As the world becomes more interconnected than ever before, the threat of cybersecurity breaches looms large. In this context, real-time network monitoring has emerged as a vital tool in maintaining the integrity of computer systems. The first step in protecting against these threats is to gain an accurate picture of what is happening on the network at any given time. Real-time monitoring allows for this by providing continuous updates on network activity.
Network Monitoring Explained
Network monitoring has undergone significant advancements throughout its history, evolving alongside the rapid growth of computer networks and the increasing complexity of cyber threats. In the early days of networking, basic monitoring tools focused on measuring network performance and uptime, primarily using simple protocols like ICMP ping. As networks expanded, more sophisticated monitoring solutions emerged, allowing administrators to track bandwidth utilisation, identify network bottlenecks, and troubleshoot connectivity issues.
With the rise of cyber attacks and the need for proactive security measures, network monitoring has evolved to include security-focused capabilities. Intrusion Detection Systems (IDS) emerged to detect malicious activities by analysing network traffic patterns and identifying suspicious behaviour. Over time, Intrusion Prevention Systems (IPS) were developed to not only detect but also block or mitigate security threats in real-time.
Today, network security monitoring has become a critical component of comprehensive cybersecurity strategies. It encompasses real-time visibility, threat detection, performance optimisation, and compliance adherence. As networks continue to evolve, network monitoring will undoubtedly continue to advance, embracing emerging technologies and techniques to address the ever-changing landscape of cyber threats and network complexities.
Network Monitoring vs Network Security Monitoring
Before diving into the intricacies of real-time network monitoring, let's take a moment to familiarize ourselves with the two main types of network monitoring and what they're all about. We're breaking it down in this section.
Network monitoring is the process of tracking, observing, and managing all the components and activities of a network. It provides a high-level overview of everything that goes on in the network, from traffic flow, performance to hardware configuration.
What is the need for this kind of monitoring? It ensures that the network is operating at its optimal level at all times, and that its resources are being used efficiently. It basically keeps a check on the network's health and helps identify any potential issues before they snowball into an outage or an overload of resources.
Network security monitoring on the other hand is the process of keeping track of threats and vulnerabilities that might affect the security of a network. Also known as Information Security Continuous Monitoring (ISCM), NIST describes it as "Maintaining an up-to-date view of information security risks across an organization". It helps organisations identify weaknesses in their network so that they can take the necessary steps to fix them.
This process can involve a number of different techniques, from external threat detection, regular vulnerability scans, and internal audits for compliance purposes to strengthen the security of a network.
In this blog post, we're talking about real-time network monitoring which includes assessing the overall security of a network, detecting threats, and spotting weaknesses.
Network Monitoring Explained
Real-time network monitoring plays a pivotal role in effective cybersecurity and proactive threat management. It empowers organizations to swiftly detect and respond to security incidents, mitigating the potential impact of attacks and unauthorized activities.
Real-time monitoring tools provide immediate visibility into network traffic, devices, and applications, enabling security teams to promptly identify anomalies, suspicious behavior, and potential breaches. Through continuous data collection and analysis in real-time, organizations gain the advantage of staying ahead of cyber threats, swiftly mitigating risks, and preventing further compromise. Real-time network monitoring enhances incident response capabilities, facilitates timely decision-making, and upholds the integrity, availability, and confidentiality of critical network resources.
Top Features of Real-Time Monitoring Tools
According to
Solutions Review, these are the features that every real-time monitoring tool should have:
- Real-time monitoring for immediate detection of suspicious activities;
- Traffic analysis to identify anomalies and unusual communication patterns;
- Intrusion detection and prevention capabilities to alert and mitigate security breaches;
- Asset discovery and inventory to track network devices and detect unauthorised devices;
- Vulnerability scanning to identify weaknesses and report on network vulnerabilities;
- Log management and analysis for detecting suspicious activities and tracking user behaviour;
- Alerting system for real-time notifications of critical events and security incidents;
- Detailed reporting and analytics on network performance, security incidents, and compliance;
- Compliance monitoring for tracking and reporting on industry standards;
- Scalability and flexibility to accommodate network size, growth, and diverse infrastructure;
- User-friendly interface with clear visualisations, dashboards, and customisable reports.
Implementing a Network Monitoring Strategy: Best Practices
NIST outlines a set of best practices for developing an ISCM program, the gist of which has been summarised below:
Define a Network Security Monitoring Strategy
Develop a clear strategy that aligns with your organization's structure, business processes, and information systems. Regularly track security metrics and evaluate the effectiveness of your security controls to make informed decisions and ensure effective monitoring.
Establish an ISCM Program
Create a comprehensive program that aligns with your ISCM strategy. The program should provide the necessary information for risk-based decisions and maintain operations within established risk tolerances. This includes detecting anomalies, gaining visibility into assets, understanding threats, assessing control effectiveness, and monitoring security status and compliance.
Monitor and Assess Regularly
Determine appropriate frequencies for security status monitoring and control assessments. Move towards continuous monitoring and ongoing assessments rather than relying on one-time assessments. Assign assessment frequencies for each control and monitoring frequencies for each metric, including assessing the effectiveness of security controls.
Implement Monitoring and Assessment Controls
Implement your ISCM program in line with your strategy, covering all types of security controls and monitoring their effectiveness. Automate the process where possible and choose suitable tools and methodologies for accurate and current security-related information.
Analyse the Data and Find the Risks
Analyse the collected security-related data, considering risk tolerances and potential impacts. Share analysed reports with organisational officials, who should review them carefully, considering risks and mitigation options. Document the rationale for decisions and how risks will be resolved based on organisational policies.
Respond to and Mitigate Threats
Take appropriate actions based on the analyzed data. This may involve mitigating risks, accepting certain risks, avoiding/rejecting risks, or transferring risks. Responses may include adjusting security policies, requesting additional information, modifying metrics, implementing new controls, or conducting in-depth security analysis.
Review and Update
Regularly review and update your ISCM program to adapt to changing needs. Ensure the strategy, assessments, metrics, and monitoring frequencies align with your organization's risk tolerance and support informed decision-making. Identify areas for improvement and enhance organisational insight into security posture.
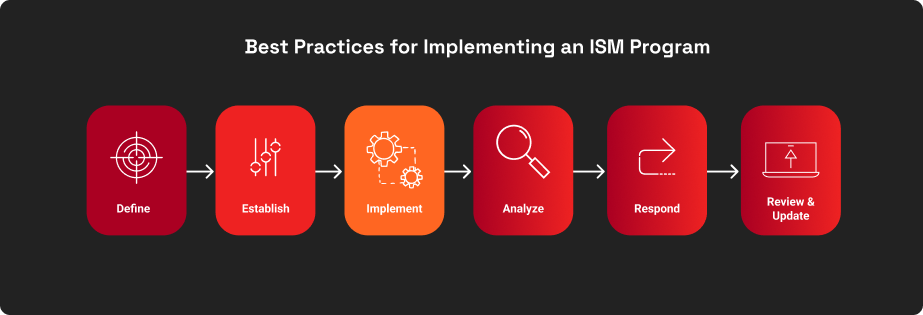
Source: NIST
The Future of Real-Time Network Monitoring
In the coming years, networks will continue to evolve with the increasing adoption of technologies like cloud computing, IoT devices, and 5G connectivity. This evolution will bring about more complex and dynamic network environments, presenting new challenges for monitoring and securing these networks.
However, the future of network monitoring holds promise through the use of automation and AI.
According to our director Ty Miller "Where AI will come in is automating all of the grunt work around the SOC so that the AI analyses the data to make decisions and then automatically responds to contain the breach."
This would not only speed up the detection and response process but also improve breach containment and recovery times.
Ty further highlights, "The challenges will always be integrations with all of the specific technologies within the company for their specific configuration."
While AI and automation can significantly enhance network monitoring capabilities, there are still critical aspects that require human expertise and context.
"AI may struggle to determine the criticality of systems and data to the business, making human input essential in guiding the decision-making process.", explains Ty.
Conclusion
As the internet and connected devices become more ubiquitous and essential to deliver high-quality and reliable services, the need for a more secure and resilient network infrastructure will become even more critical.
With the right strategies, tools, and processes in place, you can build a network that is reliable and secure, and can adapt to changing business needs.
EvolveXDR integrates seamlessly with your existing infrastructure, unifies multiple security solutions, integrates and correlates data from multiple sources, including endpoints, network, and cloud, to analyze network data and generate real-time security alerts and automated response actions. With our Security Operations Center (SOC) in action, we confirm suspicious activities, conduct in-depth investigations into surrounding events, and provide conclusive evidence of potential malicious activity. Our Digital Forensics and Incident Response (DFIR) team then swiftly steps in to contain any breaches.
Ready to experience the power of Evolve's network monitoring capabilities?
Schedule a demo today and see firsthand how we can safeguard your network infrastructure.







