In an ever-evolving threat landscape, security managers face a continuous battle against a relentless tide of sophisticated cyber threats. Add multiple security solutions and an understaffed security team to the mix, and you've got the perfect recipe for chaos.
In this dynamic digital realm, where threats lurk around every corner, your need for an agile and efficient incident response process is paramount.
In this blog post, we will highlight the need for automation in your incident response and its direct correlation to the pain points experienced by security professionals. We'll also uncover how SOAR platforms emerge as a game-changer, augmenting your incident response capabilities and providing a holistic solution that empowers your security team to tackle threats with unwavering precision.
The Incident Response Lifecycle
NIST defines a security incident as "A violation or imminent threat of violation of computer security policies, acceptable use policies, or standard security practices."
And incident response as "The mitigation of violations of security policies and recommended practices."
Incident response is a necessity for any organization that wants to maintain its security posture and protect its sensitive data. A typical incident response lifecycle is as follows:
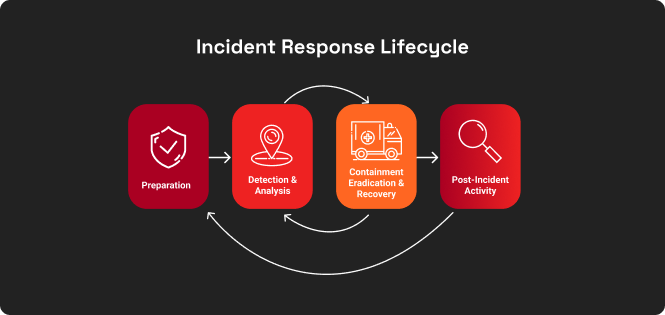
Incident Response Lifecycle
Preparation Phase
As the name suggests, the preparation phase is all about preparing for security incidents before they actually happen. This would include collecting all the data required to detect incidents, creating a playbook to respond to them, and making sure you've got the right security controls in place to detect and prevent incidents. For instance, you might face a denial of service attack that renders your website inaccessible or a malware infection that steals your data. The preparation phase is about defining the different types of security incidents you could face and then definining the process to deal with each one.
Identification Phase
The identification or detection phase is when you find out that there's been a security incident. This could be a leaked password, a malware infection, a data breach, etc. During this phase, data is collected and analyzed to confirm that an incident has taken place. Not all alerts are indicators of security incidents.
Containment Phase
The containment phase is all about making sure that the breach or incident doesn't spread any further. This is done by isolating the affected systems in order to cut off access to the larger network. Containing an incident as quickly as possible can make all the difference between a minor breach and a devastating one.
Eradication Phase
Once the incident is contained, the focus shifts to the eradication phase. This phase involves removing the root cause of the incident or the attacker, eliminating any malicious presence or vulnerabilities that allowed the breach to occur. It may include activities such as removing malware, patching system vulnerabilities, and repairing or reconfiguring affected systems. Eradication aims to ensure that all traces of the incident are eliminated, minimizing the risk of recurring incidents or reinfection.
Recovery Phase
Following the eradication phase, the recovery phase begins. This phase focuses on restoring normal operations and resuming business functions. It involves validating the integrity of systems, data, and applications affected by the incident and implementing remediation measures to bring them back to a secure state. Recovery efforts may include restoring data from backups, reconfiguring systems, and verifying that security controls are effectively reinstated. Additionally, this phase may involve communication with stakeholders, such as customers, partners, and regulatory bodies, to provide updates on the incident, any potential impact, and the steps taken for recovery.
Lessons Learnt
This phase is about going back and reviewing the incident to see what happened and why. This is when you learn what you could've done better and what you can do to prevent a similar incident from happening in the future.
Typically, eradication and recovery are a bit more of manual processes than the other phases of the incident lifecycle. This is because it requires manual intervention such as digital forensics, data recovery, and restoration. So, the first 3 phases of the incident lifecycle are what can really make or break your incident response. The sooner you are able to detect and contain the incident, the better your chances of preventing it from turning into something much worse.
Challenges Faced by Security Managers
There are many aspects of the incident response process that can be frustrating for IT security managers to deal with. Here are a few of the most common challenges:
Detection and Alert Overload
Managing a multitude of security tools and systems can result in a high volume of alerts and notifications. It becomes overwhelming to sift through the noise and identify genuine security incidents amidst false positives and irrelevant alerts. The challenge lies in efficiently prioritizing and responding to critical incidents while avoiding alert fatigue.
Complexity of Security Operations
Today, security managers need to manage multiple security solutions from multiple vendors, each with their own unique processes, to protect against the barrage of modern threats. Security teams require a solution that can integrate these solutions for the common goal of incident response can significantly simplify the incident response process.
Manual and Time-Consuming Processes
Traditional incident response often relies heavily on manual processes, which can be time-consuming and prone to human error. From incident identification and investigation to containment and eradication, the manual execution of these tasks can delay response times and hinder the ability to swiftly mitigate the impact of security incidents.
Evidence Gathering and Post-Incident Analysis
When responding to a security incident, it is essential to collect the right evidence to confirm the occurrence of a breach, identify the extent of the compromise, and support subsequent actions and investigations. However, many security professionals often struggle with determining what evidence needs to be collected and ensuring its integrity.
"Most security professionals don't know what evidence needs to be collected", says Ty Miller, Managing Director at Threat Intelligence.
Once an incident is resolved, conducting a thorough post-incident analysis to understand the root cause and implement preventive measures is crucial. However, the lack of dedicated tools and processes for post-incident analysis can hinder the ability to gain insights, identify systemic issues, and implement necessary improvements for future incident prevention.
SOAR As a Solution for Automating Incident Response
SOAR platforms are comprehensive solutions that integrate security tools, technologies, and processes to orchestrate and automate incident response activities. They provide a centralized command center that allows security teams to manage incidents efficiently, from detection to resolution. With their advanced features, SOAR platforms enable organizations to streamline workflows, improve response times, and enhance collaboration among security stakeholders.
Key Capabilities for Incident Response Automation:
SOAR platforms offer a range of essential capabilities to automate incident response effectively. These include:
- Automated Workflows: SOAR platforms enable the creation of predefined workflows that automate routine tasks and actions. By automating repetitive processes, incident response teams can focus on critical tasks and respond swiftly to emerging threats.
- Integration with Security Tools: SOAR platforms seamlessly integrate with existing security tools, such as SIEM (Security Information and Event Management) systems, threat intelligence platforms, and vulnerability scanners. This integration allows for real-time data aggregation, correlation, and analysis, enabling faster and more accurate incident detection and response.
- Intelligent Alert Triage and Prioritization: SOAR platforms leverage machine learning and artificial intelligence algorithms to analyze and triage alerts based on severity, relevance, and potential impact. This capability helps incident response teams prioritize their efforts, ensuring that critical incidents receive immediate attention.
- Playbook-driven Response: SOAR platforms enable the creation and execution of incident response playbooks. These playbooks contain predefined response actions and procedures tailored to specific incident types. By following standardized playbooks, security teams can ensure consistent and effective incident handling.
- Case Management and Collaboration: SOAR platforms provide a centralized case management system that facilitates collaboration among incident response team members. It allows for information sharing, task assignment, and communication, enabling efficient coordination and knowledge transfer during incident response.
Why Automate Incident Response?
Security incidents can leave a company vulnerable to a myriad of risks, ranging from data breaches, compromised systems, business disruption, to brand damage, loss of customer trust, and more. And in a time when cyberattacks occur every 11 seconds, it is imperative that organizations have a well-defined incident response process that can contain an incident as quickly as possible.
Companies that contained an incident within 30 days saved more than
$1 million, compared to companies that took more than 30 days to do so. This goes to show that delayed response is not an option when it comes to protecting your business from cyber threats.
But with the challenges that come with an ever-growing attack surface, limited resources, and complex solutions, incident response can be a daunting task for a single security team.
Gone are the days of relying solely on manual, time-consuming incident response methods. The transformative force that is the key to effective incident response is automation. Automation comes with remarkable capabilities that can help address the challenges security teams face and equip them to navigate the incident response process efficiently.
Benefits of Automating Incident Response with SOAR Platforms
Improved Efficiency and Response Times
Automating incident response with SOAR platforms significantly improves the efficiency and response times of security teams. By leveraging automation, repetitive and manual tasks can be streamlined, allowing security analysts to focus on critical activities that require human intervention. Automated processes enable faster identification, triage, and containment of security incidents, even in the face of the increasing frequency and sophistication of attacks. This improved efficiency ensures that security teams can respond swiftly and effectively, minimizing the impact of incidents and reducing the overall mean time to respond (MTTR).
Consistency and Standardization of Incident Handling
SOAR platforms bring consistency and standardization to incident handling processes. They enable the creation and enforcement of predefined playbooks or workflows that outline the steps to be followed for different types of incidents. By automating these workflows, SOAR platforms ensure that incident response activities are executed consistently and according to best practices. This consistency reduces the risk of human error, ensures a structured approach to incident response, and facilitates knowledge sharing among team members.
Enhanced Collaboration and Communication
SOAR platforms promote enhanced collaboration and communication among security teams and stakeholders. These platforms provide centralized visibility and facilitate seamless communication channels, enabling effective coordination and information sharing during incident response activities. Security analysts can collaborate in real-time, share insights, and work together to analyze and respond to incidents. This collaborative environment fosters cross-team cooperation, enables faster decision-making, and enhances the overall effectiveness of incident response efforts.
Integration with Existing Security Tools
SOAR platforms integrate with existing security tools and technologies, creating a unified and orchestrated security ecosystem. By connecting and leveraging the capabilities of different security solutions, SOAR platforms provide a holistic view of the security landscape. This integration allows for streamlined data sharing, automation of response actions, and the ability to leverage existing security investments effectively. It eliminates silos, reduces manual effort, and enables security teams to leverage the full potential of their security infrastructure for comprehensive incident detection, response, and mitigation.
Best Practices for Implementing SOAR
Implementing a Security Orchestration, Automation, and Response (SOAR) solution requires careful planning and execution. Consider the following best practices to maximize the benefits of SOAR and ensure a successful implementation:
Establish Clear Goals
Before implementing a SOAR solution, it is crucial to establish clear goals and objectives. Define what you aim to achieve through automation and orchestration, such as improving incident response times, reducing manual efforts, or enhancing collaboration. Clear goals provide a roadmap for implementation and help set realistic expectations for the outcomes.
Set Realistic Expectations
It is important to set realistic expectations about the capabilities and limitations of the SOAR solution. Understand the scope of automation and the areas where manual intervention may still be required.
Resource Allocation and Staff Training
Assign dedicated personnel responsible for managing and maintaining the SOAR platform. Depending on the capabilities of the SOAR solution, the use cases and functionality it supports, and the skill sets of the team members may vary.
Continuously Monitor and Optimize
Once you've set up the SOAR solution, you need to ensure that it is being used effectively. The best way to do this is to continuously monitor it and optimize it based on the results you want to achieve. Leverage the insights gained from monitoring to fine-tune automation workflows, refine playbooks, and enhance overall incident response processes.
Beyond Incident Detection and Response
When you're evaluating SOAR solutions, be sure to consider solutions that can automate more than just the detection and response processes. Automation is the key to a successful, modern-day security program. Look for additional automation capabilities such as vulnerability management, dashboards, and XDR. By incorporating these capabilities into a comprehensive SOAR offering, you can streamline your security operations and reduce the complexity of managing multiple tools.
The Future of SOAR
With evolving threats and growing complexity, the drawbacks of traditional SOAR are becoming increasingly apparent. While traditional SOAR platforms have made great strides in integrating security tools and automating workflows, they don't have the capability to deploy additional security capabilities to protect against new attack vectors.
When asked about the future of SOAR and what an ideal SOAR platform must be able to do, Ty said - "The next generation of SOAR must be able to deploy security capabilities, not just integrate [existing tools].
Automation is typically what SOAR platforms do. They're doing integration to automate the flows of activities within an environement. But they tend to be limited to incident response because that was always the focus of SOAR.
"Orchestration in SOAR stands for deploying security capabilities and building something. But SOAR platforms don't tend to build things, they just integrate solutions that already exist." he continued.
In the face of ever-evolving cyber threats, organizations require a dynamic and agile approach to incident response. Evolve rises to this challenge by empowering security teams to orchestrate and automate their incident response processes seamlessly. Unlike conventional platforms that focus solely on integrating existing security solutions, Evolve goes a step further by providing the capability to deploy new security capabilities as well. It is this unique feature that positions Evolve as the future of SOAR, unlocking a world of possibilities for security professionals. Instead of being just another tool in your security stack, Evolve is designed to be the platform for all your security needs.
"SOAR platforms actually need to cover the entire cyber kill-chain - which is your threats, attacks, and security breaches." Ty added.
With Evolve, you get the benefit of integration across your security tools as well as the ability to build and deploy your own custom security capabilities - ranging from Leaked Password Monitoring, Cyber Threat Intelligence, Penetration Testing for detecting threats exploitable systems and XDR, Incident Response, DNS Sinkole for preventing security breaches.
Conclusion
In conclusion, automating incident response with SOAR not only streamlines data sharing and reduces manual effort but also enhances collaboration and communication among security teams. It enables organizations to leverage the full potential of their security infrastructure for comprehensive incident detection, response, and mitigation.
And with a next-generation SOAR platform like Evolve, you can automate your incident response and much more, and protect your digital environement with confidence.
Schedule a demo with one of our experts today to see how we can help.







