Penetration testing, often referred to as pen testing, involves simulating real-world cyberattacks to identify vulnerabilities and weaknesses in a system. However, just conducting pen tests isn't enough; it's crucial to measure their impact and effectiveness. That's where penetration testing metrics and key performance indicators (KPIs) come into play. That's what we're talking about in this post.
Understanding Penetration Testing Metrics: Peering into the Cybersecurity Landscape
As the cyber threat landscape evolves, penetration testing has become a crucial part of a comprehensive security strategy for modern businesses. In fact, Gartner estimates that penetration testing will be a $4.5 billion dollar industry by 2025.
Threats such as ransomware, phishing, and misconfigurations have become more sophisticated, and these threats are becoming harder to detect and remediate. Penetration testing tests your infrastructure from all angles, ensuring there's no stone unturned in your defense strategy.
Definition of Penetration Testing Metrics and Their Significance
Penetration testing metrics are quantifiable measurements that provide insights into various aspects of the testing process. They shed light on the number of vulnerabilities discovered, the accuracy of findings, the speed of remediation, and the overall security posture. These metrics act as a compass, directing security teams towards vulnerabilities that need immediate attention, allowing them to allocate resources effectively.
How Metrics Provide Insights into Vulnerabilities and Risks
In penetration testing, metrics are the clues that help investigators – the cybersecurity teams – understand the impact of vulnerabilities and the potential risks. Metrics reveal patterns, trends, and weaknesses that might have otherwise gone unnoticed.
These metrics assign severity ratings to vulnerabilities discovered, highlighting critical vulnerabilities for immediate attention. Informed by metrics, cybersecurity teams optimize resource allocation and strategy. In essence, metrics bridge technical findings and strategic decisions, empowering organizations to address vulnerabilities, fortify defenses, and navigate evolving cyber threats effectively.
Link Between Metrics and Overall Cybersecurity Posture
Picture a puzzle. Each piece represents a metric, and when these pieces come together, they form the complete picture of your organization's cybersecurity posture. Metrics act as the bridge between tactical pen testing activities and the overarching cybersecurity strategy. By assessing metrics, organizations can make informed decisions about resource allocation, technology investments, and risk management, ultimately fortifying their digital defenses.
For example, check out this scorecard from the EvolvePT pen test report:
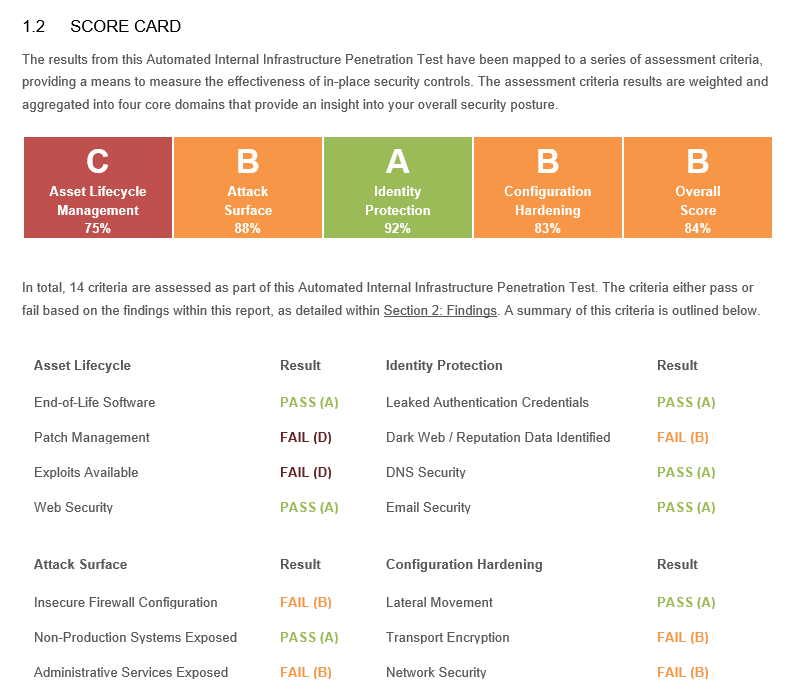
Snapshot from EvolvePT Test Report
A scorecard like this one is a visual representation of the effectiveness of existing security controls. This provides a quick and easy way for stakeholders to understand the overall security posture of an organization. It helps you understand what's currently working and what isn't so you can improve accordingly.
Key Penetration Testing Metrics: Evaluating Effectiveness
So, what are these crucial metrics that hold such significance in penetration testing? Let's dive into some of the key metrics that allow organizations to evaluate the effectiveness of their pen testing efforts.
Scope and Coverage: Measuring the Comprehensiveness of Tests
The scope and coverage metrics set the boundaries of the pen test. These metrics would include the number of systems and applications included in the pen test, the frequency of the tests, timeframe of the tests, and the testing methodology and tools.
Vulnerability Discovery Rate: Assessing How Many Vulnerabilities Are Found
Vulnerability discovery rate tells you how quickly your cybersecurity team is uncovering vulnerabilities. It measures the rate at which new vulnerabilities are discovered and reported by your pen testing team. A high discovery rate indicates that your team is adept at spotting weaknesses, whereas a low rate might warrant a closer look at your testing methodology.
False Positive Rate: Managing and Reducing False Positives
False positive rates help organizations fine-tune their testing tools and methodologies, ensuring that genuine vulnerabilities don't get lost in the noise.
In addition, using automated tools to detect vulnerabilities can help reduce the false positive rate and also identify vulnerabilities that may otherwise be overlooked.
Time-to-Remediate: Minimizing the Time Taken to Address Vulnerabilities
The longer you leave vulnerabilities unaddressed, the higher the risk of a breach. Vulnerabilities left unaddressed can also lead to performance issues, as well as data loss and downtime. Time-to-remediate metrics act as a stopwatch, urging organizations to swiftly patch vulnerabilities and minimize the window of opportunity for attackers.
Critical Vulnerabilities: Identifying and Prioritizing High-Impact Vulnerabilities
Imagine a doctor triaging patients in an emergency room. Critical vulnerabilities are the patients in dire need of immediate attention. Metrics related to critical vulnerabilities help organizations prioritize their efforts, ensuring that the most impactful vulnerabilities are dealt with promptly.
Enhancing Cybersecurity with Penetration Testing Metrics
Establishing Baselines: Setting Initial Measurement Points
An initial snapshot of your security posture provide a baseline measurement, against which future progress can be measured. By establishing baselines, organizations gain a clear understanding of their current security status and can track improvements over time. As you undertake subsequent tests, these baselines allow you to track changes and assess the effectiveness of your efforts.
Continuous Monitoring: Ongoing Assessment and Improvement
Cybersecurity is an endeavour requires constant attention. While it is impossible to attain total security, it is possible to continuously monitor and improve your security posture.
Continuous monitoring keeps an eye on metrics such as server availability, system performance, compliance, new security threats, security incidents and more. Consistently analyzing these metrics, provides real-time insights into your security posture.
Regular pen tests allow you to monitor your security posture on a regular basis and identify and address potential security gaps before they become a problem, adapt to changing threats, and maintain a strong defense posture.
Collaboration Between Teams: Coordinating Efforts for Optimal Results
Different teams within an organization – IT, security, development – play distinct roles in cybersecurity. And improving security is a collaborative effort that requires the cooperation of all teams. Pen testing results should be shared with the board and executive management, and with the development team in order to foster collaboration, ensuring that all teams work together seamlessly to address vulnerabilities and fortify defenses.
How Can We Help?
The true power of penetration testing lies not just in the tests themselves, but in the metrics that measure their impact. These metrics transform raw data into actionable insights, guiding organizations towards a fortified cybersecurity posture.
Navigating the complex world of cybersecurity is no small feat, but you're not alone on your journey. Our experts will guide you through the entire process - from establishing a baseline to to aligning objectives and fostering continuous improvement. Your security is our priority. Contact us to schedule a demo today.