"The only truly secure system is one that is powered off, cast in a block of concrete, and sealed in a lead-lined room with armed guards - and even then I have my doubts."
This quote by Gene Spafford, a renowned computer science professor and security expert, illustrates the difficulty of achieving perfect security. It suggests that even the most extreme measures to secure a system may not be enough to prevent all vulnerabilities and attacks.
In a world where vulnerabilities are a daily occurrence and digital assets and endpoints continue to grow, it is impossible to address every single one of them.
Vulnerability prioritization is an important step in the vulnerability management process that allows organizations to focus on the most critical security issues first. That's what we're breaking down in this blog post. Keep reading to learn more about vulnerability prioritization and how to use it to your advantage.
What is Vulnerability Prioritization?
Security vulnerabilities exist in all kinds of systems, from the smallest IoT devices to the largest cloud computing platforms. For example, hardware vulnerabilities can include flaws in the design or manufacturing of a device, such as a weakness in a system-on-a-chip (SoC) or a vulnerability in a hardware encryption module. Network devices such as routers, switches, and firewalls can have vulnerabilities in their software, which can be exploited by attackers to gain access to the network or to cause disruptions. Human processes and behavior can also create vulnerabilities. For example, social engineering attacks exploit human behavior to trick people into disclosing sensitive information or performing actions that can compromise security.
Vulnerabilities are the Achilles heel of the modern computing ecosystem. And there's no way to avoid them. It's the job of security teams to ensure that vulnerabilities don't turn into real threats that could be exploited by attackers. Security teams do this by fixing the vulnerabilities as soon as possible, by applying patches to the vulnerabilities.
However, with thousands of vulnerabilities being released every few months, it can easily feel like you're fighting a losing battle.
6,231 new vulnerabilities were reported in the 4th quarter of 2022 alone. When you multiply that number by all the assets in your organization, it's easy to see how you can end up with a backlog of vulnerabilities that's just too big to manage.
Prioritizing vulnerabilities can help you focus your efforts on the vulnerabilities that are most critical to your business. Vulnerability prioritization is the process of determining which vulnerabilities should be addressed first. It is a critical part of
vulnerability management, and it's also often one of the most challenging aspects of vulnerability management.
But how do you prioritize vulnerabilities? What's the best way to make a list of the most critical vulnerabilities? What factors do you need to consider when prioritizing vulnerabilities?
The Problem with Traditional Vulnerability Scanners
Traditional vulnerability scanners are designed to scan your network for security gaps and exposures. However, they often stop there. So, at the end of a scan, the security team is left to manually prioritize vulnerabilities on their own.
Traditional vulnerability scanners operate by examining individual network assets, such as devices and applications, to assess their susceptibility to various known threats. Once the scanner identifies vulnerabilities, it correlates them with the organization's asset inventory to determine the most vulnerable assets, using publicly available exploit databases.
By doing so, these scanners supply security teams with valuable information on existing vulnerabilities in their systems, laying the foundation for appropriate mitigation and defense measures. However, as previously mentioned, they often fall short when it comes to helping security teams prioritize the identified vulnerabilities. Consequently, teams are left with an overwhelming amount of work to manually determine which vulnerabilities should be addressed first.
Classifying vulnerabilities based on CVEs can be a useful starting point for understanding the potential impact of a vulnerability and for communicating about vulnerabilities across different organizations and tools. However, it's important to remember that CVEs are just one factor to consider when prioritizing vulnerabilities, and they may not always accurately reflect the risk that a particular vulnerability poses to a specific organization.
Traditional vulnerability scanners often rely heavily on CVE-based classification, as well as other external vulnerability databases, to identify and prioritize vulnerabilities. While these databases can be helpful for identifying known vulnerabilities and providing information about their potential impact, they may not always provide an accurate picture of the actual risk that a vulnerability poses to a specific organization.
What actually matters is not how many vulnerabilities a system has but how many exploitable vulnerabilities there are. The number of exploitable vulnerabilities is a better indicator of risk than the number of vulnerabilities.
While vulnerability scanners can be useful for detecting well-known vulnerabilities and providing a baseline level of security, they have some limitations:
- False positives: Vulnerability scanners may generate false positives, indicating that a system is vulnerable to an attack when it is not. This can lead to wasted time and resources trying to patch non-existent vulnerabilities.
- Limited coverage: Vulnerability scanners are often limited in the types of vulnerabilities they can detect. They may only detect well-known vulnerabilities or vulnerabilities that have been previously identified by the scanner vendor. This means that vulnerabilities are often missed.
- Inability to prioritize vulnerabilities: Vulnerability scanners may generate a large number of alerts, making it difficult to prioritize which vulnerabilities need to be addressed first. This can lead to inefficient use of resources and delayed response to critical vulnerabilities.
- Lack of context: Vulnerability scanners may not have enough contextual information about the systems or applications they are scanning. This can make it difficult to distinguish between false positives and real vulnerabilities or to understand the severity of a vulnerability in the context of the overall security posture.
- Inability to identify complex attacks: Vulnerability scanners may not be able to identify complex attacks that involve multiple vulnerabilities or exploits. Attackers can also evade detection by using techniques such as obfuscation, which can make it difficult for scanners to detect malicious code.
- Inadequate or overwhelming reports: Vulnerability scanners may generate reports that are either too simplistic and lack the necessary detail to address the vulnerabilities, or are too overwhelming and difficult to understand, making it challenging for security teams to prioritize and address the vulnerabilities.
- So how do you determine which vulnerabilities are exploitable? If your vulnerability scanner doesn't return accurate results, it's up to your security team to analyze the results manually. However, it's ridiculous to expect a small team of security professionals to drop everything any time a new vulnerability is discovered. This would only lead to plummeting productivity, chaos, and a waste of resources. On the other hand, it's not wise to leave these vulnerabilities unaddressed either.
Your security team either needs plenty of resources (people, money, and products) to keep up with the patching, or an easier and more efficient approach to patching.
The Need for a Risk-Based Approach
At the end of the day, you're trying to protect your organization's resources and attacks from real-world attacks. In order to do this, you need to have a full understanding of what these risks are and how they could impact your organization.
There might be 15000 vulnerabilities in your environment right now, but that doesn't mean that all of them need to be patched. Think of checking the weather forecast before you step out. If the forecast predicts rain, you might want to bring an umbrella, but if the forecast predicts sunshine, you're probably going to be just fine without it.
Similarly, if a vulnerability is not being actively exploited by attackers or poses a low risk to your organization, it doesn't need to be prioritized for patching because the risk of an attack is low or even nonexistent.
Critical and high risk vulnerabilities are the ones that attackers are actually trying to exploit. They are the ones that usually have many exploits and are actively being used in the wild by attackers. While not all of these exploits will succeed, some of them will and can be used to breach your network. These are the vulnerabilities that you should patch as soon as possible.
This approach is a risk-based approach to prioritization and is much more effective than the traditional approach of just trying to patch everything.
To learn more about the risk-based approach to vulnerability prioritization, check out this video from one of our webinars where Ty Miller, Managing Director of Threat Intelligence breaks down the basics of exploitability prioritization.
Benefits of Automated Penetration Testing for Vulnerability Prioritization
Incorporating automated pen testing into your security strategy provides a more accurate and efficient way to evaluate the risk of vulnerabilities in your environment.
Unlike a vulnerability scan that only identifies vulnerabilities, a pen test allows you to actually see how an attacker would exploit your system by trying to exploit the vulnerabilities identified by the scan. This allows you to more accurately prioritize your patching efforts based on the real-world risk of exploiting the vulnerability.
With
automated pen testing, these benefits can be achieved without any manual effort on your part, in addition to greater coverage, faster results, and reduced time to remediation.
EvolvePT is an advanced automated pen testing platform that combines vulnerability scanning and exploitation in a single tool, providing a faster, more comprehensive way to find and prioritize vulnerabilities. EvolvePT runs every exploit to see which ones are successful, giving you a clear picture of which vulnerabilities pose the greatest risk to your organization.
It doesn't just scan for vulnerabilities, it also identifies insecure business processes, weak passwords, supply chain risks, malware infections, and more. So you can rest assured that your environment is being tested deeply, and that your assets are not being overlooked.
Here's how EvolvePT compares to a traditional scanner:
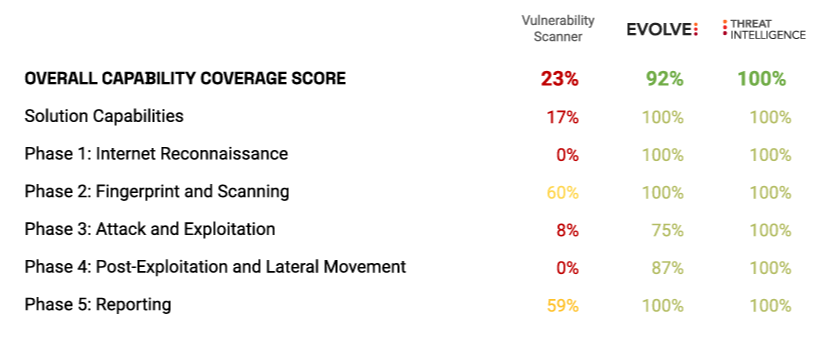
Evolve PT vs Vulnerability Scanning Comparison
Conclusion
Vulnerability prioritization is a critical aspect of effective cybersecurity, but traditional vulnerability scanners often fall short in accurately identifying and prioritizing vulnerabilities in the context of an organization's unique environment. These scanners can lead to a false sense of security, leaving organizations vulnerable to potential attacks.
To overcome these limitations, consider switching to automated penetration testing to improve your vulnerability management program. By actively attacking the infrastructure and identifying vulnerabilities that may have been missed by traditional scanners, an automated pen test can provide much more value to your organization with risk-based vulnerability prioritization, fewer false positives, and an actionable remediation guide that is tailored to your specific business environment.
If you're interested in learning more about how our automated penetration testing solution can help your organization identify and prioritize vulnerabilities, please don't hesitate to
contact us for a consultation. Our team of experts is always here to help you stay one step ahead of the hackers and protect your valuable assets.








