Cybercrime is now an industry that is worth billions of dollars. Hackers are using advanced techniques and tools involving artificial intelligence, machine learning, and automation to get around security controls and expedite the cyber attack lifecycle. In such a turbulent threat landscape, businesses can no longer afford to sit and wait around for an attack to hit them. Instead, the only way for businesses to remain secure is to strengthen their defenses by anticipating emerging cyberthreats of the future.
In this blog, we'll look at how to create a proactive cybersecurity strategy that will keep you one step ahead of cyberthreats at all times.
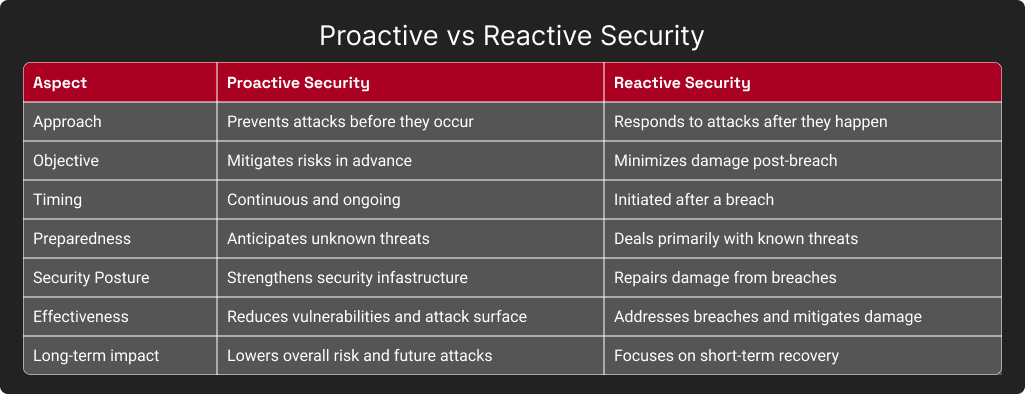
What is Proactive Cybersecurity?
Being proactive means to anticipate future problems, needs, or changes, and take action appropriately. In the context of cybersecurity, proactive implies just the same. Proactive cybersecurity is everything you do before an attack takes place. Most of the time, companies don’t properly prepare themselves for potential cyber incidents until it’s too late. In contrast to responding to an attack after it has already occurred, these security measures focus on preventing attacks in the first place.
Essentially, proactive cybersecurity entails all the processes and activities that are carried out on a regular basis within an organization to prevent risks. Examples of proactive cybersecurity measures can include identifying and patching vulnerabilities in the network infrastructure, preventing data and security breaches, and regularly evaluating the strength of your security posture. Continue reading to learn more about proactive security strategies you can implement to improve your overall security.
Proactive vs Reactive Cybersecurity
Most businesses will likely have in place security controls such as firewalls, antivirus software, and threat monitoring software. If and when an attack occurs, they will have a plan to systematically deal with its consequences. Each team member has a designated role to play during an attack and well-documented guidelines help them identify what went wrong and how to avoid such incidents in the future.
This is what a typical reactive approach to security looks like. The security team reacts or responds to the breach, and attempts to repair the damage the attacker has caused.
Reactive cybersecurity is the exact opposite of proactive security. It is everything you do after an attack occurs. Sure, if your goal is only to prevent known threats, this approach might suffice. However, acting responsively can leave you vulnerable to a host of other threats such as zero-day vulnerabilities, advanced persistent threats (APTs), and many more complex cyber attack vectors that can damage your business.
Reactive Cybersecurity Tactics
Reactive cyber security methods are focused on preventing 'known' malware from infiltrating your network and compromising your business databases. When a virus manages to slip through the cracks, these measures help you to track down the perpetrators. Following are a few examples of such reactive security measures
Firewalls
Firewalls secure your network and information by managing network traffic, blocking unsolicited incoming network traffic, and verifying access by scanning network traffic for malicious elements such as hackers and malware. However, firewalls are ineffective at protecting against viruses, trojan horses, spyware, and malware. There are too many ways to encode binary files for network transfer, as well as too many different architectures and viruses, and it is not possible for a firewall to try to find them all. Generally, firewalls cannot prevent data-driven attacks, which involve sending or copying something to an internal host, where it is then downloaded and executed.
Anti-Malware Software
Just like firewalls, the anti-virus software will protect against most known threats. But with such a significant percentage of unknown malware variants being discovered every day, it is unlikely that an antivirus will protect devices from all of them. Moreover, attacks such as social media malware are almost always undetectable. Anti-malware software cannot protect against these hidden threats, as well as a variety of other threats such as browser-based attacks, phishing, and spam.
Password Protection
‘123456’, ‘qwerty’, and ‘password’ happen to be some of the most common passwords used in 2022. Cybercriminals leverage people’s lax attitude towards passwords to launch attacks, steal credentials, and for credential stuffing. Furthermore, password protection without Multi-Factor Authentication does not provide sufficient protection because attackers will still be able to access user accounts. Passwords are also not enough to prevent account takeovers and phishing attacks.
Spam Filters
While spam filters are necessary and do a great job at keeping spam emails out of your inbox, spammers understand what is flagged when emails are filtered and how to adapt to better fool the system and get past your spam detection.
Disaster Recovery Plan
Cybersecurity disaster recovery is specifically concerned with disasters caused by cyber threats such as DDoS attacks or data breaches. A typical recovery plan will outline the steps your company must take to stop losses, eliminate the threat, and move forward without endangering the company's future. However, it is advisable to invest in prevention at least as much as, if not more, in recovery.
Proactive Cybersecurity Tactics
Benefits of Proactive Cybersecurity
Proactive cybersecurity actually works. The proactive security market was worth USD 20.81 million in 2020, and it is expected to grow to
USD 45.67 million
by 2026.
Reports
have shown that aggressive security policies and a proactive approach have helped companies confidently navigate through and prevent cyberattacks such as phishing attempts. Some more benefits of proactive cybersecurity include:
Prevent Threats and Disruptions from the Get-Go
By taking a more proactive, forward-thinking approach from the start, companies can address and mitigate future disruptions and cyberthreats. Working actively to prevent threats helps you gain complete control over your cybersecurity strategy. This helps you prioritize your risks and address them accordingly.
Simplify Reactive Security
By identifying vulnerabilities early on, and preparing for the worst-case scenarios ahead of time, you’re able to take action rapidly and decisively during a cyber incident. While proactive measures help to actively prevent breaches, reactive measures strike if and when a breach occurs.
Reduces Clean-Up Costs
Some data breaches have resulted in billions of dollars in losses. Without aggressive security policies in place, businesses can expect exorbitant clean-up costs including fines, settlement, and business loss, in the event of a data breach. Strategic planning helps spot and patch vulnerabilities before attackers strike, as well as significantly lowers the additional costs incurred during and after a breach.
Stay on Top of Emerging Threats
A highly adaptable cyber security strategy can help you keep up with the latest developments in the threat landscape. When you don't have to devote all of your resources and time to responding to attacks, you have the opportunity to learn about cybercriminals' attack tactics.
Maintain Compliance
A proactive security strategy helps you understand your organization’s risk thoroughly. When you address these risks appropriately, you can rest assured that you will pass compliance checks any time.
Build Customer Trust
Proactively securing your business shows that you take security seriously. Going above and beyond to protect your customers’ data enables you to gain their trust and build a safe and transparent relationship with them.
Now that we’ve understood the phases in SDLC, let’s take a look at the SDLC methodologies. Here are some models to consider:
Threat Hunting
The goal of threat hunting is to identify unknown threats that may be lurking within an organization's systems. Threat hunting utilizes threat indicators and
threat intelligence
as a starting point or hypothesis for a hunt. Threat hunting, as opposed to reactive methods, is a proactive approach to identifying previously unknown or existing, unpatched threats within an organization's network. An effective threat hunt can also identify threats that have not yet been discovered in the wild.
Penetration Testing
Penetration testing
is a great preventative security measure. This method involves hiring skilled and experienced hackers to intentionally try to breach your company's defenses. This process identifies holes and security gaps in the network and helps to build a stronger overall security posture.
Proactive Network and Endpoint Monitoring
Proactive monitoring implies that your company is constantly looking for impending threats. This method enables IT teams to identify and resolve issues that could have a significant impact on their business, if left unchecked.
Cybersecurity Awareness Training
Recent statistics show that 95% of all data breaches were caused due to employee negligence. This implies that your employees can be your biggest strength or your biggest liability when it comes to the security of your business. For a truly proactive approach, create and implement effective cybersecurity training for your employees to ensure that your teams operate in line with the appropriate security standards.
Security Patch Management
Security Patch Management is a crucial component of proactive cybersecurity tactics, ensuring that your organization's software and systems are fortified against known vulnerabilities. By regularly applying updates and patches to software, operating systems, and applications, you create a robust defense mechanism that guards against potential exploits.
User and Entity Behavior Analytics (UEBA)
A proactive cybersecurity strategy called User and Entity Behavior Analytics (UEBA) focuses on tracking and examining the actions of users and entities on your network. Any variations or abnormalities can be promptly detected by setting up a baseline of typical behavior, pointing to possible security risks or malevolent activity.
Common Misconceptions About Proactive Cybersecurity
There are several common misconceptions about proactive cybersecurity. Here are some of the most prevalent ones:
Proactive Cybersecurity is too Expensive and Time-Consuming
While there may be some upfront costs associated with implementing proactive cybersecurity measures, the cost of a cybersecurity breach can be much greater. In addition, proactive measures can actually save time in the long run by preventing security incidents and minimizing the time and resources required to respond to a breach.
Proactive Cybersecurity is Only for Large Companies
Many small and medium-sized companies make the mistake of believing that they're too small to be targeted by cybercrime when in fact, they are just as vulnerable as larger organizations. Any organization can be a target for cybercriminals, regardless of its size or industry. Small businesses may even be seen as easier targets because they may have fewer security measures in place.
Proactive Cybersecurity is Only Necessary for Highly Regulated Industries
Another common misconception is that proactive cybersecurity is only necessary for highly regulated industries such as finance, healthcare, or government. While these industries do have specific regulations and compliance requirements around cybersecurity, all businesses are at risk of cyber threats and need to be proactive in protecting their data and systems.
Proactive Cybersecurity is a One-Time Effort
Some people believe that once they have implemented security measures, they no longer need to worry about cybersecurity. However, cybersecurity is an ongoing process, and threats are constantly evolving. It is important to regularly review and update security measures to stay ahead of potential threats.
Implementing Proactive Cybersecurity
Here's how you can implement proactive cybersecurity in your enterprise:
- Conduct a risk assessment: Start by identifying your organization's assets, such as hardware, software, and data, and assess the potential risks to each asset. This will help you prioritize which assets need the most protection and determine what security measures are needed.
- Develop a cybersecurity policy: Develop a policy that outlines your organization's approach to cybersecurity. This should include procedures for protecting sensitive data, guidelines for employee behavior, and protocols for responding to security incidents.
- Implement employee training: Employees are often the weakest link in an organization's cybersecurity defenses, so it's important to provide them with regular training on how to identify and respond to potential threats.
- Use multi-factor authentication: Require multi-factor authentication for all employees and contractors who access your organization's systems and data. This can include something the user knows, such as a password, and something they have, such as a physical token or mobile device.
- Regularly update software and systems: Ensure that all software and systems are regularly updated with the latest security patches and upgrades. This will help protect against known vulnerabilities that can be exploited by cybercriminals.
- Implement network monitoring: Use tools such as intrusion detection and prevention systems to monitor your organization's network for unusual activity. This can help you identify and respond to potential security incidents in real-time.
- Backup data regularly: Regularly backup all critical data, both on-site and off-site, in case of a security incident or system failure.
- Conduct regular security audits: Conduct regular security audits to identify potential vulnerabilities and areas for improvement in your organization's cybersecurity defenses.
- Hire an expert: A cybersecurity expert or team can bring a wealth of knowledge and experience to the table, help identify potential vulnerabilities and risks, and provide guidance on best practices and industry standards. Additionally, an external expert can provide an objective perspective on your organization's cybersecurity posture and help identify areas for improvement.
Lessons Learned: Real-Life Examples of Data Breaches Caused by Inadequate Cybersecurity Measures
- Equifax: In 2017, Equifax, one of the largest credit reporting agencies in the United States, suffered a massive data breach that exposed the personal information of over 147 million people. The breach occurred due to a vulnerability in the company's web application software, which had not been patched in a timely manner.
- Target: In 2013, Target, a major retailer in the United States, suffered a data breach that exposed the credit and debit card information of over 40 million customers. The breach occurred due to a vulnerability in the company's payment processing system, which had not been adequately secured.
- Yahoo: In 2013 and 2014, Yahoo suffered two massive data breaches that exposed the personal information of over one billion users. The breaches occurred due to a failure to implement adequate security measures and a lack of proactive cybersecurity practices.
- Marriott International: In 2018, Marriott International suffered a data breach that exposed the personal information of over 500 million customers. The breach occurred due to a vulnerability in the company's Starwood reservation database, which had not been detected and addressed in a timely manner.
These breaches are cautionary tales that demonstrate the importance of taking a proactive approach to cybersecurity. They illustrate the devastating consequences that can result from a failure to adequately protect sensitive information and address vulnerabilities in a timely manner.
While no organization can guarantee complete protection against cyber threats, a proactive approach to cybersecurity can help reduce the likelihood of a breach and mitigate the impact if one does occur.
The Future of Proactive Cybersecurity
The future of proactive cybersecurity looks promising, with advancements in artificial intelligence (AI) and machine learning (ML) playing an increasingly important role in identifying and addressing potential threats. AI-based cybersecurity systems can already detect and prevent cyber-attacks with higher accuracy and speed than traditional systems and the use of ML can improve threat detection and incident response in real-time, reducing the time to detect and remediate a security breach. With continued investment and innovation, the future of proactive cybersecurity is likely to see continued advancements in AI, ML, as well as greater collaboration between industry, academia, and government to address emerging threats and challenges.
Artificial Intelligence and Machine Learning in Proactive Cybersecurity
AI and ML are already being used to automate security tasks such as threat detection, incident response, and vulnerability scanning. As the technology continues to evolve, AI and ML will likely play an even greater role in proactive cybersecurity.
Predictive Analytics
One area where AI and ML are already being used is in the development of predictive analytics. Predictive analytics uses machine learning algorithms to analyze large amounts of data and identify patterns that can indicate potential security threats. By using predictive analytics, organizations can identify potential threats before they occur and take proactive measures to mitigate the risk.
Autonomous Security Systems
Another area where AI and ML are likely to play a big role in shaping the future of proactive cybersecurity is in the development of autonomous security systems. These systems use AI and ML algorithms to continuously monitor and respond to potential security threats without human intervention. Autonomous security systems are able to learn from past incidents and adapt to new threats, making them more effective at preventing cyber attacks.
Detecting Emerging Threats
Finally, AI and ML are also being used to develop more advanced cybersecurity tools and technologies. For example, AI and ML algorithms can be used to identify new and emerging threats, analyze malware behavior, and detect phishing attacks. These tools can help organizations stay one step ahead of cybercriminals and better protect their systems and data.
The Final Word: Reactive or Proactive Cybersecurity?
A common misconception in cybersecurity is that if you've never encountered a threat, you're unlikely to encounter it in the future. Or that you only need to prepare for the threats that seem most probable. Unfortunately, that is not how breaches and cyberattacks work.
While handling the aftermath of a cyber incident is important, that cannot be the focus of your cybersecurity strategy. Creating a proactive cybersecurity strategy ensures that the organization does not depend only on reactive security measures. A proactive defense strategy, when combined with reactive security, supplements the reactive security measures to reduce overall risk to the organization. This integrated approach is the most effective when it comes to securing your data and networks.
How Can Threat Intelligence Help?
In a constantly evolving risk landscape, cybercriminals know that you’ve got the tools to protect yourself from common attack methods. They know that in order to infiltrate your network, they need to launch attacks you’ve never seen before.
If you’re looking to secure your organization from the relentless cyberthreats of today, we’ve got you covered. Threat Intelligence’s
Evolve
suite has a range of innovative products and services that are designed to enhance your security posture at scale. The Evolve platform goes beyond just security automation and gives you a 360-degree view of your security posture and risk landscape, enabling you to better protect your business and customers. Our comprehensive set of proactive cybersecurity tools and services range from threat hunting and threat intelligence, supply chain monitoring, leaked password monitoring, DNS sinkholing, external and internal penetration testing, and compliance monitoring. You can also rely on our expert security team to handle all your security needs with our managed security services and expert security consulting.
To learn more about how you can take control of your cybersecurity strategy and actively breach-proof your business,
schedule a demo/consultation
with one of our specialists, or visit www.threatintelligence.com to find out how our solutions can help you.






