In today’s competitive business landscape, organisations are under intense market pressure to develop and release applications at record pace.
Whether in the form of a new web or mobile application, or additional functionality to an existing application, delays can cost your organisation dearly. Rivals may surge ahead, achieving competitive advantages and capturing greater market share.
DevOps
teams find themselves under intense pressure from executives to roll-out applications faster than ever before. Agile methodologies are now widely embraced by DevOps teams as an efficient way to write code, build functionality and deploy applications.
However, all too often speed comes at the expense of security. For many organisations, market considerations trump security imperatives.
In the rush to the production environment, the costs associated with weak application security, or AppSec, are often overlooked. Applications with bugs are vulnerable to breaches. Confidential customer and corporate data may be compromised, resulting in significant financial and reputational costs for your organisation.
The key to secure applications is integrating strong security throughout the software development lifecycle (SDLC). With ongoing code reviews and continuous testing within an agile environment, it is possible to efficiently deploy robust applications, achieving your business objectives without comprising security.
In this blog we will explore the benefits of embracing agile methodologies, whilst ensuring AppSec becomes an integral part of the SDLC.
Waterfall vs Agile
The Waterfall Model
Before we dive into agile, it is worth taking a look at its predecessor: waterfall software development methodologies.
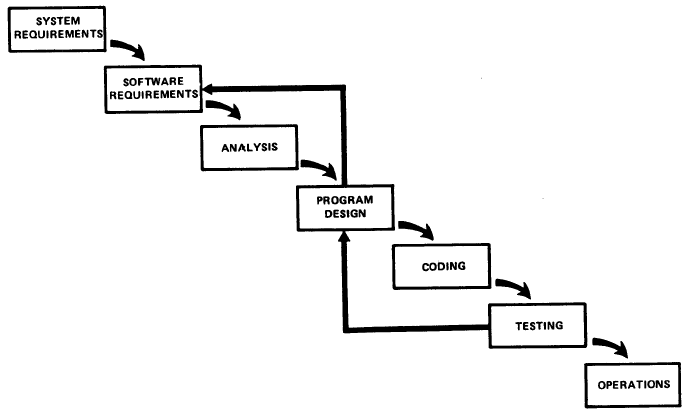
The waterfall approach to systems analysis and design was first established by Winston W. Royce in the 1970s. For many years, it was the default approach to building and deploying software. However, the waterfall method contained some significant challenges. It required developers to determine all the requirements of the project from the outset, during the System Requirements phase. This included detailed understandings of precisely what end-users needed from the application.
Once System Requirements has been established, the development process ran downhill. The completion of each stage would result in the commencement of the next stage.
A major shortcoming of the waterfall methodology was that Testing was so close to the end of the lifecycle, right before deployment.
As Royce himself understood: “I believe in this concept, but the implementation described above is risky and invites failure…The testing phase which occurs at the end of the development cycle is the first event for which timing, storage, input/output transfers, etc., are experienced as distinguished from analysed. These phenomena are not precisely analysable…If these phenomena fail to satisfy the various external constraints, then invariably a major redesign is required…The required design changes are likely to be so disruptive that the software requirements upon which the design is based, and which provides the rationale for everything are violated. Either the requirements must be modified, or a substantial change in the design is required. In effect the development process has returned to the origin and one can expect up to a 100 percent overrun in schedule and/or costs.”
In other words, after DevOps teams had invested considerable time and resources to develop software, it may be discovered that there were fundamental flaws during the Systems Requirements stage. This may necessitate a full rethink of the entire design of the application.
It should also be noted that any security testing would also be conducted at the Testing stage. This could also reveal fundamental vulnerabilities. Retroactively fixing these bugs could be costly and would likely delay the release of the end product.
A better methodology was needed. Application development had to be flexible, so that it could be adapted to suit changing circumstances and needs. Additionally, it was essential that testing not be left to the end of the process right before deployment. In particular, security testing had to be embedded throughout the SDLC.
In contrast to waterfall, agile methodologies seek to incorporate flexibility into the process. Rather than building an entire application before releasing it, agile focuses on rapidly developing, testing and deploying individual components or functionality of an application. This ensures that there is flexibility embedded within the SDLC. DevOps teams can execute redesigns as needs change or market expectations shift.
The Agile Method
Agile methodologies are also better suited to ensuring software is built securely. With functionality tested on an ongoing basis, bugs can be identified and fixed rapidly. This avoids lengthy delays and enables applications to be delivered on time and on budget.
By embracing agile development methodologies, DevOps teams can integrate security considerations throughout every stage of the SDLC. This has given rise to a new model:
DevSecOps
.
DevSecOps recognises that security cannot be an afterthought. Security is integral to the success or failure of software. Only with continuous code reviews and continuous testing of application functionality can organisations develop software that meets their business needs, including the needs of customers. Embracing a DevSecOps model demonstrates that there does not need to be any trade-off between AppSec and the efficient deployment of applications. Both can be achieved simultaneously.
Why Security Must Not be an Afterthought
Modern organisations need to consider the interests of a range of stakeholders. Customers, employees, shareholders and the broader community all expect organisations to take cyber-security seriously. Policymakers and regulators have responded to these expectations with a range of strong regulatory and privacy requirements that aim to protect private data.
Cyber-security must now be treated as a top priority. With application breaches a leading cause of cyber-attacks, it is critical that you ensure your organisation’s web and mobile applications are built robustly. The challenge for DevOps teams is that agile methodologies can see small-scale functionality deployed in timeframes of less than week. However, thorough security testing usually takes longer than this. Finding a way to integrate continuous security into agile methodologies, without unnecessarily delaying the SDLC is essential.
The best way your DevOps team can align its agile development timelines with its security imperatives is through embracing automation tools.
Tools that automate security-related tasks are essential because the more you can automate the work necessary to meet your software deployment objectives, the easier achieving strong AppSec becomes. Additionally, security tools can help reduce some of the development effort required of your DevOps team by shifting it onto the tools. This allows your DevOps team to focus on other priorities, such as building additional functionality.
It is important to remember that where security is involved, tools do not replace humans. However, tools enable scalability and speed. For example, automated tools can scan large volumes of code at a speed that humans would not be able to achieve.
How Can Threat Intelligence Help?
Threat Intelligence brings you
Evolve Automated DevOps Application Security Testing
.
This innovative solution enables your DevOps team to automate the integration of AppSec testing into the software development pipeline. You will be able to rapidly identify security vulnerabilities in applications under development, with automated reviews of every piece of code that is deployed.
Evolve Automated DevOps Application Security Testing delivers the most efficient security controls for software progressing through the development pipeline to the production environment. Not only will you achieve unprecedented efficiencies, but the security of your applications will be stronger than ever before.
With Evolve Automated DevOps Application Security Testing, you will be able to automatically orchestrate on-demand AppSec testing environments in real-time. This can even take place within your Evolve Cloud that sits inside your Evolve Security Zone. This means that there are minimal requirements for DevOps pipeline integration.
As long as your DevOps Pipeline server can execute Python code, either locally or on a remote server running Windows or Linux, you can easily integrate the Evolve Automated DevOps Application Security Testing to get up and running within minutes by adding a simple build step into your deployment pipeline.
Evolve Automated DevOps Application Security Testing has made building and deploying applications faster and more secure than ever before.
Contact us
today to learn how Threat Intelligence can help your organisation meet all your application development needs.






