By now, hopefully, you have at least started to think about what Payment Card Industry Data Security Standard (PCI DSS) compliance will look like in 2023 and beyond. The PCI SSC released PCI DSS v4.0 in 2022, and the changes coming down the pike could have a large impact on your organization - especially if you're still scrambling to maintain compliance with the current version.
In this blog post, we will take a look at some of the key changes in PCI DSS v4.0 and how you can start preparing for them.
Current State of PCI DSS Compliance
The comprehensive 2022 Verizon Payment Security Report, has recorded the following statistics for the state of PCI DSS compliance over the years:
It states that 43.4% of the assessed organizations maintained full compliance in 2020, compared to the low 27.9% in 2019. These figures are especially encouraging, given that the Payment Card Industry (PCI) Security Standards Council has continuously updated the Data Security Standard (DSS) since its inception in 2004. Enterprises seem to have embraced these updates and are concentrating their efforts on enhancing security management and governance, resulting in significant improvements in compliance. Furthermore, the report noted that the control gap has also reduced from a high 7.7% in 2019 to a low 4.0% in 2020, indicating that the surveyed organizations are moving closer to achieving full compliance with the PCI DSS. In addition, the report also indicated that the use of compensating controls has also been on the rise from 24.7% in 2019 to 30.1% in 2020. When an organization is unable to meet the real requirement mentioned under PCI DSS requirements, compensating controls are implemented.
Through the introduction of more stringent requirements, organizations have been obligated to adopt a greater level of security when dealing with customer data. In the next sections, we'll uncover what these new requirements entail and the implications of their implementation.
Overview of the 12 Core PCI DSS Requirements
The PCI DSS consists of 12 core requirements that all organizations handling credit card data must implement. These 12 core requirements serve as a foundation for organizations to create and maintain updated security protocols that follow the standards set by the PCI DSS. They are focused on ensuring that organizations have the necessary safeguards in place to protect customer data, as well as establishing processes for regularly monitoring and testing their security controls. Additionally, these requirements provide organizations with the guidance necessary to ensure that their systems, applications, and networks are secure and able to protect customer data from unauthorized access. Finally, they also ensure that personnel are trained in information security best practices and that all personnel have appropriate access to the data they need to do their jobs.
The requirements are as follows:
1. Install and maintain a firewall configuration
2. Do not use vendor-supplied defaults for system passwords and other security parameters
3. Protect stored cardholder data
4. Encrypt transmission of cardholder data across open, public, closed, and private channels
5. Protect against malware
6. Develop and maintain secure systems and applications
7. Restrict access to cardholder data
8. Assign a unique ID to each person with computer access
9. Restrict physical access to cardholder data
10. Track and monitor all access to network resources and cardholder data
11. Regularly test security systems and processes
12. Create and maintain a policy that addresses information security for all personnel
These requirements are part of 6 broader objectives which are as follows:
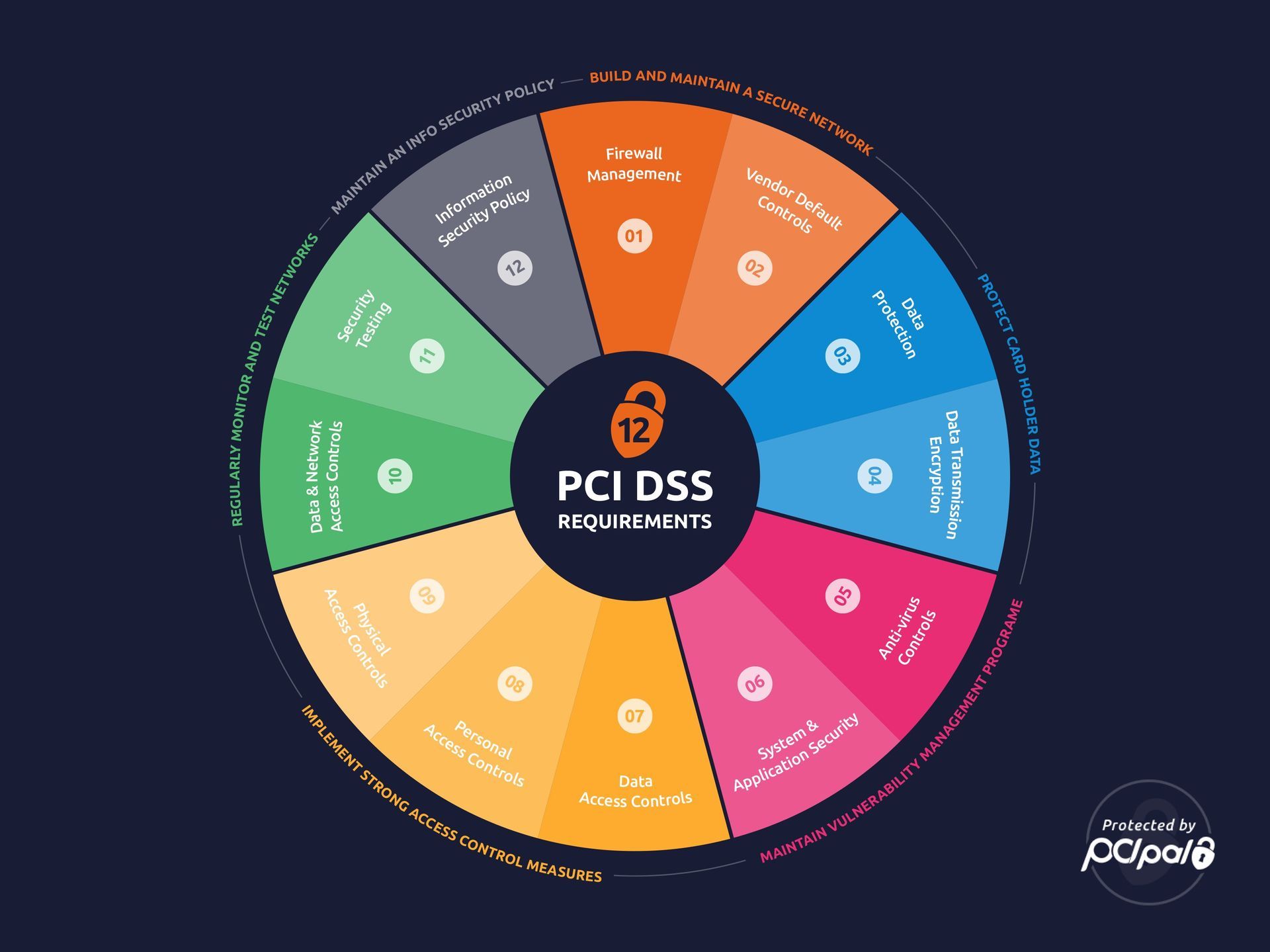
Source: PCIPal
To maintain PCI DSS compliance, organizations must not only implement these requirements but also consistently review and audit the state of their network security after implementation. The PCI DSS penetration testing process helps organizations do this by providing an objective assessment of the security of the cardholder data environment.
While the PCI DSS is not a regulatory requirement, it is a set of best practices that is essential for protecting the payment data of customers. So, it is unlikely that you will be fined by regulatory authorities for not meeting the requirements of the PCI DSS, however, it is highly likely that you will face costly penalties when you do experience a breach of sensitive cardholder data. And this is a risk that most companies cannot afford to overlook as cardholder data is one of the most valuable and sought after assets that a company can have. A single cardholder's data can be sold on the dark web for anywhere in between
$5-$150, depending on how much additional personal information is attached to it. While this figure may seem low, hackers can make lucrative amounts of money selling stolen cardholder data in bulk, and the fraud doesn't even have to be successful. Cardholder data is only anticipated to be worth more in the future as the number of cashless transactions increases. Incidents such as these can cost businesses hefty penalties and fines from payment processors. They can even lead to the termination of merchant accounts, and stop businesses from processing payments from their customers. Not to mention the damages to a company's reputation that a breach of sensitive cardholder data can cause, and the additional costs required to remediate the consequences.
Therefore, as a company or service that collects and stores cardholder data, it should be your top priority to maintain the security of this data.
Security Standards to Follow Under PCI DSS v4.0
With the release of version 4.0 of the PCI DSS in 2022, businesses have had to update their security measures to meet the new requirements. While these changes can cause some initial disruption, they also provide organizations with an important opportunity to strengthen their security systems and protect their customers’ data and transactions. Furthermore, organizations that achieve compliance with v4 of the PCI DSS will be better prepared to face future changes in the security landscape, enabling them to remain agile and adaptive. Finally, organizations that are compliant with v4 of the PCI DSS can benefit from the standardized level of security and consistency across the industry, ultimately reducing their overall risk.
Let's take a look at some of the key changes introduced as part of this update:
According to
experts, the main change in the PCI DSS v4 is the shift from a prescriptive model to a subjective one.
"The biggest change with v4 is the customized implementation. The 12 core requirements remain the same, so the update is made to improve security and provide more flexibility for security operators", says Sujith Parambath, Head of PCI Consulting Services at IT Governance.
"The new, customized approach is focused on security outcomes, risk reduction, and the intent of the control. This would be adopted by companies with mature risk management processes and robust cybersecurity programs.", he added.
This means that organizations will be able to design their own controls for each requirement, based on their current and future risk levels. This will also prove particularly useful for companies that currently use compensatory controls. The compensating controls will no longer require a business or technical justification, as long as the requirements have been satisfied.
Examples of additional flexibility include the ability to select from group, shared, and generic accounts, and targeted risk analysis that enable organizations to define frequencies for performing certain operations.
As per
PCI DSS V4 At A Glance, version 4 of the PCI DSS has also introduced additional requirements such as stronger multi-factor authentication, updated password requirements, and new e-commerce and phishing requirements to address current security concerns, and to continue to meet the changing security needs of the payment industry.
Another one of the objectives of v4 is to have a security program that's continuous and evolves over time. Under v4, entities can clearly allocate roles and responsibilities for each requirement, making it easier to adapt to changes in the environment. This version also includes guidance and instructions to help companies implement these changes, and understand how to build and maintain a robust security program. A new reporting option allows for the identification of areas for improvement and provides more transparency to report reviewers.
Finally, v4 also aims to enhance the validation methods and procedures to increase transparency and granularity of the results.
For a more detailed description of these changes, see the full version of the
PCI DSS v4 document.
For a quick rundown of the updated requirements, see below:
- Install and maintain network security controls
- Apply secure configurations to all system components
- Protect stored account data
- Protect cardholder data with strong cryptography during transmission
- Protect all systems and networks from malicious software
- Develop and maintain secure systems and software
- Restrict access to system components and cardholder data by business “need to know”
- Identify users and authenticate access to system components
- Restrict physical access to cardholder data
- Log and monitor all access to system components and cardholder data
- Test security of systems and networks regularly
- Support information security with organizational policies and programs
What to Keep in Mind While Implementing PCI DSS v4.0
As organizations move towards a more flexible approach to compliance with PCI DSS v4.0, there are a few important items to keep in mind.
First and foremost, organizations must ensure that the compensating controls they deploy meet the intent of the control. While organizations can now create their own specific controls for each requirement, it is important to remember that this approach is going to be more time-consuming. Planning audits in advance will be a necessity. Additionally, documenting the changes meticulously will be key to avoiding inconsistencies and ensuring that future risk assessments are not negatively impacted.
Regular monitoring and testing of controls should be carried out to ensure that the security measures are up-to-date and effective. Organizations should also focus on continual improvement and be ready to adjust controls as needed in order to remain compliant with the PCI DSS v4.0 requirements, and future iterations of the standard.
When budgeting for your PCI DSS compliance requirements, it is important to remember that new controls may require additional and unexpected resources. This could include additional personnel, training, or new tools or technologies that need to be implemented. Being prepared for these changes and potential costs is essential to ensure your organizational compliance. Additionally, factor in the time needed to adjust processes and procedures to meet the new requirements, as well as the cost of initially implementing the controls and the ongoing monitoring and testing required to maintain compliance.
Conclusion
The PCI DSS V4.0 was released in March 2022, and was effective immediately. If you have not already started the transition to the new standard, it is important to know that the previous version of the standard (PCI DSS v3.2.1) will expire in March 2024. Organizations have until March 2025 to transition into the latest version, after which they will be subject to the new standard during compliance assessments.
The PCI DSS v4.0 is a much needed update to the standard that brings it in line with current security concerns and best practices. While there is a lot of new information to digest, the overall goal of the standard remains the same: to protect cardholder data and reduce fraud. With the deadline for compliance fast approaching, now is the time to start familiarizing yourself with the new requirements and making the necessary changes to your security program.
How Can We Help?
At Threat Intelligence, we understand the importance of compliance and are committed to helping our clients maintain a secure environment. If you are feeling overwhelmed by the changes in the PCI DSS v4.0, or are not sure where to start, our team of compliance experts can help.
Evolve's Automated Compliance Monitoring service automatically collects and analyzes your security information, and maps it against the requirements of the PCI DSS and even regulatory standards such as HIPAA, NIST 800-53, GDPR, and ISO 27001. We can assess your current security posture and develop a roadmap to compliance that fits your budget and timeline.
Contact us today to get started.







