Sam Panicker
Technical GRC Specialist at Threat Intelligence, IRAP Assessor, ISO 27001 Lead Implementer, Certified Information Systems Security Professional (CISP), ISACA Certified in Risk and Information Systems Control (CRISC).
Anupama Mukherjee • March 7, 2024


Sam Panicker
Technical GRC Specialist at Threat Intelligence, IRAP Assessor, ISO 27001 Lead Implementer, Certified Information Systems Security Professional (CISP), ISACA Certified in Risk and Information Systems Control (CRISC).
Businesses and their security teams need to constantly keep up with regulatory assessments of their industry and other markets to be able to provide the best possible services. One such assessment is IRAP (Information Technology Risk Assessment Program). In this blog post, we're breaking down IRAP, who it applies to, and how to achieve it. This content has been created with the help of our Technical GRC Specialist, Sam Panicker
The Australian government defines the IRAP as "an independent assessment of the implementation, appropriateness, and effectiveness of a system’s security controls. It is an Australian Signals Directorate (ASD) initiative to provide high-quality information and communications technology (ICT) security assessment services to government and industry."
Tailored for businesses seeking government contracts, this assessment is a mandatory step for those aiming to offer services or products to the Australian government. By subjecting your systems to IRAP assessment, your business demonstrates its commitment to meeting the stringent security standards necessary for engaging with government entities.
The IRAP assessment is for businesses or entities that want to sell their product to the government. However, not every business that wants to sell to the government has to get an IRAP assessment. The government specifically ask for an IRAP assessment in cases where it is required to do so.
The significance of the IRAP assessment is underscored by the government's recognition of cyber and information security as a paramount national security priority. In the contemporary landscape, cyber intrusions pose tangible threats to government systems,
critical infrastructure, and broader information networks, jeopardizing Australia's national security and interests. The IRAP initiative aligns with the imperative to fortify these systems against potential vulnerabilities and ensure their resilience in the face of evolving cybersecurity challenges. By mandating this assessment for businesses engaging with government contracts, authorities emphasize the crucial role of robust cybersecurity measures in safeguarding the nation's critical assets and sensitive information. Through participation in the IRAP assessment, businesses not only navigate regulatory requirements but actively contribute to the overarching goal of enhancing
Australia's cybersecurity posture.
The Protective Security Policy Framework (PSPF) serves as a comprehensive guide for Australian Government entities, ensuring the protection of people, information, and assets worldwide. With its 16 policies, each defining core and supporting requirements, the PSPF sets the minimum security standards endorsed by the government.
Specifically tailored for IRAP assessments, the Information Security Manual (ISM) acts as a subset within the broader PSPF. The ISM provides essential questions for evaluation, outlining a cybersecurity framework for organizations to integrate into their risk management processes. Targeted at key roles such as Chief Information Security Officers (CISOs), Chief Information Officers, cybersecurity professionals, and information technology managers, the ISM represents the expert guidance of the Australian Signals Directorate (ASD) in enhancing cyber resilience within organizations. All recommendations within the ISM align with ASD's designated functions under the Intelligence Services Act 2001.
Source: Australian Signals Directorate (ASD)
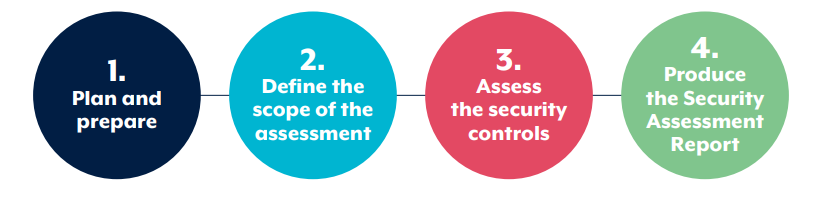
For a detailed description of the IRAP Assessment Process, please refer to the ASD’s Assessment Process Guide. Here's a quick summary of the steps:
Initiate engagement by informing ASD IRAP Administrator, and plan assessment activities, including setting milestones, defining resource access, and determining stakeholder engagement approaches.
Define the assessment scope by agreeing on the system version, security classification, and authorization boundary. Validate and document the scope, including any out-of-scope components, within the security assessment report.
Review evidence provided by the client to assess security controls. Conduct design effectiveness and operational effectiveness reviews to ensure controls are both documented and implemented. Clearly document any limitations in evidence.
Generate a comprehensive security assessment report outlining the assessment scope, effectiveness of security control implementation, identified security risks, and recommended remediation actions. Include the Security Controls Matrix (SCM) or Cloud SCM (CSCM) with assessment observations against each ISM control. Ensure deliverables adhere to ACSC IRAP Resources guidelines, avoiding misleading statements.
The IRAP assessment is a set of questions that are asked to the client to determine the strength of their security posture. IRAP assessors go through the ISM, and make sure that the company bidding for the government has fulfilled the requirements listed in the ISM.
Once these questions have been answered, the assessors find gaps in the security posture of the company, and then provide a report back to the company. The company can then choose to go back and mitigate these gaps and then re-submit their information for another assessment, or they can go ahead and bid on the project. If the government is satisfied with the report, then they will award the contract and if not, they will reject the bid. It depends on whether you meet the specific requirements of the government.
While doing an IRAP assessment, the assessors let the company know beforehand the exact version of the ISM that will be used for the assessment so that the company can prepare for the assessment accordingly.
"Typically, as assessors we're called in to do ISM Gap Assessments", explains Sam.
"An ISM Gap Assessment is a process of identifying and addressing security gaps in a company's security posture. We assess their systems, make sure everything is in scope, and set up the Cloud Controls Matrix (CCM) document for them. This takes roughly about 5 days per system."
This document is then used as a reference to do the gap analysis and fill the gaps in the company's security posture.
The actual IRAP Assessment is a process of verifying that the company has in fact implemented the controls it claims to have in place and takes about 2-3 days.
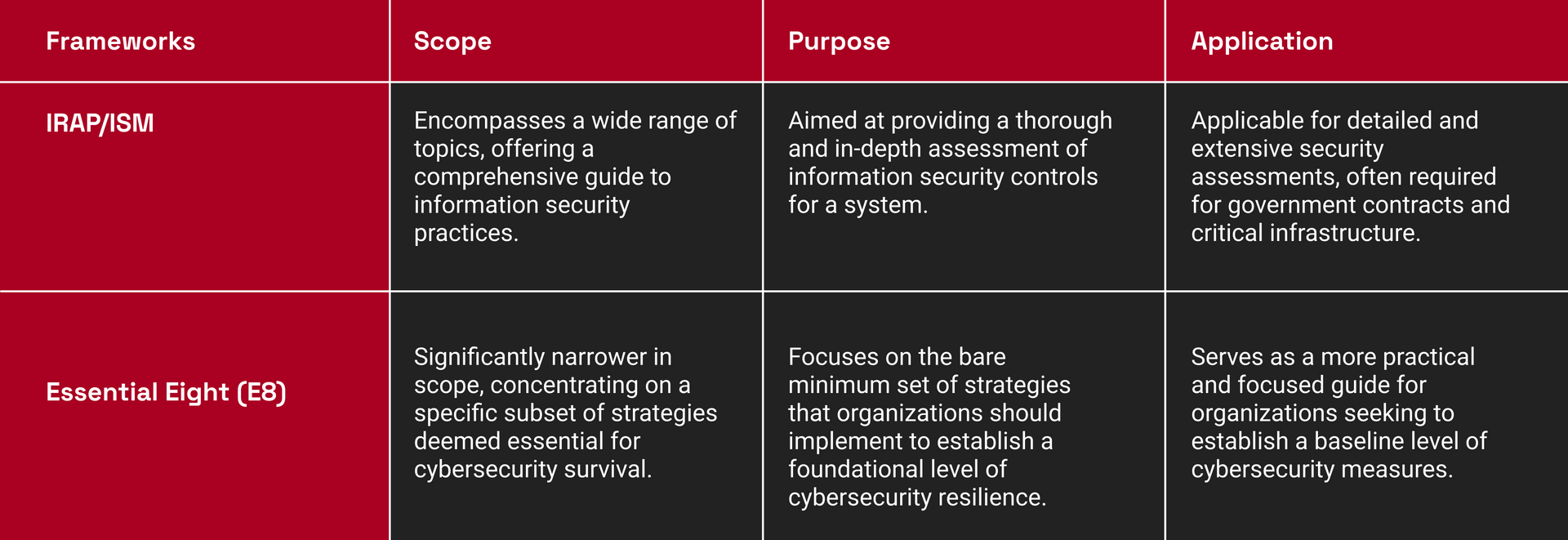
The IRAP (Information Security Registered Assessors Program) and Essential Eight (E8) represent distinct frameworks with specific focuses and scopes.
The IRAP program operates within the Information Security Manual (ISM), a comprehensive set of guidelines initiated by the Australian Signals Directorate (ASD). This program involves independent assessments conducted by registered assessors to evaluate the implementation, appropriateness, and effectiveness of security controls in a system. The ISM covers a broad spectrum of topics, reflecting a holistic approach to information security.
On the other hand, the Essential Eight (E8) is a subset of the ISM, consisting of eight key mitigation strategies. These strategies are considered the fundamental measures that organizations should implement to enhance their cybersecurity posture. Unlike the expansive coverage of the ISM, the Essential Eight provides a more focused and streamlined set of guidelines. It represents the baseline measures necessary for companies to comply with for foundational cybersecurity resilience.
If you're embarking on your IRAP assessment journey, partner with us for our comprehensive IRAP Assessment services. Our expertise ensures your systems not only align with government standards but excel in the ever-evolving digital landscape.
Our Technical GRC Specialist Mr. Sam Panicker has guided and continues to guide many organisations through the IRAP Gap Assessment process. He has over 15 years of experience in IT, including 5 years specialising in GRC and security architecture wih 2 years experience as an IRAP assessor.
He has worked with clients in industries ranging from finance to defence.
For more information on our GRC Services, take a look
here. And to book your IRAP Assessment,
schedule a call/consultation with us today.
Related Content