Imagine you're in charge of a company's cybersecurity. How would you measure your success?
This is where cybersecurity metrics come in. Cybersecurity metrics help you track your progress in order to figure out if your current security measures are working or not. They are the key to understanding your company’s cybersecurity status and how to improve it.
In this blog, we’re going to cover what cybersecurity metrics are, and the key metrics your business should be tracking to improve its security and success.
What are Cybersecurity Metrics?
You've probably heard the term 'cybersecurity metrics' tossed around a lot in information security, but what do they actually mean? And more importantly, why should you care?
In business, a metric is a type of performance measurement or a set of indicators that are used to measure the success of an organization or project. Basically, they are a way of quantifying and measuring what you're trying to accomplish.
The best way to monitor applications, networks, or systems for cybersecurity is by using cybersecurity metrics. These metrics are used to determine the effectiveness of your current security efforts. Key cybersecurity metrics can include anything from the number of security incidents to the number your company faces on a daily, weekly, and monthly basis, the amount of data and money your business has lost as a result of these incidents, and the percentage of your systems that have been compromised by hackers.
Why are Cybersecurity Metrics Important?
You can't improve what you don't measure, and that's why cybersecurity metrics are so important. By tracking key performance indicators, you can see exactly how well your company is doing when it comes to cybersecurity.
And that's not all. These metrics can help you make informed decisions about your security posture and identify areas for improvement. They also provide a way to benchmark your organization against industry peers and compliance requirements.
What are the Key Metrics for Measuring Cybersecurity Success?
Cybersecurity Preparedness
The ability to identify, prevent, and respond to cyberthreats is known as cybersecurity preparedness. It is a critical component of any organization that needs to protect its data and systems from
cyberattacks
. Is your security team always ready to respond to an incident? Are your systems working properly and fully patched? Are you able to test your security posture on a regular basis? These are the types of questions that can help you measure your cybersecurity preparedness.
Unidentified Devices on Internal Networks
Modern networks are subjected to constant change because of the increasing number and types of devices connected to them. The rapid growth of the number of endpoints and mobile devices on corporate networks, leaves networks open to attack by those who want to gain access to sensitive data.
Intrusion Attempts and Security Incidents
As long as you are connected to the internet, you are vulnerable to network intrusions. Are you aware of the number of attempts that are made to break into your network each day? What’s the frequency of these attacks? How many of these attacks are successful? Check your logs regularly to identify any changes or trends in the number of attempts.
Mean Time to Detect (MTTD)
Mean Time to Detect or MTTD is a metric that measures the time it takes to detect a security incident, potential security threats, or other indicators of compromise. Do security threats go undetected for long periods of time in your organization? If so, how can you improve your detection capabilities?
Mean Time to Resolve (MTTR)
Mean Time to Resolve or MTTR is a metric that measures the time it takes to resolve a security incident. It is a great way to measure the effectiveness of your
incident response
capabilities. How long does it take for your incident response team to resolve an incident?
Mean Time to Contain (MTTC)
Mean Time to Contain (MTTC) is a metric that measures the time it takes to detect, address and contain the possible spread of a security incident. It is a good indicator of the efficacy of your incident management efforts. You should always work towards minimizing the time it takes to contain security threats across all your endpoints.
First Party Security Ratings
Security ratings are a useful way for you and external stakeholders to understand the security posture of your organization. They use a simple scoring system to rate the security of your organization, that can be easily understood even by non-technical stakeholders. Different security rating platforms use different scales to score security postures such as a scale from 0 to 100 or from A to F. The data-driven ratings are usually based on a number of factors that demonstrate how well your company can protect its data from breaches and security incidents.
Average Vendor Security Rating
Third-party risk assessments from a trusted source are a good way to get an outsider’s perspective on your security posture and help you understand your organization’s threat landscape better.
Patching Cadence
Patching cadence is a term that is used to refer to the frequency and quality of the updates that your organization makes to its software and operating systems. These updates are used to remediate vulnerabilities, and are an important part of your overall security posture. Cybercriminals often take advantage of the fact that computers are constantly running software and operating systems that are not properly patched. The longer it takes for your organization to make security updates, the more likely it is that your systems could be breached.
Access Management
Privilege escalation attacks abuse the user accounts that have access to systems and data they do not require. Access management is a process that ensures that only authorized users are allowed to access sensitive information, and that they can only access the information they require. Additionally, leverage zero-trust access controls and policies to monitor user activity and access to systems.
Vendor Patching Cadence
Supply chain risks are one of the top ways that cyber criminals compromise organizations’ networks and data. Vendor patching cadence indicates the patching capabilities and frequency of the third party vendors in your supply chain. Run regular risk assessments to ensure that the vendors you’re in business with are able to protect their data and meet your security requirements as well.
Mean Time For Vendors Incident Response
As already mentioned under the previous metric, attack attempts on your vendors make you a potential target for attack as well. If your vendors take too long to respond to security threats and incidents, you are more likely to fall victim to a third-party data breach.
Cybersecurity Metrics for the Board
It's not just the IT department that should be concerned with cybersecurity metrics. The board should also be tracking these numbers so they can understand the overall risk to the business. After all, the board is ultimately responsible for protecting the company's assets. Here are some metrics that the board should be tracking:
Incident Detection and Response
As covered in the previous section, if you have an incident response team and plan, you need to measure its effectiveness. Metrics including the time taken to detect, respond to and remediate a security incident give the Board a clear picture of ongoing, and pending investigations and the average time required to conduct an investigation.
Metrics for Unresolved or Open Issues
While ongoing risk assessments provide you with the necessary visibility into your network and threat landscape, it is just as important to keep track of outstanding issues that are pending from previous risk assessments, especially the ones that have high-risk findings. Are there any risks that you won’t be able to address immediately? What is the primary reason for delay? These questions can help the board to better understand where your organization is in the process of addressing threats, and provide you with the required support.
Industry Comparison
One of the most effective metrics to demonstrate your cybersecurity expertise is your performance relative to your competitors in the industry. Also known as benchmarking, this metric allows you to make valid comparisons, understand how successful your peers are, and what they’re doing differently when it comes to cybersecurity. And if you perform better than the industry average, you can use this as a competitive advantage to show your clients and stakeholders that you take data security seriously.
Cybersecurity Awareness Level
It is the Board’s responsibility to enable cybersecurity leaders to create a culture of cybersecurity awareness throughout the organization. This includes designing customized awareness programs for employees based on their roles and responsibilities so that they are able to understand the risks and threats that they are vulnerable to. The Cybersecurity Awareness Level is a helpful metric to understand the current level of awareness in your organization.
Cybersecurity Dashboards: How Can Threat Intelligence Help You?
When it comes to cybersecurity, it's essential to have a holistic view of your security posture so that you can understand what you’re trying to protect.
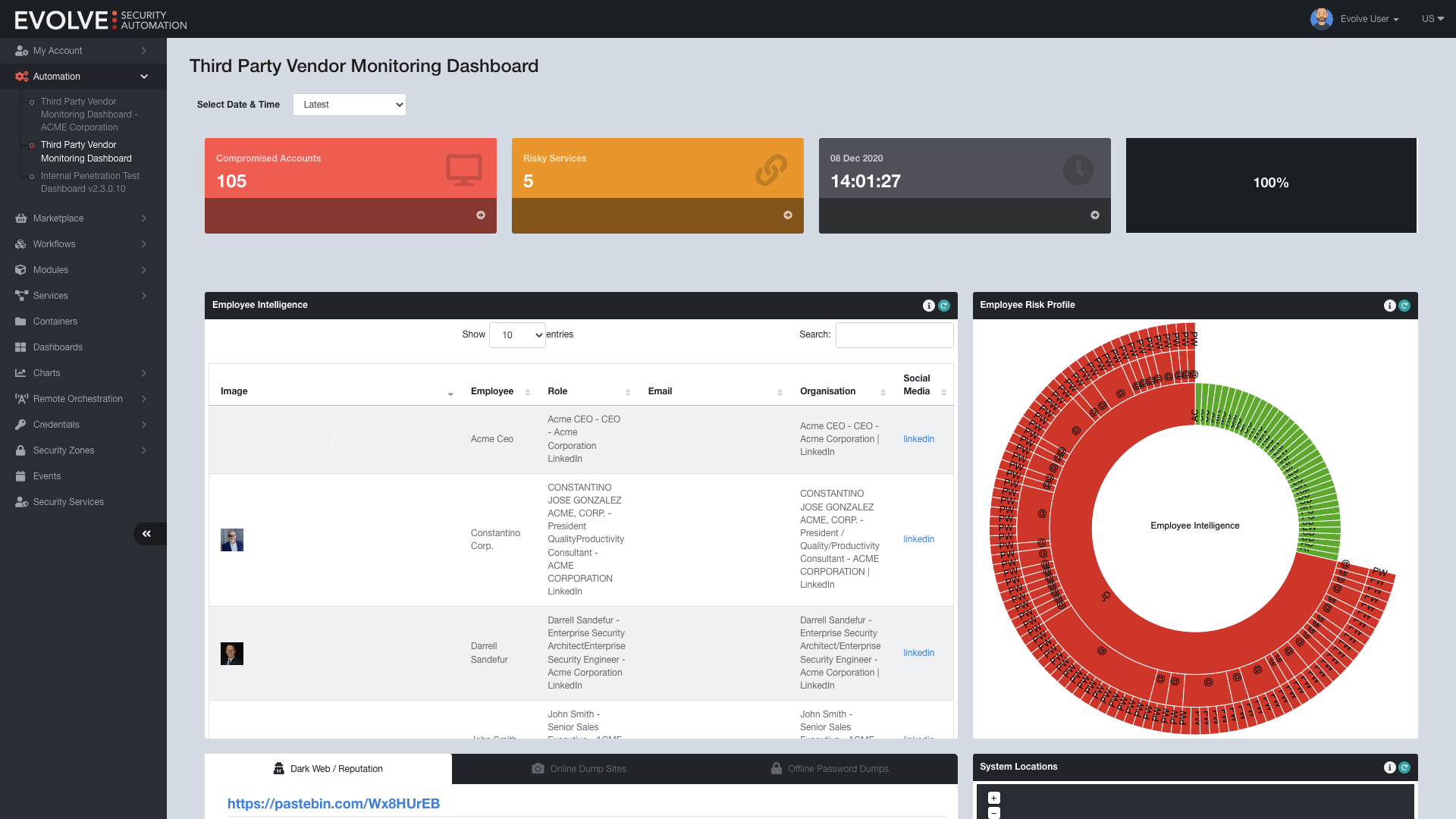
Threat Intelligence’s EvolveXDR Dashboards provide predefined visualizations for services such as - Automated Penetration Testing - Compromised Account Monitoring - DNS Sinkhole that give you a comprehensive view of your overall security. Additionally, you can explore vulnerability and compliance data in detail.
Moreover, our Managed Detection and Response service allows you to generate a report summarizing events for the previous calendar month, covering key areas such as Summary of Events, MITRE ATT&CK framework, File Integrity Monitoring, Cloud Services (such as AWS and Office 365) and Vulnerability Monitoring.
Our dashboards and reports are available in easy-to-understand formats so that you can easily visualize and share them with the Board. Check out one of our Supply Chain Monitoring dashboards in the picture below:
Conclusion
In short, cybersecurity metrics are essential because they allow you to track the security of your business and see where you need to make improvements. By measuring things like security incidents, malware infections, and data breaches, you can identify potential weak points in your security and take steps to fix them. Not only that, but cybersecurity metrics can also be used by the board to measure the effectiveness of the company's information security program and make sure that it is adequately protecting the business.
The key is to always keep the bigger picture in mind and pick the right metrics that align with your business objectives and risk appetite.
If you're not currently using cybersecurity metrics, now is the time to start.
Contact our experts
today to learn more about our affordable and easy-to-use solution.