicious actors to gain access.
But what if this extra layer of security isn’t as secure as we once thought? Are the growing vulnerabilities and limitations of MFA putting us at risk more than ever before?
From Uber to Reddit, several high-profile organisations have recently reported cases of hackers breaching MFA protection and gaining access to users' accounts. How do these breaches happen? And what can you do to protect yourselves and your accounts?
In this article, we’ll explore recent vulnerabilities in multi-factor authentication and discuss why it’s important to re-evaluate your current security measures. You’ll also learn about the different methods of MFA, and why they may leave you vulnerable. We’ll also provide some tips on how you can strengthen your security and protect yourself against malicious actors. Ready? Let's dive in!
What is Multi-Factor Authentication?
If you're looking to protect your data more effectively, then you've likely heard of "multi-factor authentication," or MFA. But what is it, exactly?
Essentially, MFA is an extra layer of security that requires multiple credentials from the user in order to access a service or account. It is an authentication process in which a user must provide additional verification factors other than their password in order to gain access to their account. These credentials can range from the answer to a security question, a token-based unique code or biometrics like facial recognition and fingerprints. MFA lets you use up to five additional factors to verify your identity before accessing personal accounts. According to
OWASP, these factors can be categorised into the following - Something You Have, Something You Know, Something You Are, and Your Location. By combining multiple factors and verifying the identity of the user for each one, MFA helps to ensure that only legitimate users are accessing sensitive areas.
MFA is being widely adopted by more and more services and platforms, to ensure data protection and reduce the risk of data breaches. In fact, Google made 2FA mandatory for
150 million users in 2021. Governments are also increasingly mandating MFA to protect critical infrastructure and data. Government applications around the world that are currently protected by MFA include - The American Login.gov service, the UK National Health Services Login app, the Czech DNS registry, and the Swedish educational system eduID.
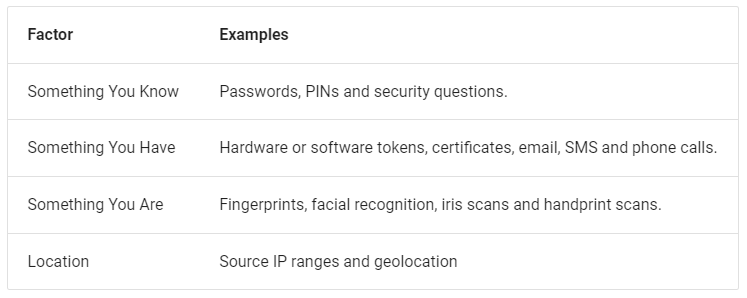
Source:OWASP
Before MFA, there was 2FA which required two verification factors to gain access to an account. But this didn't gain much traction until the mid-2000s when smartphones were first introduced. Mobile devices made it more convenient for users to provide 2FA verification factors via text messages, phone calls or app-based codes. Today, with the rise of data breaches and attacks and remote workforces, MFA is seen as one of the best ways to protect user accounts.
Multiple authentication factors help to protect your sensitive data from a wide range of threats and attacks which include:
- Phishing;
- Keyloggers;
- Brute force attacks;
- Dictionary and credential stuffing attacks;
- Ransomware;
- Man-in-the-middle attacks.
While MFA adds a vital extra layer of security to your sensitive data, it doesn't promise to eliminate all threats. Actually sometimes, MFA protection is exactly what lands you in the middle of a breach. With the growing adoption of MFA, attackers are sharpening their skills to circumvent this security measure just like they do with every new defence technique.
So do you need to be wary of implementing MFA in your organization? Maybe. But first, let's take a look at the dangers associated with MFA.
Assessing the Risks and Vulnerabilities Associated With MFA
Multi-factor authentication (MFA) is known for being the gold standard in security access. It helps protect sensitive accounts and data by requiring an extra layer of authentication such as a password, PIN, or One-Time Password (OTP). Plus, it is a critical step in a zero-trust security model, which is the ideal approach for organisations today (and we've covered previously).
But, is MFA as safe as it used to be?
It's true that there are some risks and vulnerabilities associated with MFA.
For one, OTPs are vulnerable to attack as they can be easily phished or guessed. The latest Reddit breach was caused by a phishing scam that tricked an employee into clicking a malicious link.
Hackers can build proxy websites that mimic the source website to mislead users into entering their OTPs into the wrong website. Additionally, techniques like man-in-the-browser attacks can be used to intercept communications with the result of gaining access to user accounts — a frightening reality for anyone depending on these for security.
Similarly, SMS-based codes are sometimes susceptible to mobile device hijacking. Attackers can also use SIM Switch attacks to duplicate an authorized device and steal a user's OTPs or SMS codes. In addition, there have been reports of malicious actors using brute force attacks to crack PINs. Recovery emails can also be compromised, allowing attackers to access your accounts. There could even be a security flaw in the authentication itself, since these vulnerabilities aren't entirely avoidable.
In addition to using the above-mentioned techniques to bypass MFA, bad actors can also entirely disable your organization's MFA by altering your device and configuration settings.
Another technique used by attackers to exploit MFA security is the MFA fatigue attack. This is where the attacker tricks users into accepting a security challenge that is clearly malicious by repeatedly sending push notifications to the user. The victim eventually gets tired of the endless notifications, and approves it without verifying its legitimacy. MFA fatigue let an 18-year old break into the internal systems of
Uber in September 2022.
While these risks are certainly present, MFA is still a necessary part of modern security measures and attackers often look to exploit exceptional accounts that don't have MFA implemented. For example, during the devastating
Colonial Pipeline attack was a result of a break-in via an inactive account that didn't have MFA.
So does that mean you should abandon MFA altogether? Not at all. MFA is an essential part of any modern security strategy, but it has its limitations. So, the implementation of MFA is what could make a difference in its effectiveness.
Evaluating The Current Limitations of MFA
There's no doubt that Multi-Factor Authentication (MFA) is a powerful tool when it comes to securing online services and accounts. But like any security measure, it has limitations and vulnerabilities – some more serious than others. Let's take a look at what the current limitations and vulnerabilities are with MFA, so that you can make an informed decision about how you can implement MFA in your organization.
Social Engineering
One of the biggest problems with MFA is that it can be hacked. As seen in the last section, SMS and voice-based one-time passwords (OTPs) are incredibly vulnerable to phishing attacks, as they can easily be intercepted by a malicious actor. As a result, many organisations are moving away from using SMS or voice OTPs altogether.
Weak Passwords
Another limitation of MFA is that it doesn't help if users create weak passwords for their accounts. If someone manages to guess or crack your password, then MFA won't do anything to stop them from accessing your account. This is why it's so important to create strong passwords that are difficult for attackers to guess.
E-token Security Issues
Lastly, another issue with MFA is that some e-token-based systems (such as USB keys) can suffer from security issues due to their physical nature. For example, if an attacker gets physical access to the device then they could potentially steal the data stored on it or bypass the MFA system entirely.
Vulnerabilities in Smartphones as Authentication Devices
Smartphones are now commonly used for authentication purposes, but their usage is becoming increasingly fraught with risks. Mobile device security is something that is often overlooked by both users and companies, but it's something that needs to be taken seriously. Mobile devices that aren't updated can be an easy entry point for hackers. Moreover, unintentional malware downloads can pose a significant risk when it comes to MFA done via smartphones. In addition to this, hackers have also become adept at exploiting weaknesses in the Bluetooth connections used in mobile devices such as smartphones. This means they can effectively use Bluetooth to access devices on which two-factor authentication has been enabled.
Limitations of Biometrics in Multi-Factor Authentication
Biometrics such as fingerprints are also commonly used for authentication purposes and are gaining attention as a safer mode of authentication. But even biometrics aren't a perfect solution. While they are much harder to hack, it's not impossible to work around them. One of the biggest problems with fingerprint biometrics is that it cannot be reset like passwords can be. So if a hacker steals your fingerprint and matches it to one of your devices, then they have complete access to your accounts. Moreover, biometric data collected from users can be targeted by malicious actors who attempt to spoof or steal this data for unauthorised access or credential theft purposes. In addition, biometric systems are vulnerable to attacks that use deepfakes or other artificial intelligence techniques designed to circumvent traditional security systems based on facial recognition technologies or voice recognition technologies. Lastly, there are also a number of ethical and privacy concerns surrounding biometric authentication systems.
The False Sense of Security That Comes with MFA and The Disappointments That Follow
If you believe that MFA will protect you from 99% of attacks, then you're going to be disappointed. This is a claim that has been around for years and was circulated by Google and Microsoft and was even backed by security experts. This has created a false sense of security for many organisations and they think that they are secure if they have MFA enabled. However, it is not true.
“MFA stops a very large majority of attacks.”,
says Roger Grimes, author of the book Hacking Multi-factor Authentication and Data-Driven Defence Evangelist at KnowBe4, Inc. "I think phishing-resistant MFA would stop somewhere between 15% to 30% of all attacks. That’s pretty huge. That’s beyond respectable. For that reason alone, everyone should use phishing-resistant MFA."
This goes to show that a security measure doesn't have to be 100% foolproof to be worth adopting. The fact that it can stop 30% of attacks is exactly why you should use it. So if you're implementing MFA, know exactly what it can and can't do for you.
MFA and Remote Work
The advent of remote work has revolutionized how businesses operate. However, it has also introduced a new set of challenges when it comes to implementing Multi-Factor Authentication (MFA) in remote work environments. Let's delve into the key challenges and strategies to overcome them.
Increased Remote Access
The shift to remote work has significantly increased the need for secure remote access to company systems and data. While MFA is a powerful security tool, ensuring its seamless integration into various remote work setups can be challenging. Organisations must invest in technology solutions that facilitate MFA for remote employees without compromising productivity.
Phishing and Social Engineering Risks
Remote work environments have made employees more susceptible to phishing and social engineering attacks. Attackers often target remote workers who may not have the same level of security awareness as they do in the office. MFA is a strong defence, but educating remote employees about the risks and providing regular training is essential to combat these threats effectively.
User Adoption and Training
Introducing MFA to a remote workforce requires careful consideration of user adoption. Remote employees may initially resist MFA due to perceived complexity or inconvenience. Organisations need to invest in user-friendly MFA solutions and provide comprehensive training to ensure that employees understand the importance of MFA in protecting both company and personal data.
Mobile Device Management (MDM)
Mobile devices are at the core of remote work, and securing them is crucial. Mobile Device Management (MDM) solutions are often used to enforce security policies on remote devices, including MFA. However, organisations must strike a balance between security and user privacy, as employees are using their personal devices for work. Finding the right MDM solution that aligns with company policies and employee preferences is a challenge worth addressing.
Balancing Security and Usability
Remote work environments demand a delicate balance between security and usability. While MFA enhances security, overly complex authentication processes can hinder remote employees' productivity. Organisations should continually assess and refine their MFA strategies to strike the right balance and adapt to the evolving remote work landscape.
Newer and More Closing Advanced Authentication Methods
Newer Tech as an Option
There is some hope in the form of newer technologies such as biometrics and facial recognition. Despite the challenges that these technologies face, they are still promising alternatives to other, insecure authentication methods and offer a much higher level of security. In the future we may also see the use of more such personalised authentication factors such as heartbeat, DNA, and more customisable authentication factors.
Passwordless Security
In recent times, there has been a lot of talk in the security community about moving away from passwords to passwordless security. Passwords are hard to remember, use, and manage and are seen as more of an inconvenience than a security measure. The idea is to use something that you have, and something you are in order to authenticate your identity. Examples of this include a biometric or a mobile device. Sensitive information may also be stored in a private, cryptographic key that is not accessible to anyone and can only be accessed with a public key that the user possesses. An example of this is the U2F/WebAuthn key.
Suggested Updates and Developments for MFA
Now that you know what the risks of multi-factor authentication (MFA) are, you might be wondering if there are any updates or developments that could make MFA safer. Here are a few of them:
The Use of Cryptography
Cryptography can provide an additional layer of protection for MFA by encrypting data before it is stored in a database or transmitted over a network. This will help to protect confidential information from being accessed or stolen by unauthorised parties.
Better User Interface Design
The user interface design of an MFA system should also be considered when determining its level of security. A user-friendly interface makes it easier for users to understand the process and enter their credentials accurately. This can reduce the risk of errors that could lead to potential data breaches.
Increased Security Measures
Given the growing vulnerabilities and limitations of MFA, it is important to make sure security measures are updated regularly. This includes implementing stronger passwords that cannot be cracked easily, and adding additional layers of protection whenever possible. The solution is not doing away with MFA completely; rather, making it more resilient. Utilising phishing-resistant authentication factors such as biometrics or a combination of authentication factors is one way to do this.
Additionally, contextualising user access with behavioural analytics can help to identify suspicious activity. Monitoring user access and activity in real-time can help in creating a more secure environment for organisations and users alike. Finally, security training is probably the most important security measure an organization can implement to supplement existing security measures.
It is important to ensure that your MFA solution is up-to-date with these latest developments and updates, so you can rest assured knowing your data is secure and protected at all times.
Conclusion
Whether it is a one-step process or a two-step process, multi-factor authentication is a powerful tool. It can provide an extra layer of security for your accounts, protecting them from unauthorised access. However, it is not without its vulnerabilities due to the ever-evolving technology landscape.
In the
words of Ant Allan, VP analyst at Gartner, “Locks can be picked, and doors jimmied, but would you leave your house without locking the front door?”.
The constant cat and mouse game between attackers and defenders is the essence of cybersecurity and only goes to show that as long as there are security measures, there will be attackers who learn to defeat these measures. But that does not mean that you should stop implementing security measures; it only means that you should re-evaluate the effectiveness of your security processes and tools regularly to make sure they are as up-to-date as possible.
By staying aware of the latest threats and having the right combination of security measures in place, you can make sure that your accounts stay safe and secure.
How Can Threat Intelligence Help?
At Threat Intelligence, we understand the importance of staying updated on cybersecurity trends and the need to get ahead of these trends before they start affecting your business. Our enterprise-grade solutions are designed to meet the evolving demands of your business while keeping you and your customers safe. To know more about how we can help you,
schedule a consultation with one of our cybersecurity experts today.







