Social engineering is the art of manipulating people so they give up confidential information. It has become an increasingly popular tactic used by cybercriminals to bypass technical controls and exploit human vulnerabilities.
According to Kevin Mitnick, a former hacker, "you can't go to Windows Update and get a patch for stupidity."
So, how do you deal with human errors?
That's what we're going to talk about in this blog post. Social engineering penetration testing is a great way to find the human vulnerabilities in your network. Read on to learn more about how it works and why it's important.
The Human Element
Picture this: a single click on a malicious email attachment, and a seemingly impenetrable fortress of digital defenses crumbles like a house of cards. It's a sobering reminder of the immense power that lies within human vulnerabilities and the potential consequences of a momentary lapse in judgment.
Social engineering was reported as the #1 top attack type in 2022. Yes, you read that right. Despite all the advanced technology and sophisticated security measures, it's the fallibility of human beings that often becomes the chink in the armor, allowing for catastrophic accidents to occur.
In today's interconnected world, where information flows freely and digital interactions are the norm, the risks associated with human error have become even more pronounced. From inadvertently sharing sensitive data on social media to falling prey to persuasive phishing attempts, we humans often find ourselves at the center of a delicate balancing act between convenience and security.
Consider the infamous data breaches that have rocked even the largest organizations - Google, Facebook, Uber, Microsoft, and even the United States government. Behind the headlines and monetary losses, there's a common thread: human involvement. Whether it's an employee inadvertently revealing their login credentials or an unsuspecting individual plugging in a malicious USB drive found in the parking lot, it's the human element that often opens the door for cybercriminals to strike.
Understanding Social Engineering Penetration Testing
You've heard of penetration testing before. It is a type of security testing where an ethical hacker or a pen tester attempts to break into a computer system or network by exploiting vulnerabilities. It's all about finding weak spots that could be exploited by malicious hackers.
Social engineering penetration testing is a type of penetration test that focuses on human vulnerabilities. In this unique approach, the focus shifts to the vulnerabilities found within human nature itself. It is a technique that uses social engineering tactics to attempt to gain access to a system or network. These tactics could include phishing, using stolen credentials, USB drops, pretexting, impersonation, and much more. They exploit our curiosity, trust, and willingness to help others. And by doing so, they expose potential weaknesses within our organization's human infrastructure, ultimately strengthening our defenses against real-world threats.
The social engineering cycle represents the iterative process that social engineers follow to plan, execute, and refine their attacks. It consists of several interconnected stages that form a continuous loop of assessment, adaptation, and improvement.
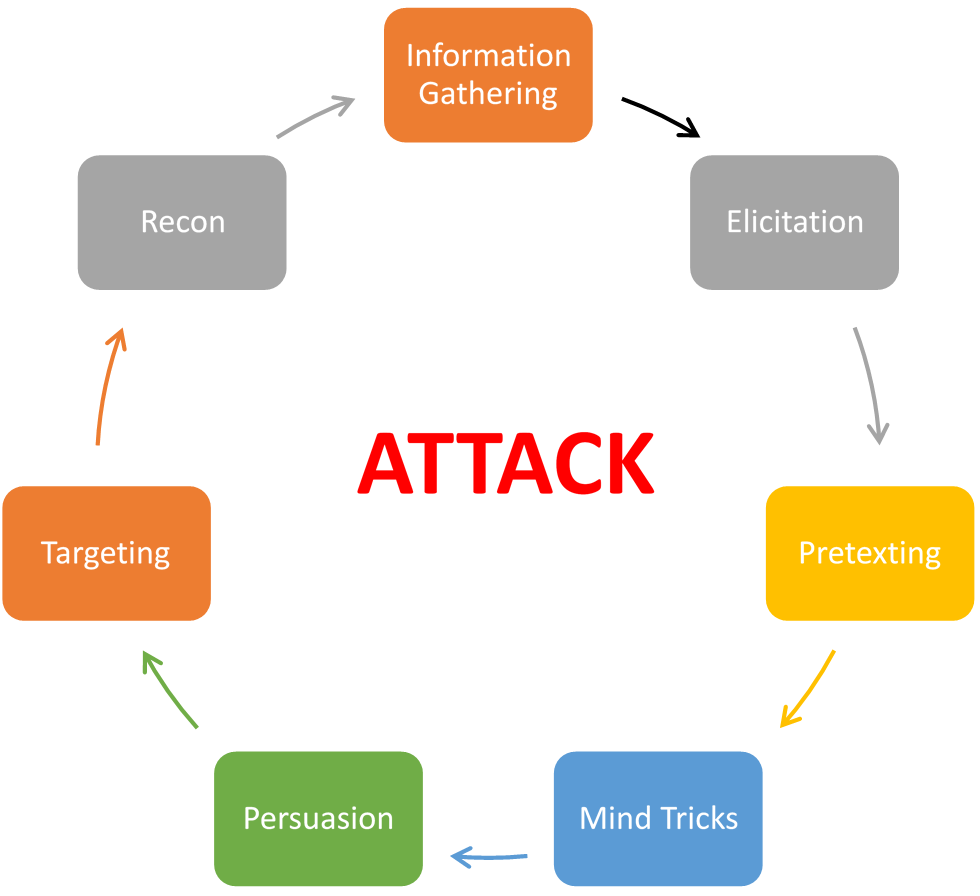
Source: Packt
The steps involved in a social engineering penetration test closely align with the stages of the social engineering cycle. While the specific methodologies and techniques may vary, the overall approach remains consistent. Here is a brief overview of the steps:
- Reconnaissance: Gather high-level information about the target organization, employees, and infrastructure.
- Information Gathering: Conduct detailed research and collect specific information about the organization, employees, systems, and potential attack vectors.
- Target Selection: Identify specific targets within the organization based on the gathered information.
- Pretexting and Planning: Develop a convincing pretext and carefully plan the social engineering attack.
- Attack Execution: Employ various tactics like phishing, impersonation, or pretexting to deceive and manipulate targets.
- Exploitation and Access: Exploit vulnerabilities exposed during the attack to gain unauthorized access or sensitive information.
- Documentation: Collect and document data, including the methods used, information obtained, and any observations or insights gained during the engagement.
- Reporting and Analysis: Compile a detailed report that outlines findings, vulnerabilities, and recommendations.
- Remediation and Follow-up: Address identified vulnerabilities and implement necessary measures for improvement.
When it comes to conducting social engineering penetration tests, testers have a wide array of open-source tools at their disposal. These tools offer various functionalities and attack vectors to simulate real-world social engineering attacks, helping organizations identify vulnerabilities and enhance their security posture. Here are a few notable examples:
- The Social Engineer Toolkit (SET): The Social Engineer Toolkit, commonly known as SET, is a comprehensive open-source tool designed specifically for social engineering penetration tests. It provides a diverse range of attack vectors, including spear phishing, credential harvesting, website cloning, and more. With its intuitive interface and support for multiple platforms, SET has gained popularity among security professionals.
- GoPhish: GoPhish is an open-source phishing framework that enables testers to simulate phishing attacks and assess an organization's susceptibility to such threats. It offers customizable email templates, tracking capabilities, and detailed reporting features to analyze user interactions and gauge the effectiveness of security awareness programs.
- Maltego: Maltego is a powerful open-source intelligence (OSINT) tool that facilitates the gathering and analysis of information about individuals, organizations, or networks. Testers can leverage Maltego to map relationships, identify potential attack vectors, and conduct reconnaissance for social engineering campaigns. It assists in uncovering valuable information from publicly available sources, aiding in the identification of vulnerabilities and potential targets.
- The Browser Exploitation Framework (BeEF): The Browser Exploitation Framework, known as BeEF, focuses on exploiting vulnerabilities in web browsers. This open-source tool allows testers to assess and manipulate browser behavior, gather information about targeted systems, and launch various social engineering attacks, such as clickjacking and cross-site scripting (XSS). BeEF provides a platform for understanding and mitigating browser-based security risks.
These open-source tools serve as valuable resources for social engineering penetration testers, offering flexibility, customization, and extensive capabilities.
Benefits of Social Engineering Penetration Testing
Social engineering pen testing can provide some significant benefits when it comes to testing the security of your organization. Some of the key benefits include:
- Identifying Vulnerabilities: Social engineering pen tests help uncover vulnerabilities within an organization's human factor. By simulating real-world attacks, organizations can identify weaknesses and gaps in their security controls related to human behavior and decision-making processes.
- Measuring Security Awareness: These tests provide insights into the level of security awareness among employees. By observing their responses to social engineering tactics, organizations can assess the effectiveness of their security training programs and identify areas for improvement.
- Raising Employee Awareness: Social engineering pen tests serve as eye-opening experiences for employees, highlighting the potential risks associated with social engineering attacks. It helps to create a culture of vigilance and empowers employees to be more cautious and proactive in recognizing and reporting suspicious activities.
- Mitigating Risks: By proactively identifying vulnerabilities, organizations can take necessary measures to mitigate risks and strengthen their security posture. This may include implementing additional security controls, enhancing policies and procedures, or conducting targeted training programs to address specific areas of concern.
- Improving Incident Response: Social engineering pen tests provide valuable insights into an organization's incident response capabilities. By testing how employees respond to simulated attacks, organizations can identify areas where their incident response plans may need refinement and enhance their ability to detect and respond to real-world social engineering incidents.
- Compliance and Regulations: Many industries and regulatory frameworks require organizations to demonstrate their commitment to security and protect sensitive data. Social engineering pen tests can help organizations meet compliance requirements by identifying vulnerabilities and taking proactive measures to mitigate risks.
- Building Stakeholder Confidence: Conducting social engineering pen tests help organizations demonstrate their commitment to maintaining a robust security posture. This can enhance stakeholder confidence, including customers, partners, and investors, as they see proactive efforts to protect their data and privacy.
- Cost-Effective Risk Management: Identifying and addressing vulnerabilities through social engineering pen tests can help organizations avoid potential financial losses and reputational damage that could result from successful social engineering attacks. It offers a cost-effective approach to risk management by preventing incidents before they occur.
Preventing Social Engineering Attacks
Shockingly, over 80% of successful data breaches involve some form of social engineering. Whether it's cleverly crafted phishing emails or convincing impersonations, attackers exploit our innate vulnerabilities. But here's the key: prevention is within our grasp.
While it may be impossible to completely eradicate the risk, we can equip ourselves to recognize and resist manipulation. Here are some steps to take:
- Provide regular security awareness training for your employees.
- Enforce strong password practices
- Implement multi-factor authentication (MFA)
- Follow the principle of least privilege.
- Establish and test an incident response plan specific to social engineering incidents.
- Encourage the use of secure communication channels
- Conduct regular security assessments, including penetration tests, to identify vulnerabilities.
- Implement security monitoring systems, update and patch systems regularly, and validate their effectiveness through penetration testing.
Conducting social engineering penetration tests can be a great way to detect misconfigurations in your systems, identify knowledge gaps in your employees' security awareness, expose weaknesses in your incident response plan, and validate the effectiveness of your security monitoring system.
The Threat Intelligence Approach
At Threat Intelligence, we understand the criticality of securing your infrastructure before malicious actors can exploit vulnerabilities. Our comprehensive Penetration Testing Services combine cutting-edge security automation with the expertise of our highly experienced team. With over 20 years of penetration testing experience, we have successfully tested and protected over 1000 customers across the globe.
When you partner with us, you gain access to a certified team of Pentesters who specialize in identifying and addressing both external and internal threats. Our Principal Security Consultants, who not only lead advanced penetration testing training at renowned Black Hat conferences but also contribute to industry-leading security standards as part of the Open Web Application Security Project (OWASP) International Board.
Combining manual expertise with EvolvePT's capabilities, we streamline engagements, increasing coverage and delivering higher-quality outcomes. We will not only pinpoint vulnerabilities but also guide you on how to fix them effectively.
Test and fortify your defenses with our team's in-depth knowledge and extensive experience.
Book a consultation today and see how we can help.
Conclusion
But let's not place blame solely on human error. After all, we are only human, and mistakes are part of our nature. The key lies in understanding and addressing these vulnerabilities head-on. By recognizing the potential risks and empowering individuals through education and awareness, we can transform the human element from a liability into an asset—a crucial line of defense against cyber threats.
This is where social engineering penetration testing comes into play. By simulating real-world scenarios and employing ingenious tactics, you can proactively assess your organization's vulnerabilities and arm your employees with the knowledge and skills to recognize and thwart potential attacks. It's about building a human firewall that is as resilient as any technical barrier.
So, let's embrace the human element, not as a weakness to be exploited, but as a powerful force that can be harnessed and fortified. Through comprehensive security strategies and a deep understanding of our inherent fallibilities, we can minimize the risks posed by human error and create a safer digital landscape for all.







